SparklingGoblin APT Hackers Using New Linux Variant of SideWalk BackdoorA Linux variant of a backdoor known as SideWalk was used to target a Hong Kong university...
Month: September 2022
Russian Gamaredon Hackers Target Ukrainian Government Using Info-Stealing Malware
Russian Gamaredon Hackers Target Ukrainian Government Using Info-Stealing MalwareAn ongoing espionage campaign operated by the Russia-linked Gamaredon group is targeting employees of Ukrainian government, defense, and...
5 Ways to Mitigate Your New Insider Threats in the Great Resignation
5 Ways to Mitigate Your New Insider Threats in the Great ResignationCompanies are in the midst of an employee "turnover tsunami" with no signs of a slowdown. According to...
Webworm Hackers Using Modified RATs in Latest Cyber Espionage Attacks
Webworm Hackers Using Modified RATs in Latest Cyber Espionage AttacksA threat actor tracked under the moniker Webworm is taking advantage of bespoke variants of already existing...
Researchers Warn of Self-Spreading Malware Targeting Gamers via YouTube
Researchers Warn of Self-Spreading Malware Targeting Gamers via YouTubeGamers looking for cheats on YouTube are being targeted with links to rogue password-protected archive files designed to...
Hackers Targeting WebLogic Servers and Docker APIs for Mining Cryptocurrencies
Hackers Targeting WebLogic Servers and Docker APIs for Mining CryptocurrenciesMalicious actors such as Kinsing are taking advantage of both recently disclosed and older security flaws in...
Uber Says It’s Investigating a Potential Breach of Its Computer Systems
Uber Says It's Investigating a Potential Breach of Its Computer SystemsRide hailing giant Uber disclosed Thursday it's responding to a cybersecurity incident involving a breach of its network...
Researchers Find Link b/w PrivateLoader and Ruzki Pay-Per-Install Services
Researchers Find Link b/w PrivateLoader and Ruzki Pay-Per-Install ServicesCybersecurity researchers have exposed new connections between a widely used pay-per-install (PPI) malware service known as PrivateLoader and...
North Korean Hackers Spreading Trojanized Versions of PuTTY Client Application
North Korean Hackers Spreading Trojanized Versions of PuTTY Client ApplicationA threat with a North Korea nexus has been found leveraging a "novel spear phish methodology" that...
How to Use a UTM Solution & Win Time, Money and Resources
How to Use a UTM Solution & Win Time, Money and ResourcesUnified threat management is thought to be a universal solution for many reasons. First of...
Microsoft Warns of Large-Scale Click Fraud Campaign Targeting Gamers
Microsoft Warns of Large-Scale Click Fraud Campaign Targeting GamersMicrosoft said it's tracking an ongoing large-scale click fraud campaign targeting gamers by means of stealthily deployed browser...
Uber Claims No Sensitive Data Exposed in Latest Breach… But There’s More to This
Uber Claims No Sensitive Data Exposed in Latest Breach… But There's More to ThisUber, in an update, said there is "no evidence" that users' private information...
Hackers Had Access to LastPass’s Development Systems for Four Days
Hackers Had Access to LastPass's Development Systems for Four DaysPassword management solution LastPass shared more details pertaining to the security incident last month, disclosing that the...
Europol and Bitdefender Release Free Decryptor for LockerGoga Ransomware
Europol and Bitdefender Release Free Decryptor for LockerGoga RansomwareA decryptor for the LockerGoga ransomware has been made available by Romanian cybersecurity firm Bitdefender in collaboration with Europol, the...
Your VPN Has Already Been Hacked
Your VPN Has Already Been HackedRemote Access VPNs have been around for over 20 years. Having worked in this space for a long time, I know...
Major Momentum: Apple Supports BIMI in iOS 16
Major Momentum: Apple Supports BIMI in iOS 16Recently, Apple announced support for BIMI in its latest iOS-16 features. This is a major momentum boost for BIMI. With...
BSides Vancouver 2022 – Jason Rivera’s ‘Understanding The Modern Attack: A Review Of The Adversary’s Operational Lifecycle’
BSides Vancouver 2022 – Jason Rivera’s ‘Understanding The Modern Attack: A Review Of The Adversary’s Operational Lifecycle’Our sincere thanks to BSides Vancouver for publishing their outstanding...
Trustero Compliance as a Service Gains New Features
Trustero Compliance as a Service Gains New FeaturesRead about the latest enhancements to Trustero Compliance as a Service, including new AI-powered features and ISO 27001 support....
Trustero Launches New SOC 2 Compliance Help for Startups
Trustero Launches New SOC 2 Compliance Help for StartupsIf you’re part of a startup, you know you face many of the same challenges as your larger...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
4 Problems with Password Managers Today
4 Problems with Password Managers TodayThe four primary problems of password managers causing low adoption and other failures to achieve the desired security outcome are discussed...
Apple Releases iOS and macOS Updates to Patch Actively Exploited Zero-Day Flaw
Apple Releases iOS and macOS Updates to Patch Actively Exploited Zero-Day FlawApple has released another round of security updates to address multiple vulnerabilities in iOS and...
China Accuses NSA’s TAO Unit of Hacking its Military Research University
China Accuses NSA's TAO Unit of Hacking its Military Research UniversityChina has accused the U.S. National Security Agency (NSA) of conducting a string of cyberattacks aimed...
Iranian Hackers Target High-Value Targets in Nuclear Security and Genomic Research
Iranian Hackers Target High-Value Targets in Nuclear Security and Genomic ResearchHackers tied to the Iranian government have been targeting individuals specializing in Middle Eastern affairs, nuclear...
Misinformation and propaganda in the authoritarian internet
Misinformation and propaganda in the authoritarian internet On my sixth birthday, my father gifted me a globe of the world. It is the best birthday present...
How to deal with dates and times without any timezone tantrums…
How to deal with dates and times without any timezone tantrums…Heartfelt encouragement to embrace RFC 3339 - find out why!Leer másNaked SecurityHeartfelt encouragement to embrace RFC...
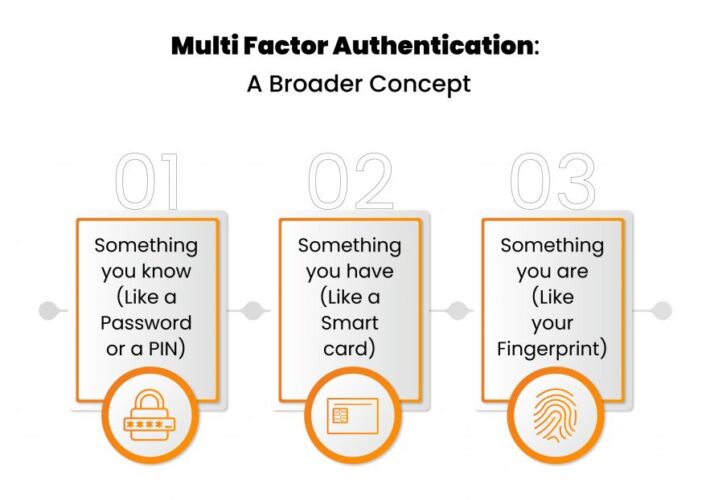
Beef up your Cyber Protection with Multi Factor Authentication
Beef up your Cyber Protection with Multi Factor Authentication“When it comes to security, Two-Factor Authentication proves to be a treasury full of gold.” The severity and...
Barracuda Networks Extends Cybersecurity and Data Protection Portfolio
Barracuda Networks Extends Cybersecurity and Data Protection Portfolio At the Secured.22 virtual conference, Barracuda Networks announced it has added a range of capabilities that collectively tighten...
Apple patches zero-day holes – even in the brand new iOS 16
Apple patches zero-day holes – even in the brand new iOS 16Five updates, one upgrade, plus two zero-days. Patch your Macs, iPhones and iPads as soon...
ESET Research uncovers new APT group Worok – Week in security with Tony Anscombe
ESET Research uncovers new APT group Worok – Week in security with Tony AnscombeWorok takes aim at various high-profile organizations that operate in multiple sectors and...