Risky Business: Enterprises Can’t Shake Log4j flaw70% of Large enterprises that previously addressed the Log4j flaw are still struggling to patch Log4j-vulnerable assets. INTRODUCTION In December...
Month: August 2022
Cisco fixed a flaw in ASA, FTD devices that can give access to RSA private key
Cisco fixed a flaw in ASA, FTD devices that can give access to RSA private keyCisco addressed a high severity flaw, tracked as CVE-2022-20866, affecting Adaptive...
Ex Twitter employee found guilty of spying for Saudi Arabian government
Ex Twitter employee found guilty of spying for Saudi Arabian governmentA former Twitter employee was found guilty of spying on certain Twitter users for Saudi Arabia....
Cisco Event Response: Corporate Network Security Incident
Cisco Event Response: Corporate Network Security IncidentContenido de la entradaLeer másCisco Event Responses
Emotet Tops List of July’s Most Widely Used Malware
Emotet Tops List of July's Most Widely Used MalwareThe Emotet botnet continues to evolve and now includes a credit card stealer moduleLeer másThe Emotet botnet continues...
Chinese APT group uses multiple backdoors in attacks on military and research organizations
Chinese APT group uses multiple backdoors in attacks on military and research organizationsSince early this year, a known APT group of Chinese origin has been targeting...
Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP Reports
Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP ReportsThe report shows an 11% rise in archive files containing malware, including LNK filesLeer...
DeathStalker’s VileRAT Continues to Target Foreign and Crypto Exchanges
DeathStalker's VileRAT Continues to Target Foreign and Crypto ExchangesThe campaign is not only ongoing, the threat actors increased its efforts to compromise targets using VileRATLeer másThe...
CrowdStrike adds AI-powered indicators of attack to Falcon platform
CrowdStrike adds AI-powered indicators of attack to Falcon platformCybersecurity vendor CrowdStrike has added new AI-powered indicators of attack (IoA) functionality to its Falcon platform. Announced at...
Suspected $3m Romance Scammer Extradited to Japan
Suspected $3m Romance Scammer Extradited to JapanInterpol warns of growing role of money mulesLeer másInterpol warns of growing role of money mules
Microsoft urges Windows users to run patch for DogWalk zero-day exploit
Microsoft urges Windows users to run patch for DogWalk zero-day exploitDespite previously claiming the DogWalk vulnerability did not constitute a security issue, Microsoft has now released...
Microsoft Patches ‘Dogwalk’ Zero-Day and 17 Critical Flaws
Microsoft Patches ‘Dogwalk’ Zero-Day and 17 Critical FlawsAugust Patch Tuesday tackles 121 CVEs, 17 critical bugs and one zero-day bug exploited in the wild.Leer másThreatpostAugust Patch...
Podcast: Inside the Hackers’ Toolkit
Podcast: Inside the Hackers’ ToolkitThis edition of the Threatpost podcast is sponsored by Egress.Leer másThreatpostThis edition of the Threatpost podcast is sponsored by Egress.
Sensitive data in the cloud gets new automated remediation tool from BigID
Sensitive data in the cloud gets new automated remediation tool from BigIDData intelligence company BigID announced this week at the Black Hat conference in Las Vegas...
Patch Tuesday Advisory – August 2022
Patch Tuesday Advisory – August 2022Fixes for 17 critical CVEs and 2 zero-days including DogWalk For August, the number of patched threats announced by Microsoft totals...
Aspen Security Forum 2022 – Moderator: Sarah Smith – ‘Food Security Is National Security’
Aspen Security Forum 2022 – Moderator: Sarah Smith – ‘Food Security Is National Security’Ertharin Cousin, Former Executive Director, UN World Food Programme Michael Froman, Vice Chairman...
Building a modern API security strategy — API components
Building a modern API security strategy — API components Part three of the five-part series, Building a modern API security strategy. The post Building a modern...
Traditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s Why
Traditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s WhyTraditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s Why brooke.crothers Wed, 08/10/2022 - 16:43...
Is Your AppSec Program Developer-Centric?
Is Your AppSec Program Developer-Centric? You need an AppSec program. Software supports your business, and you need to know that attackers can’t kick that ground out...
Twilio Breach: Three Steps to Protect Your Company
Twilio Breach: Three Steps to Protect Your CompanyTwilio published an incident report on August 4, 2022 about an attack that led to employee and customer account...
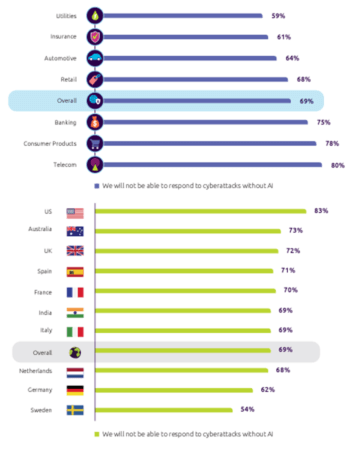
Convergence and adoption of AI and ML countering the cyber threat
Convergence and adoption of AI and ML countering the cyber threatDuring the last few years, we have witnessed an increase in advanced cyber attacks. Cybercriminals utilize...
NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber Resilience
NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber ResilienceThe post NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber Resilience appeared...
Digital milestones for elementary schoolers
Digital milestones for elementary schoolers The internet is a vital part of kids’ lives today. They see grown-ups and older kids going online with all kinds...
Why is Cybersecurity Essential for Small Businesses?
Why is Cybersecurity Essential for Small Businesses?Cybersecurity is a common term for every business but how seriously is it taken? Small businesses often have no budget...
APIC/EPIC! Intel chips leak secrets even the kernel shouldn’t see…
APIC/EPIC! Intel chips leak secrets even the kernel shouldn’t see…If you've ever written code that left stuff lying around in memory when you didn't need it...
Former Twitter Employee Found Guilty of Spying for Saudi Arabia
Former Twitter Employee Found Guilty of Spying for Saudi ArabiaA former Twitter employee has been pronounced guilty for his role in digging up private information pertaining...
Experts Uncover Details on Maui Ransomware Attack by North Korean Hackers
Experts Uncover Details on Maui Ransomware Attack by North Korean HackersThe first ever incident possibly involving the ransomware family known as Maui occurred on April 15,...
Hybrid Identity Protection with Denis Ontiveros Merlo
Hybrid Identity Protection with Denis Ontiveros MerloSecurity architectures depend on identity—the “new security boundary.” Yet despite investment in identity and attempts to drive a sustainable identity...
Debunking IAST myths
Debunking IAST myths If you have followed Contrast's progress over the years, you will recognize us as a leading provider of Interactive Application Security Testing (IAST)/...
Microsoft Patch Tuesday, August 2022 Edition
Microsoft Patch Tuesday, August 2022 EditionMicrosoft today released updates to fix a record 141 security vulnerabilities in its Windows operating systems and related software. Once again,...