United States Labor Day 2022 Construction workers sit on a New York City skyscraper girder in 1932. The building today is known as Rockefeller Plaza. (Image...
Day: September 6, 2022
Identity Verification for Telehealth: A New Boon To The Medical Industry
Identity Verification for Telehealth: A New Boon To The Medical IndustryTelehealthcare Sector is one of the best innovations that could have happened to the healthcare industry....
Extra, Extra, VERT Reads All About It: Cybersecurity News for the Week of August 29, 2022
Extra, Extra, VERT Reads All About It: Cybersecurity News for the Week of August 29, 2022All of us at Tripwire’s Vulnerability Exposure and Research Team (VERT)...
How to address IoT security challenges?
How to address IoT security challenges? My first association with IoT was way back in 2016. We were then working on developing an IoT-based solution for monitoring...
What is Flutter? Is Flutter a Good Business Prospective?
What is Flutter? Is Flutter a Good Business Prospective?Flutter makes it easier for developers to build apps with high-quality graphics, animation, and performance. The framework has...
Ransomware Attackers Abuse Genshin Impact Anti-Cheat System to Disable Antivirus
Ransomware Attackers Abuse Genshin Impact Anti-Cheat System to Disable AntivirusA vulnerable anti-cheat driver for the Genshin Impact video game has been leveraged by a cybercrime actor...
Paul’s Security Weekly #753. “Data Integrity Lights the Way: Security With the Decentralized Web”
Paul’s Security Weekly #753. “Data Integrity Lights the Way: Security With the Decentralized Web”I joined the PSW crew for a discussion about data integrity and decentralized...
Email Security News Round-Up [August 2022]
Email Security News Round-Up [August 2022]August was another busy month in the cyberworld. From email security news headlines and hot cybersecurity news, here’s our monthly news...
Ransomware’s rise: What can be done about it
Ransomware’s rise: What can be done about it A new report by John Sakellariadis for the Atlantic Council takes a deeper dive into the rise of...
WhatsApp Scams in 2022: What to Look out for
WhatsApp Scams in 2022: What to Look out forWhatsApp is ranked as the most popular mobile messenger app in the world. In fact, there are two...
Chrome and Edge fix zero-day security hole – update now!
Chrome and Edge fix zero-day security hole – update now!This time, the crooks got there first - only 1 security hole patched, but it's a zero-day.Leer...
How is Document verification used to verify the authenticity of an Identity document?
How is Document verification used to verify the authenticity of an Identity document?Before the world transitioned to digital-first onboarding due to cellphones, high-speed internet, and a...
EvilProxy Phishing Toolkit Spotted on Dark Web Forums
EvilProxy Phishing Toolkit Spotted on Dark Web ForumsThe tool highlights the growth in attacks against online services and MFA authorization mechanismsLeer másThe tool highlights the growth...
SharkBot Malware Resurfaces on Google Play to Steal Users’ Credentials
SharkBot Malware Resurfaces on Google Play to Steal Users' CredentialsIt reportedly targets the banking credentials of Android users via apps with 60,000 installationsLeer másIt reportedly targets...
Keybank’s Customer Information Stolen By Hackers Via Third-party Provider
Keybank's Customer Information Stolen By Hackers Via Third-party ProviderOverby-Seawell, a firm providing multiple clients with insurance services is alleged to have been the source of the...
London’s Biggest Bus Operator Hit by Cyber “Incident”
London's Biggest Bus Operator Hit by Cyber "Incident"Go-Ahead is working through its incident response plansLeer másGo-Ahead is working through its incident response plans
TikTok denies data breach following leak of user data
TikTok denies data breach following leak of user dataThreat actors published a sample of data allegedly stolen from TikTok, but the company denies it was breached....
Windows Defender identified Chromium, Electron apps as Hive Ransomware
Windows Defender identified Chromium, Electron apps as Hive RansomwareMicrosoft released a Windows Defender update to fix a problem that caused Defender antivirus to identify Chromium, Electron,...
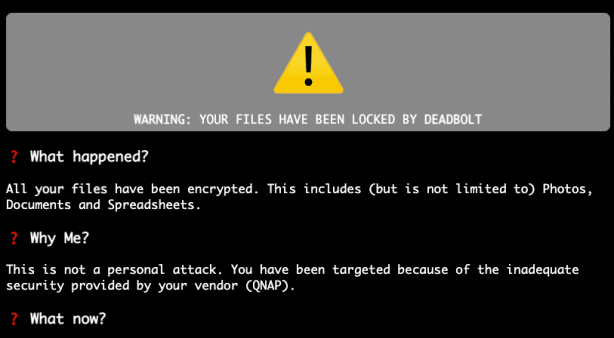
QNAP warns new Deadbolt ransomware attacks exploiting zero-day
QNAP warns new Deadbolt ransomware attacks exploiting zero-dayQNAP warns customers of ongoing DeadBolt ransomware attacks that are exploiting a zero-day vulnerability in Photo Station. QNAP warns...
China accuses the US of cyberattacks
China accuses the US of cyberattacksChina accuses the United States of conducting tens of thousands of cyberattacks on its country, including cyberespionage campaigns. The Government of...
Interpol dismantled sextortion ring in Asia
Interpol dismantled sextortion ring in AsiaInterpol arrested 12 individuals which are suspected to be core members of a transnational sextortion ring. Interpol announced the arrest of...
Is TikTok Safe?
Is TikTok Safe?TikTok (also known as Douyin in China) is a short-form video hosting service owned by the Chinese corporation ByteDance. It features a wide range...
A New and Upgraded Version of SharkBot Malware Has Been Detected
A New and Upgraded Version of SharkBot Malware Has Been DetectedSharkBot malware is back in Google Play Store where two SharkbotDopper apps were identified. The two...
Golang Attack Campaign Tracked as GO#WEBBFUSCATOR Applies James Webb Space Telescope Images as Lures to Infect Systems
Golang Attack Campaign Tracked as GO#WEBBFUSCATOR Applies James Webb Space Telescope Images as Lures to Infect Systems The modern cyber threat landscape illustrates a growing trend...
Raspberry Robin Malware Detection: New Connections Revealed
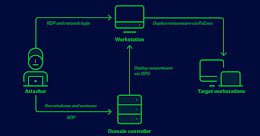
Raspberry Robin Malware Detection: New Connections Revealed In late July, Microsoft researchers released new evidence linking Raspberry Robin Windows worm to the activity of the russia-backed...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel Sectors
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel SectorsContenido de la entradaLeer másProofpoint News Feed
TikTok denies security breach after hackers leak user data, source code
TikTok denies security breach after hackers leak user data, source codeTikTok denies recent claims it was breached, and source code and user data were stolen, telling...
QNAP patches zero-day used in new Deadbolt ransomware attacks
QNAP patches zero-day used in new Deadbolt ransomware attacksQNAP is warning customers of ongoing DeadBolt ransomware attacks that started on Saturday by exploiting a zero-day vulnerability...
Interpol dismantles sextortion ring, warns of increased attacks
Interpol dismantles sextortion ring, warns of increased attacksA transnational sextortion ring was uncovered and dismantled following a joint investigation between Interpol's cybercrime division and police in Singapore and...