Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S.A 36-year-old Russian man recently identified by KrebsOnSecurity as the likely proprietor of the massive RSOCKS botnet has...
Month: September 2022
SEO poisoning campaign directs search engine visitors from multiple industries to JavaScript malware
SEO poisoning campaign directs search engine visitors from multiple industries to JavaScript malwareResearchers have discovered a high-effort search engine optimization (SEO) poisoning campaign that seems to...
IT Security Takeaways from the Wiseasy Hack
IT Security Takeaways from the Wiseasy HackLast month Tech Crunch reported that payment terminal manufacturer Wiseasy had been hacked. Although Wiseasy might not be well known in...
BSidesLV 2022 Lucky13 BreakingGround – Shreyas Rami’s, Shaun Jones’ ‘Ransomware Emulation Done Right’
BSidesLV 2022 Lucky13 BreakingGround – Shreyas Rami’s, Shaun Jones’ ‘Ransomware Emulation Done Right’Our sincere thanks to BSidesLV for publishing their outstanding conference videos on the organization's...
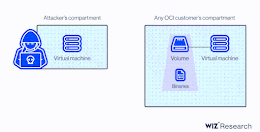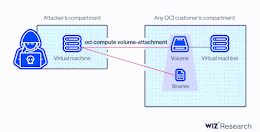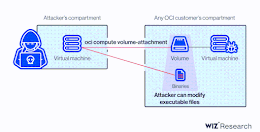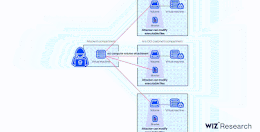
Researchers Disclose Critical Vulnerability in Oracle Cloud Infrastructure
Researchers Disclose Critical Vulnerability in Oracle Cloud InfrastructureResearchers have disclosed a new severe Oracle Cloud Infrastructure (OCI) vulnerability that could be exploited by users to access...
Researchers Uncover Years-Long Mobile Spyware Campaign Targeting Uyghurs
Researchers Uncover Years-Long Mobile Spyware Campaign Targeting UyghursA new wave of a mobile surveillance campaign has been observed targeting the Uyghur community as part of a...
StackHawk Expands API Security Testing Suite
StackHawk Expands API Security Testing Suite StackHawk this week expanded the scope of its application programming interface (API) security testing tools to now include the entire...
Malicious NPM Package Caught Mimicking Material Tailwind CSS Package
Malicious NPM Package Caught Mimicking Material Tailwind CSS PackageA malicious NPM package has been found masquerading as the legitimate software library for Material Tailwind, once again...
Firing Your Entire Cybersecurity Team? Are You Sure?
Firing Your Entire Cybersecurity Team? Are You Sure?What on earth were they thinking? That's what we – and other security experts – were wondering when content...
Void Balaur Hackers-for-Hire Targeting Russian Businesses and Politics Entities
Void Balaur Hackers-for-Hire Targeting Russian Businesses and Politics EntitiesA hack-for-hire group that was first exposed in 2019 has expanded its focus to set its sights on entities with...
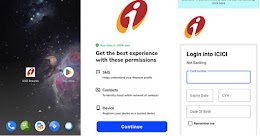
Fake Indian Banking Rewards Apps Targeting Android Users with Info-stealing Malware
Fake Indian Banking Rewards Apps Targeting Android Users with Info-stealing MalwareAn SMS-based phishing campaign is targeting customers of Indian banks with information-stealing malware that masquerades as...
Hackers Using Malicious OAuth Apps to Take Over Email Servers
Hackers Using Malicious OAuth Apps to Take Over Email ServersMicrosoft on Thursday warned of a consumer-facing attack that made use of rogue OAuth applications deployed on...
Researchers Uncover New Metador APT Targeting Telcos, ISPs, and Universities
Researchers Uncover New Metador APT Targeting Telcos, ISPs, and UniversitiesA previously undocumented threat actor of unknown origin has been linked to attacks targeting telecom, internet service...
Morgan Stanley fined millions for selling off devices full of customer PII
Morgan Stanley fined millions for selling off devices full of customer PIICritical data on old disks always seems inaccessible if you really need it. But when...
CISA Warns of Hackers Exploiting Recent Zoho ManageEngine Vulnerability
CISA Warns of Hackers Exploiting Recent Zoho ManageEngine VulnerabilityThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a recently disclosed security flaw in Zoho ManageEngine to...
S3 Ep101: Uber and LastPass breaches – is 2FA all it’s cracked up to be? [Audio + Text]
S3 Ep101: Uber and LastPass breaches – is 2FA all it’s cracked up to be? [Audio + Text]Latest episode - listen now! Learn why adopting 2FA...
Hackers Using Fake CircleCI Notifications to Hack GitHub Accounts
Hackers Using Fake CircleCI Notifications to Hack GitHub AccountsGitHub has put out an advisory detailing what may be an ongoing phishing campaign targeting its users to...
CNAPP buyers guide: Top tools compared
CNAPP buyers guide: Top tools comparedCloud security continues to be a vexing situation, and the tool set continues to become more complex, riddled with acronyms representing...
Q-Scout aims for smartphone security without the intrusiveness
Q-Scout aims for smartphone security without the intrusivenessMobile security firm Quokka—which earlier this week rebranded from its previous name, Kryptowire—is launching a new smartphone protection product...
Recommended security resources for Microsoft Active Directory
Recommended security resources for Microsoft Active DirectoryMany firms are still firmly in an Active Directory (AD) world. They may have moved some applications to the cloud,...
Iranian cyberspies use multi-persona impersonation in phishing threads
Iranian cyberspies use multi-persona impersonation in phishing threadsOne of the most prolific state-sponsored Iranian cyber espionage groups is targeting researchers from different fields by setting up...
One in 10 employees leaks sensitive company data every 6 months: report
One in 10 employees leaks sensitive company data every 6 months: reportInsider threats are an ongoing menace that enterprise security teams need to handle. It's a...
New Sysdig cloud security software prioritizes risk, cuts remediation time
New Sysdig cloud security software prioritizes risk, cuts remediation timeUnified container and cloud security firm Sysdig on Wednesday launched its cloud security posture management (CSPM) offering,...
AutoRabit launches devsecops tool for Salesforce environments
AutoRabit launches devsecops tool for Salesforce environmentsDevsecops firm AutoRabit is trying to address security issues arising from policy changes and misconfigurations in Salesforce environments with a...
Cybersecurity startup launches mobile app to protect against phishing attacks
Cybersecurity startup launches mobile app to protect against phishing attacksCybersecurity startup novoShield has launched an enterprise-grade mobile security application, designed to protect users from mobile phishing...
Excess privilege in the cloud is a universal security problem, IBM says
Excess privilege in the cloud is a universal security problem, IBM saysExcess privilege granted to cloud identities is a key component in 99% of all security...
Russia’s cyber future connected at the waist to Soviet military industrial complex
Russia’s cyber future connected at the waist to Soviet military industrial complexThe Center for European Policy Analysis (CEPA) recently published a 38-page study, Russian Cyberwarfare: Unpacking...
U.S. government issues guidance for developers to secure the software supply chain: Key takeaways
U.S. government issues guidance for developers to secure the software supply chain: Key takeawaysSoftware supply chain attacks are on the rise, as cited in the Cloud...
US government indicts Iranian nationals for ransomware and other cybercrimes
US government indicts Iranian nationals for ransomware and other cybercrimesThe US Department of Justice (DOJ) unsealed an indictment that charged three Iranian cybercriminals with orchestrating a...
Control Structured Data with Intelligent Archiving
Control Structured Data with Intelligent ArchivingIt’s no surprise that nearly every business today faces exponential data growth, with huge volumes of information in diverse formats spread...