DEADBOLT ransomware rears its head again, attacks QNAP devicesNAS devices make it easy for anyone to add high-capacity file servers to their network. Guess why cybercrooks...
Day: September 7, 2022
Channel 4 optimizes cybersecurity and boosts efficiency after partnering with Invicti
Channel 4 optimizes cybersecurity and boosts efficiency after partnering with InvictiUsing Invicti for vulnerability scanning has allowed Channel 4 to improve security while also spending less...
What Is Your Security Team Profile? Prevention, Detection, or Risk Management
What Is Your Security Team Profile? Prevention, Detection, or Risk ManagementNot all security teams are born equal. Each organization has a different objective. In cybersecurity, adopting...
QNAP Warns of New DeadBolt Ransomware Attacks Exploiting Photo Station Flaw
QNAP Warns of New DeadBolt Ransomware Attacks Exploiting Photo Station FlawQNAP has issued a new advisory urging users of its network-attached storage (NAS) devices to upgrade...
TikTok Denies Data Breach Reportedly Exposing Over 2 Billion Users’ Information
TikTok Denies Data Breach Reportedly Exposing Over 2 Billion Users' InformationPopular short-form social video service TikTok denied reports that it was breached by a hacking group,...
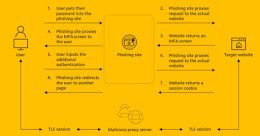
New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security
New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor SecurityA new phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy is being advertised on the criminal underground as a means...
Researchers Find New Android Spyware Campaign Targeting Uyghur Community
Researchers Find New Android Spyware Campaign Targeting Uyghur CommunityA previously undocumented strain of Android spyware with extensive information gathering capabilities has been found disguised as a...
Worok Hackers Target High-Profile Asian Companies and Governments
Worok Hackers Target High-Profile Asian Companies and GovernmentsHigh-profile companies and local governments located primarily in Asia are the subjects of targeted attacks by a previously undocumented...
TA505 Hackers Using TeslaGun Panel to Manage ServHelper Backdoor Attacks
TA505 Hackers Using TeslaGun Panel to Manage ServHelper Backdoor AttacksCybersecurity researchers have offered fresh insight into a previously undocumented software control panel used by a financially...
Integrating Live Patching in SecDevOps Workflows
Integrating Live Patching in SecDevOps WorkflowsSecDevOps is, just like DevOps, a transformational change that organizations undergo at some point during their lifetime. Just like many other...
Mirai Variant MooBot Botnet Exploiting D-Link Router Vulnerabilities
Mirai Variant MooBot Botnet Exploiting D-Link Router VulnerabilitiesA variant of the Mirai botnet known as MooBot is co-opting vulnerable D-Link devices into an army of denial-of-service...
Critical RCE Vulnerability Affects Zyxel NAS Devices — Firmware Patch Released
Critical RCE Vulnerability Affects Zyxel NAS Devices — Firmware Patch ReleasedNetworking equipment maker Zyxel has released patches for a critical security flaw impacting its network-attached storage...
New Stealthy Shikitega Malware Targeting Linux Systems and IoT Devices
New Stealthy Shikitega Malware Targeting Linux Systems and IoT DevicesA new piece of stealthy Linux malware called Shikitega has been uncovered adopting a multi-stage infection chain...
North Korean Hackers Deploying New MagicRAT Malware in Targeted Campaigns
North Korean Hackers Deploying New MagicRAT Malware in Targeted CampaignsThe prolific North Korean nation-state actor known as the Lazarus Group has been linked to a new...
4 Key Takeaways from “XDR is the Perfect Solution for SMEs” webinar
4 Key Takeaways from "XDR is the Perfect Solution for SMEs" webinarCyberattacks on large organizations dominate news headlines. So, you may be surprised to learn that...
Some Members of Conti Group Targeting Ukraine in Financially Motivated Attacks
Some Members of Conti Group Targeting Ukraine in Financially Motivated AttacksFormer members of the Conti cybercrime cartel have been implicated in five different campaigns targeting Ukraine...
Authorities Shut Down WT1SHOP Site for Selling Stolen Credentials and Credit Cards
Authorities Shut Down WT1SHOP Site for Selling Stolen Credentials and Credit CardsAn international law enforcement operation has resulted in the dismantling of WT1SHOP, an online criminal marketplace...
Top 5 Zero-Day Vulnerabilities of August
Top 5 Zero-Day Vulnerabilities of AugustZero day vulnerabilities and exploits are unexpected, hence zero-day protection is required. Here are some suggestions for preventing zero-day attacks on...
Game-Related Cyber-Threats: Almost 100k Malicious Files Last Year
Game-Related Cyber-Threats: Almost 100k Malicious Files Last YearKaspersky also observed an increase in the number of programs that can steal secretsLeer másKaspersky also observed an increase...
Password Reuse is Putting MSP’s at Risk
Password Reuse is Putting MSP’s at RiskPassword hygiene is a huge priority for Managed Service Providers Every organization is at risk for cyber attack, but MSPs...
Google Vulnerability Reward Program Focuses on Open Source Software
Google Vulnerability Reward Program Focuses on Open Source Software Google’s bug bounty program will be expanded to include a special open source section called the Open...
BlackCat Ransomware Linked to Italy’s Energy Services Firm Hack
BlackCat Ransomware Linked to Italy's Energy Services Firm HackThe ransomware group claimed to have downloaded 700GB of data from GSELeer másThe ransomware group claimed to have...
The Mayhem for API Difference – A ZAP – API Scan Comparison
The Mayhem for API Difference – A ZAP – API Scan ComparisonWith the rapid development of modern web APIs, developers must balance quality, reliability, and security...
Meta Fined $400m in Ireland For Children’s Privacy Breach
Meta Fined $400m in Ireland For Children's Privacy BreachInstagram allowed children to run business accounts, which showed phone numbers and email addressesLeer másInstagram allowed children to...
Using Backups to Turn the Tables on Ransomware
Using Backups to Turn the Tables on Ransomware When an enterprise gets hit with ransomware, the fundamental question is whether the cost of downtime is greater...
In-app browser security risks, and what to do about them
In-app browser security risks, and what to do about themIn-app browsers can pose significant security risks to businesses, with their tendency to track data a primary...
Cloud-Based File Systems as a Ransomware Defense
Cloud-Based File Systems as a Ransomware Defense Ransomware is an unfortunate and unavoidable fact of life for businesses today. Attackers are escalating their attacks on organizations...
Interpol Busts Asian Sextortion Syndicate
Interpol Busts Asian Sextortion SyndicateCops launched public awareness campaign in June to warn potential victimsLeer másCops launched public awareness campaign in June to warn potential victims
California Regulators Hit Sephora with $1.2M Fine
California Regulators Hit Sephora with $1.2M Fine Regulators have roared back from a pandemic-induced stupor that seemingly tamped down some of the most aggressive actions at...
Orgs Report Mixed Progress on Ransomware Defense
Orgs Report Mixed Progress on Ransomware Defense A survey of 400 technology, financial and security leaders published today by HYCU, a provider of a data protection...