Mobile Ransomware: The Next Step for Cybercriminals Targeting smartphones started to be increasingly appealing to cybercriminals as these devices become more and more important in users’...
Day: September 23, 2022
Seven-Year Mobile Surveillance Campaign Targets Uyghurs
Seven-Year Mobile Surveillance Campaign Targets UyghursScarlet Mimic group uses over 20 Android malware variantsLeer másScarlet Mimic group uses over 20 Android malware variants
Australian Telecoms company Optus discloses security breach
Australian Telecoms company Optus discloses security breachAustralian telecoms company Optus disclosed a data breach, threat actors gained access to former and current customers. Optus, one of...
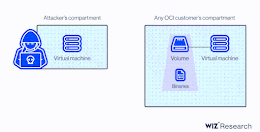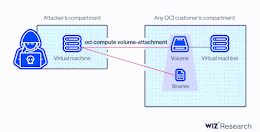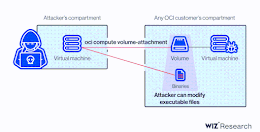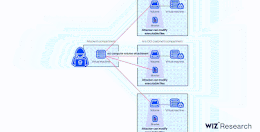
AttachMe: a critical flaw affects Oracle Cloud Infrastructure (OCI)
AttachMe: a critical flaw affects Oracle Cloud Infrastructure (OCI)A critical vulnerability in Oracle Cloud Infrastructure (OCI) could be exploited to access the virtual disks of other...
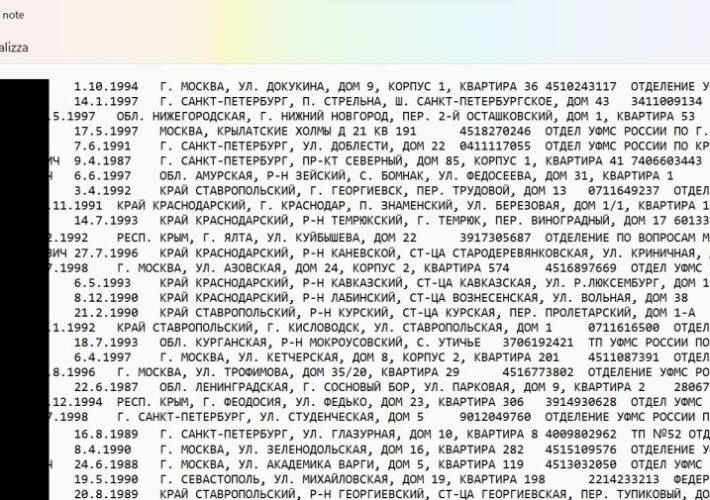
Details of Over 300,000 Russian Reservists Leaked, Anonymous Claims
Details of Over 300,000 Russian Reservists Leaked, Anonymous ClaimsThe group claims the individuals are likely to be mobilized by the Russian government to fight in UkraineLeer...
Surge in Magento 2 template attacks exploiting the CVE-2022-24086 flaw
Surge in Magento 2 template attacks exploiting the CVE-2022-24086 flawSansec researchers warn of a surge in hacking attempts targeting a critical Magento 2 vulnerability tracked as...
5 ways to grow the cybersecurity workforce
5 ways to grow the cybersecurity workforceThe demand for cybersecurity professionals has surged over the past decade. According to (ISC)2’s 2020 Cybersecurity Workforce Study, while the...
CISA adds Zoho ManageEngine flaw to its Known Exploited Vulnerabilities Catalog
CISA adds Zoho ManageEngine flaw to its Known Exploited Vulnerabilities CatalogCISA added a security flaw in Zoho ManageEngine, tracked as CVE-2022-35405, to its Known Exploited Vulnerabilities Catalog. The...
Daniel Stori’s ‘The Ketchup Gun’
Daniel Stori’s ‘The Ketchup Gun’ via Daniel Stori, crafting comics at turnoff.us! Permalink The post Daniel Stori’s ‘The Ketchup Gun’ appeared first on Security Boulevard. Leer...
Cyber Mercenary Group Void Balaur Continues Hack-For-Hire Campaigns
Cyber Mercenary Group Void Balaur Continues Hack-For-Hire CampaignsVoid Balaur campaigns in 2022 targeted various industries across the US, Russia and UkraineLeer másVoid Balaur campaigns in 2022...
Anonymous claims to have hacked the website of the Russian Ministry of Defense
Anonymous claims to have hacked the website of the Russian Ministry of DefenseThe popular collective Anonymous claims to have hacked the website of the Russian Ministry...
Best 10 SIEM Tools to Fuel Up Your Threat-Hunting Grind
Best 10 SIEM Tools to Fuel Up Your Threat-Hunting GrindThreat-hunting has proven to be the most efficient, field-proven countermeasure against cyber threats. Action items based on...
Ransomware operators might be dropping file encryption in favor of corrupting files
Ransomware operators might be dropping file encryption in favor of corrupting filesRansomware started out many years as scams where users were being tricked into paying fictitious...
The Increasing Insider Risk of Emerging Healthcare Technology
The Increasing Insider Risk of Emerging Healthcare TechnologyEarlier this month, the Health Sector Cybersecurity Coordination Center (HC3) issued a grave warning about the security implications of...
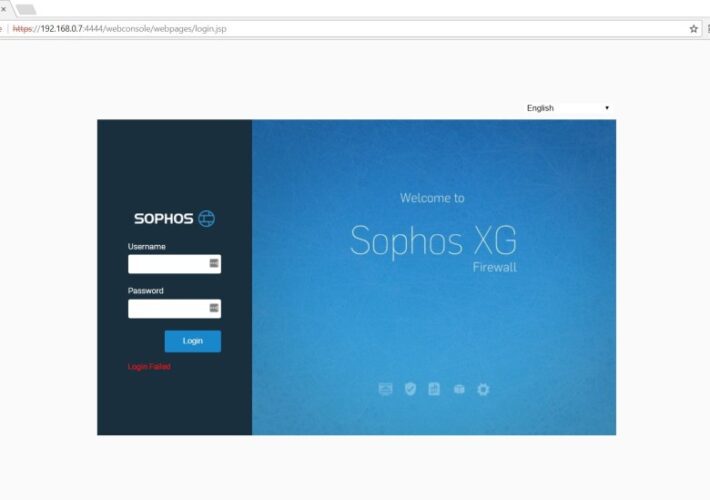
Sophos warns of a new actively exploited flaw in Firewall product
Sophos warns of a new actively exploited flaw in Firewall productSophos warns that a critical code injection security vulnerability in its Firewall product is actively exploited...
Weekly Update 313
Weekly Update 313I came so close to skipping this week's video. I'm surrounded by family, friends and my amazing wife to be in only a couple...
Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread Spam
Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread SpamThe spam emails were sent to trick recipients into signing up for fake paid subscriptionsLeer másThe...
A third of Australian population likely affected in Optus cyberattack
A third of Australian population likely affected in Optus cyberattackAustralia’s second largest telecommunications provider, Optus, revealed it suffered a cyberattack where data from customers have possibly...
Air Force Upgrades Digital Modernization Strategy to “As a Service” Model
Air Force Upgrades Digital Modernization Strategy to "As a Service" ModelThe transition will be carried out through three procurements to be awarded before the end of...
Hey WeLiveSecurity, how does biometric authentication work?
Hey WeLiveSecurity, how does biometric authentication work?Your eyes may be the window to your soul, but they can also be your airplane boarding pass or the...
Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S.
Accused Russian RSOCKS Botmaster Arrested, Requests Extradition to U.S.A 36-year-old Russian man recently identified by KrebsOnSecurity as the likely proprietor of the massive RSOCKS botnet has...
SEO poisoning campaign directs search engine visitors from multiple industries to JavaScript malware
SEO poisoning campaign directs search engine visitors from multiple industries to JavaScript malwareResearchers have discovered a high-effort search engine optimization (SEO) poisoning campaign that seems to...
IT Security Takeaways from the Wiseasy Hack
IT Security Takeaways from the Wiseasy HackLast month Tech Crunch reported that payment terminal manufacturer Wiseasy had been hacked. Although Wiseasy might not be well known in...
BSidesLV 2022 Lucky13 BreakingGround – Shreyas Rami’s, Shaun Jones’ ‘Ransomware Emulation Done Right’
BSidesLV 2022 Lucky13 BreakingGround – Shreyas Rami’s, Shaun Jones’ ‘Ransomware Emulation Done Right’Our sincere thanks to BSidesLV for publishing their outstanding conference videos on the organization's...
Researchers Disclose Critical Vulnerability in Oracle Cloud Infrastructure
Researchers Disclose Critical Vulnerability in Oracle Cloud InfrastructureResearchers have disclosed a new severe Oracle Cloud Infrastructure (OCI) vulnerability that could be exploited by users to access...
Researchers Uncover Years-Long Mobile Spyware Campaign Targeting Uyghurs
Researchers Uncover Years-Long Mobile Spyware Campaign Targeting UyghursA new wave of a mobile surveillance campaign has been observed targeting the Uyghur community as part of a...
StackHawk Expands API Security Testing Suite
StackHawk Expands API Security Testing Suite StackHawk this week expanded the scope of its application programming interface (API) security testing tools to now include the entire...
Malicious NPM Package Caught Mimicking Material Tailwind CSS Package
Malicious NPM Package Caught Mimicking Material Tailwind CSS PackageA malicious NPM package has been found masquerading as the legitimate software library for Material Tailwind, once again...
Firing Your Entire Cybersecurity Team? Are You Sure?
Firing Your Entire Cybersecurity Team? Are You Sure?What on earth were they thinking? That's what we – and other security experts – were wondering when content...
Void Balaur Hackers-for-Hire Targeting Russian Businesses and Politics Entities
Void Balaur Hackers-for-Hire Targeting Russian Businesses and Politics EntitiesA hack-for-hire group that was first exposed in 2019 has expanded its focus to set its sights on entities with...