Google Chrome Bug Lets Sites Silently Overwrite System Clipboard ContentA "major" security issue in the Google Chrome web browser, as well as Chromium-based alternatives, could allow...
Month: September 2022
Stop Worrying About Passwords Forever
Stop Worrying About Passwords ForeverSo far 2022 confirms that passwords are not dead yet. Neither will they be anytime soon. Even though Microsoft and Apple are...
The Ultimate Security Blind Spot You Don’t Know You Have
The Ultimate Security Blind Spot You Don't Know You HaveHow much time do developers spend actually writing code? According to recent studies, developers spend more time...
Warning: PyPI Feature Executes Code Automatically After Python Package Download
Warning: PyPI Feature Executes Code Automatically After Python Package DownloadIn another finding that could expose developers to increased risk of a supply chain attack, it has...
Apple Releases Update for iOS 12 to Patch Exploited Vulnerability
Apple Releases Update for iOS 12 to Patch Exploited VulnerabilityThe flaw would allow the processing of maliciously crafted web content and arbitrary code executionLeer másThe flaw...
Google Releases Urgent Chrome Update to Patch New Zero-Day Vulnerability
Google Releases Urgent Chrome Update to Patch New Zero-Day VulnerabilityGoogle on Friday shipped emergency fixes to address a security vulnerability in the Chrome web browser that...
BSides Vancouver 2022 – Vivek Ponnada’s ‘OT: Air-Gap Is A Myth And Cloud Is Here To Stay!’
BSides Vancouver 2022 – Vivek Ponnada’s ‘OT: Air-Gap Is A Myth And Cloud Is Here To Stay!’Our sincere thanks to BSides Vancouver for publishing their outstanding...
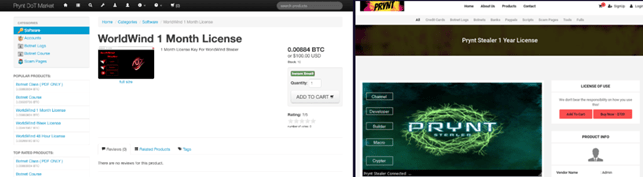
Prynt Stealer Contains a Backdoor to Steal Victims’ Data Stolen by Other Cybercriminals
Prynt Stealer Contains a Backdoor to Steal Victims' Data Stolen by Other CybercriminalsResearchers discovered a private Telegram channel-based backdoor in the information stealing malware, dubbed Prynt...
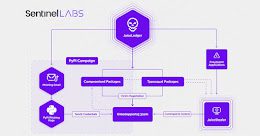
JuiceLedger Hackers Behind the Recent Phishing Attacks Against PyPI Users
JuiceLedger Hackers Behind the Recent Phishing Attacks Against PyPI UsersMore details have emerged about the operators behind the first-known phishing campaign specifically aimed at the Python Package Index...
Samsung Admits Data Breach that Exposed Details of Some U.S. Customers
Samsung Admits Data Breach that Exposed Details of Some U.S. CustomersSouth Korean chaebol Samsung on Friday said it experienced a cybersecurity incident that resulted in the...
Log4Shell is the worst security issue of the decade: what you should do
Log4Shell is the worst security issue of the decade: what you should doLast week, we discussed the Log4Shell and other Log4j-related vulnerabilities, implications, and recommended mitigation...
Ragnar Locker Ransomware Targets Energy Sector, Cybereason Suggests
Ragnar Locker Ransomware Targets Energy Sector, Cybereason SuggestsThe malware can also check if specific products are installed, particularly security softwareLeer másThe malware can also check if...
Peter Eckersley, co-creator of Let’s Encrypt, dies at just 43
Peter Eckersley, co-creator of Let’s Encrypt, dies at just 43This site, like millions of others, has a certificate from Let's Encrypt. Farewell, Peter Eckersley, PhD, who...
S3 Ep98: The LastPass saga – should we stop using password managers? [Audio + Text]
S3 Ep98: The LastPass saga – should we stop using password managers? [Audio + Text]Latest episode - listen now!Leer másNaked SecurityLatest episode - listen now!
Source Code of Over 1800 Android and iOS Apps Gives Access to AWS Credentials
Source Code of Over 1800 Android and iOS Apps Gives Access to AWS CredentialsRoughly 50% of all the apps analyzed were seen using the same AWS...
Chile and Montenegro Floored by Ransomware
Chile and Montenegro Floored by RansomwareGovernments reveal system compromise in separate incidentsLeer másGovernments reveal system compromise in separate incidents
NATO Countries Hit With Unprecedented Cyber Attacks
NATO Countries Hit With Unprecedented Cyber AttacksMontenegro, Estonia and new NATO applicant Finland are just three of the countries being hit hard by sophisticated cyber attacks....
UK Government Releases New AI Security Guidance
UK Government Releases New AI Security GuidanceNew principles set to take on adversarial machine learningLeer másNew principles set to take on adversarial machine learning
CISA, NSA and npm Release Software Supply Chain Guidance
CISA, NSA and npm Release Software Supply Chain GuidanceBest practices are designed to help developers bolster securityLeer másBest practices are designed to help developers bolster security
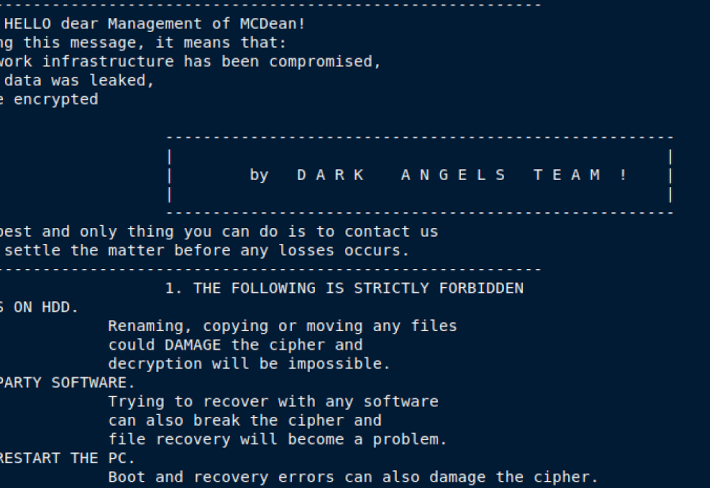
New Ransomware Group BianLian Activity Exploding
New Ransomware Group BianLian Activity ExplodingThe threat actor using the common Go programming language and a custom toolkit claims twenty victimsLeer másThe threat actor using the...
Will cyber‑insurance pay out? – Week in security with Tony Anscombe
Will cyber‑insurance pay out? – Week in security with Tony AnscombeWhat if your organization is hit by a cyberattack that is attributed to a nation state?...
Attack infrastructure used in Cisco hack linked to Evil Corp affiliate
Attack infrastructure used in Cisco hack linked to Evil Corp affiliateResearchers discovered that the infrastructure used in Cisco hack was the same used to target a...
JuiceLedger Hacker Linked to First Phishing Campaign Targeting PyPI Users
JuiceLedger Hacker Linked to First Phishing Campaign Targeting PyPI UsersJuiceLedger started poisoning open-source packages as a way to target a wider audience in AugustLeer másJuiceLedger started...
Google Chrome Vulnerability Lets Sites Quietly Overwrite Clipboard Contents
Google Chrome Vulnerability Lets Sites Quietly Overwrite Clipboard ContentsThe bug was discovered by developer Jeff Johnson, who detailed his findings in a blog postLeer másThe bug...
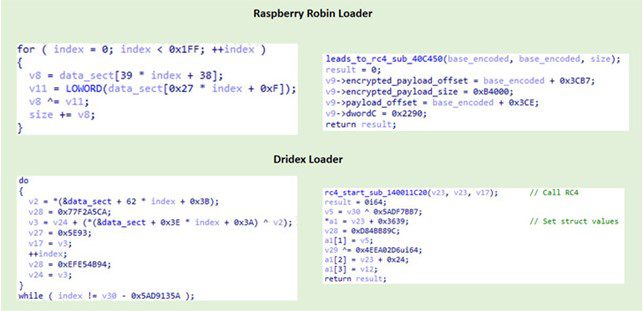
Experts link Raspberry Robin Malware to Evil Corp cybercrime gang
Experts link Raspberry Robin Malware to Evil Corp cybercrime gangResearchers attribute the Raspberry Robin malware to the Russian cybercrime group known as Evil Corp group. IBM...
Google Chrome issue allows overwriting the clipboard content
Google Chrome issue allows overwriting the clipboard contentA security issue in the Google Chrome browser could allow malicious web pages to automatically overwrite clipboard content. A...
The Prynt Stealer malware contains a secret backdoor. Crooks steal data from other cybercriminals
The Prynt Stealer malware contains a secret backdoor. Crooks steal data from other cybercriminalsThe information-stealing malware Prynt Stealer contains a backdoor that allows stealing the data...
US Police Deployed Obscure Smartphone Tracking Tool With No Warrants
US Police Deployed Obscure Smartphone Tracking Tool With No WarrantsIt would allow police to search billions of mobile device-based records, including GPS dataLeer másIt would allow...
Another Ransomware For Linux Likely In Development
Another Ransomware For Linux Likely In DevelopmentUptycs researchers recently spotted a new Linux ransomware that appears to be under active development. The Uptycs Threat Research team...
Google rolled out emergency fixes to address actively exploited Chrome zero-day
Google rolled out emergency fixes to address actively exploited Chrome zero-dayGoogle rolled out emergency fixes to address a vulnerability in the Chrome web browser that is...