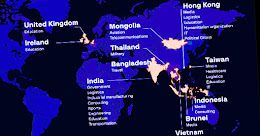
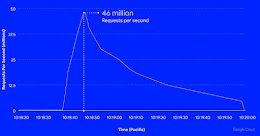
Google Cloud blocks largest HTTPS DDoS attack everGoogle Cloud has claimed to have blocked the largest Layer 7 (HTTPS) DDoS attack to date after a Cloud...
Month: August 2022
Five things security pros want from CNAPP
Five things security pros want from CNAPPAccording to new research from ESG and the Information Systems Security Association (ISSA), 58% of organizations are consolidating or considering consolidating...
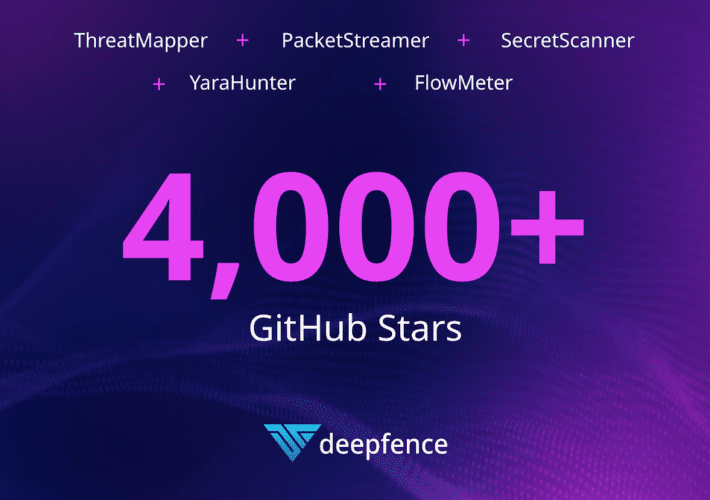
Deepfence Open Source Community Update – August 2022
Deepfence Open Source Community Update – August 2022We’ve seen some tremendous momentum since our last open source community update and are excited to share our most...
Understanding eBPF for API Security
Understanding eBPF for API Security Executive Summary API security is increasingly a top priority for security leaders and risk executives. eBPF has emerged as a potential...
BSidesTLV 2022 – Vera Mens’ ‘Total Flaw: Hacking Flow Computers For Fun And Free Gas’
BSidesTLV 2022 – Vera Mens’ ‘Total Flaw: Hacking Flow Computers For Fun And Free Gas’Our thanks to BSidesTLV for publishing their outstanding conference videos on the...
Black Hat Fireside Chat: Replacing VPNs with ZTNA that leverages WWII battlefield tactics
Black Hat Fireside Chat: Replacing VPNs with ZTNA that leverages WWII battlefield tacticsThe sunsetting of Virtual Private Networks is underway. Related: VPNs as a DIY tool...
Analysis of Clop’s Attack on South Staffordshire Water – UK
Analysis of Clop’s Attack on South Staffordshire Water – UKOn August 15, the Clop ransomware group announced on their leak website the breach of South Staffordshire...
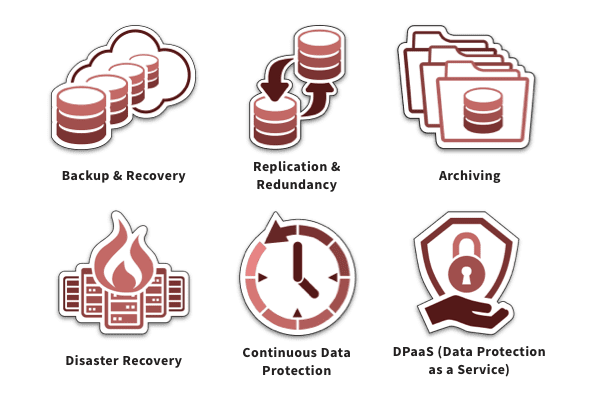
Data Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats
Data Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats “Data really powers everything that we do.” — Jeff Weiner, executive chairman of LinkedIn It...
Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack
Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio HackPopular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month...
Credential Theft Is (Still) A Top Attack Method
Credential Theft Is (Still) A Top Attack MethodCredential theft is clearly still a problem. Even after years of warnings, changing password requirements, and multiple forms of...
Microsoft Warns About Phishing Attacks by Russia-linked Hackers
Microsoft Warns About Phishing Attacks by Russia-linked HackersMicrosoft on Monday revealed it took steps to disrupt phishing operations undertaken by a "highly persistent threat actor" whose...
Russian State Hackers Continue to Attack Ukrainian Entities with Infostealer Malware
Russian State Hackers Continue to Attack Ukrainian Entities with Infostealer MalwareRussian state-sponsored actors are continuing to strike Ukrainian entities with information-stealing malware as part of what's...
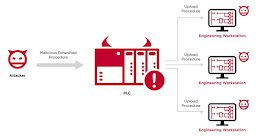
New Evil PLC Attack Weaponizes PLCs to Breach OT and Enterprise Networks
New Evil PLC Attack Weaponizes PLCs to Breach OT and Enterprise NetworksCybersecurity researchers have elaborated a novel attack technique that weaponizes programmable logic controllers (PLCs) to...
Friday Squid Blogging: The Language of the Jumbo Flying Squid
Friday Squid Blogging: The Language of the Jumbo Flying SquidThe jumbo flying squid (Dosidicus gigas) uses its color-changing ability as a language: In 2020, however, marine...
Unified Threat Management: The All-in-One Cybersecurity Solution
Unified Threat Management: The All-in-One Cybersecurity SolutionUTM (Unified threat management) is thought to be an all-in-one solution for cybersecurity. In general, it is a versatile software...
North Korea Hackers Spotted Targeting Job Seekers with macOS Malware
North Korea Hackers Spotted Targeting Job Seekers with macOS MalwareThe North Korea-backed Lazarus Group has been observed targeting job seekers with malware capable of executing on...
RubyGems Makes Multi-Factor Authentication Mandatory for Top Package Maintainers
RubyGems Makes Multi-Factor Authentication Mandatory for Top Package MaintainersRubyGems, the official package manager for the Ruby programming language, has become the latest platform to mandate multi-factor...
Malicious Browser Extensions Targeted Over a Million Users So Far This Year
Malicious Browser Extensions Targeted Over a Million Users So Far This YearMore than 1.31 million users attempted to install malicious or unwanted web browser extensions at...
July Tesla Sales Crashed in Germany and Norway: Not Even on Chart
July Tesla Sales Crashed in Germany and Norway: Not Even on ChartLooking at July I was at first surprised by German news about Fiat having a...
Researchers Link Multi-Year Mass Credential Theft Campaign to Chinese Hackers
Researchers Link Multi-Year Mass Credential Theft Campaign to Chinese HackersA Chinese state-sponsored threat activity group named RedAlpha has been attributed to a multi-year mass credential theft...
Lean Security 101: 3 Tips for Building Your Framework
Lean Security 101: 3 Tips for Building Your FrameworkCobalt, Lazarus, MageCart, Evil, Revil — cybercrime syndicates spring up so fast it's hard to keep track. Until…they...
Goodbye “Kill Chains”, Hello “Attack Sequences”
Goodbye “Kill Chains”, Hello “Attack Sequences”A few years ago at the RSA Conference I co-presented on the top cloud attack “kill chains”. Shawn Harris @infotechwarrior and...
Cybercriminals Developing BugDrop Malware to Bypass Android Security Features
Cybercriminals Developing BugDrop Malware to Bypass Android Security FeaturesIn a sign that malicious actors continue to find ways to work around Google Play Store security protections,...
Hackers Using Bumblebee Loader to Compromise Active Directory Services
Hackers Using Bumblebee Loader to Compromise Active Directory ServicesThe malware loader known as Bumblebee is being increasingly co-opted by threat actors associated with BazarLoader, TrickBot, and...
Chrome browser gets 11 security fixes with 1 zero-day – update now!
Chrome browser gets 11 security fixes with 1 zero-day – update now!Don't delay - patch today.Leer másNaked SecurityDon't delay - patch today.
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver Malware
Researchers Detail Evasive DarkTortilla Crypter Used to Deliver MalwareA .NET-based evasive crypter named DarkTortilla has been used by threat actors to distribute a broad array of commodity malware...
US offers reward “up to $10 million” for information about the Conti gang
US offers reward “up to $10 million” for information about the Conti gangWanted - Reward Offered - Five unknown individuals (plus a man with a weird...
China-backed APT41 Hackers Targeted 13 Organisations Worldwide Last Year
China-backed APT41 Hackers Targeted 13 Organisations Worldwide Last YearThe Chinese advanced persistent threat (APT) actor tracked as Winnti has targeted at least 13 organizations geographically spanning...
Apple patches double zero-day in browser and kernel – update now!
Apple patches double zero-day in browser and kernel – update now!Double 0-day exploits - one in WebKit (to break in) and the other in the kernel...
Google Cloud Blocks Record DDoS attack of 46 Million Requests Per Second
Google Cloud Blocks Record DDoS attack of 46 Million Requests Per SecondGoogle's cloud division on Thursday disclosed it mitigated a series of HTTPS distributed denial-of-service (DDoS)...