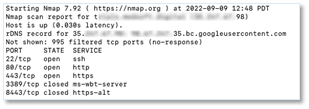
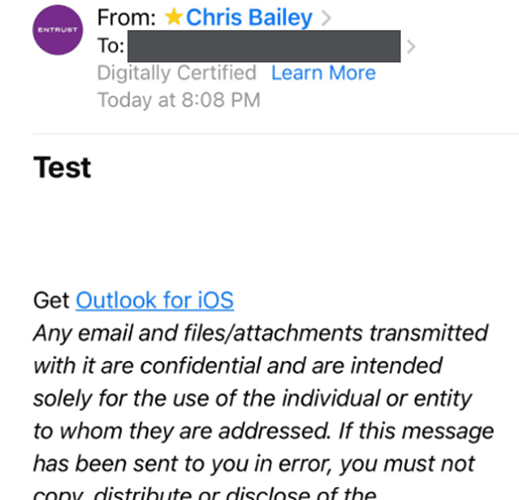
Your VPN Has Already Been HackedRemote Access VPNs have been around for over 20 years. Having worked in this space for a long time, I know...
Day: September 13, 2022
Major Momentum: Apple Supports BIMI in iOS 16
Major Momentum: Apple Supports BIMI in iOS 16Recently, Apple announced support for BIMI in its latest iOS-16 features. This is a major momentum boost for BIMI. With...
BSides Vancouver 2022 – Jason Rivera’s ‘Understanding The Modern Attack: A Review Of The Adversary’s Operational Lifecycle’
BSides Vancouver 2022 – Jason Rivera’s ‘Understanding The Modern Attack: A Review Of The Adversary’s Operational Lifecycle’Our sincere thanks to BSides Vancouver for publishing their outstanding...
Trustero Compliance as a Service Gains New Features
Trustero Compliance as a Service Gains New FeaturesRead about the latest enhancements to Trustero Compliance as a Service, including new AI-powered features and ISO 27001 support....
Trustero Launches New SOC 2 Compliance Help for Startups
Trustero Launches New SOC 2 Compliance Help for StartupsIf you’re part of a startup, you know you face many of the same challenges as your larger...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
4 Problems with Password Managers Today
4 Problems with Password Managers TodayThe four primary problems of password managers causing low adoption and other failures to achieve the desired security outcome are discussed...
China Accuses NSA’s TAO Unit of Hacking its Military Research University
China Accuses NSA's TAO Unit of Hacking its Military Research UniversityChina has accused the U.S. National Security Agency (NSA) of conducting a string of cyberattacks aimed...
Apple Releases iOS and macOS Updates to Patch Actively Exploited Zero-Day Flaw
Apple Releases iOS and macOS Updates to Patch Actively Exploited Zero-Day FlawApple has released another round of security updates to address multiple vulnerabilities in iOS and...
Iranian Hackers Target High-Value Targets in Nuclear Security and Genomic Research
Iranian Hackers Target High-Value Targets in Nuclear Security and Genomic ResearchHackers tied to the Iranian government have been targeting individuals specializing in Middle Eastern affairs, nuclear...
Misinformation and propaganda in the authoritarian internet
Misinformation and propaganda in the authoritarian internet On my sixth birthday, my father gifted me a globe of the world. It is the best birthday present...
How to deal with dates and times without any timezone tantrums…
How to deal with dates and times without any timezone tantrums…Heartfelt encouragement to embrace RFC 3339 - find out why!Leer másNaked SecurityHeartfelt encouragement to embrace RFC...
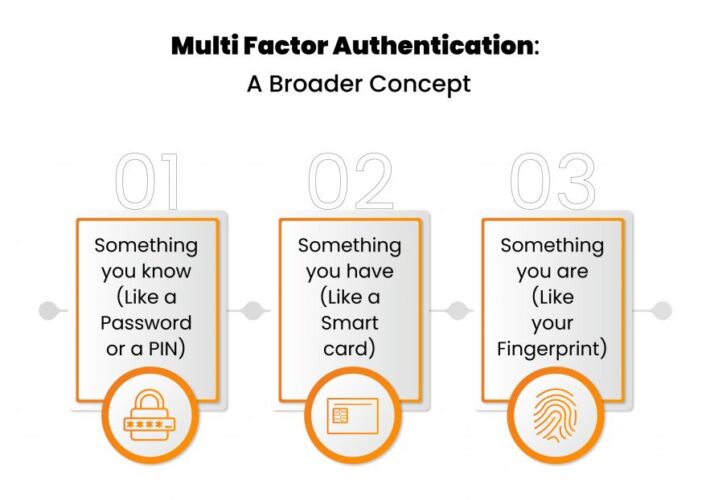
Beef up your Cyber Protection with Multi Factor Authentication
Beef up your Cyber Protection with Multi Factor Authentication“When it comes to security, Two-Factor Authentication proves to be a treasury full of gold.” The severity and...
Barracuda Networks Extends Cybersecurity and Data Protection Portfolio
Barracuda Networks Extends Cybersecurity and Data Protection Portfolio At the Secured.22 virtual conference, Barracuda Networks announced it has added a range of capabilities that collectively tighten...
Apple patches zero-day holes – even in the brand new iOS 16
Apple patches zero-day holes – even in the brand new iOS 16Five updates, one upgrade, plus two zero-days. Patch your Macs, iPhones and iPads as soon...
ESET Research uncovers new APT group Worok – Week in security with Tony Anscombe
ESET Research uncovers new APT group Worok – Week in security with Tony AnscombeWorok takes aim at various high-profile organizations that operate in multiple sectors and...
What Is DNS Filtering and Why Does Your Business Need It?
What Is DNS Filtering and Why Does Your Business Need It?One of the most popular methods used by companies and providers to protect their environments from...
Five ways your data may be at risk — and what to do about it
Five ways your data may be at risk — and what to do about itWe store vast amounts of data — financial records, photos/videos, family schedules,...
Pro-Palestinian group GhostSec hacked Berghof PLCs in Israel
Pro-Palestinian group GhostSec hacked Berghof PLCs in IsraelThe hacktivist collective GhostSec claimed to have compromised 55 Berghof PLCs used by Israeli organizations. Pro-Palestinian Hacking Group GhostSec claimed to...
Montenegro and its allies are working to recover from the massive cyber attack
Montenegro and its allies are working to recover from the massive cyber attackA massive cyberattack hit Montenegro, officials believe that it was launched by pro-Russian hackers...
Lampion Trojan Launches New Campaign Through File-Sharing Service
Lampion Trojan Launches New Campaign Through File-Sharing ServiceLampion trojan is again in action, this time launching a large phishing campaign. The unknown threat actors behind this...
Leading a Revolution to Provide Secure CCTV Cameras
Leading a Revolution to Provide Secure CCTV CamerasBy Mitch Muro, Product Marketing Manager, Check Point Software Technologies When building IoT devices, it is important to […]...
Cloud attacks on the supply chain are a huge concern
Cloud attacks on the supply chain are a huge concernContenido de la entradaLeer másProofpoint News Feed
Apple released iOS 16 with Lockdown, Safety Check security features
Apple released iOS 16 with Lockdown, Safety Check security featuresApple released iOS 16 today with new features to boost iPhone users' security and privacy, including Lockdown...
Levelling The Battlefield with Cyber as An Asymmetric Leverage
Levelling The Battlefield with Cyber as An Asymmetric LeverageBy Goh Eng Choon, President for Cyber, ST Engineering From sabotaging, stealing and destroying valuable enterprise data to...
Lazarus Group Resurfaces, Exploiting Log4j Vulnerability and Spreading MagicRAT
Lazarus Group Resurfaces, Exploiting Log4j Vulnerability and Spreading MagicRAT Lazarus Group, also known as APT38, Dark Seoul, Hidden Cobra, and Zinc, has garnered a reputation as...
Cybercrime Group TA558 Ramps Up Email Attacks Against Hotels
Cybercrime Group TA558 Ramps Up Email Attacks Against HotelsContenido de la entradaLeer másProofpoint News Feed
VMware: 70% drop in Linux ESXi VM performance with Retbleed fixes
VMware: 70% drop in Linux ESXi VM performance with Retbleed fixesVMware is warning that ESXi VMs running on Linux kernel 5.19 can have up to a 70%...
Cloud security: Increased concern about risks from partners, suppliers
Cloud security: Increased concern about risks from partners, suppliersContenido de la entradaLeer másProofpoint News Feed
New Linux Cryptomining Malware
New Linux Cryptomining MalwareIt’s pretty nasty: The malware was dubbed “Shikitega” for its extensive use of the popular Shikata Ga Nai polymorphic encoder, which allows the...