Do companies have a false sense of database security?This month, Black Hat 2022 celebrated its 25th year and gathered thousands of security experts and executives from...
Day: August 31, 2022
GigaOm Recognizes DTEX as the Only Outperforming Leader in 2022 Data Loss Prevention Radar Report
GigaOm Recognizes DTEX as the Only Outperforming Leader in 2022 Data Loss Prevention Radar ReportThere is nothing more gratifying in a crowded market filled with good...
Lloyd’s Backs Off Insurance for State-Sponsored Cyberattacks
Lloyd’s Backs Off Insurance for State-Sponsored CyberattacksLloyd's Backs Off Insurance for State-Sponsored Cyberattacks brooke.crothers Tue, 08/30/2022 - 15:00 22 views Cyber related businesses are ‘evolving risk’...
Tech knowledge: Parents believe their children have overtaken them
Tech knowledge: Parents believe their children have overtaken them We’ve recently conducted research that shows that over half of UK parents believe that their child is...
Updated for 2022: What is Network Traffic Analysis? A Beginner’s Guide
Updated for 2022: What is Network Traffic Analysis? A Beginner’s Guide87 percent of organizations use network traffic analysis (NTA) tools for threat detection and response according...
Dealing with a ransomware attack: How can firms spot and recover from these threats?
Dealing with a ransomware attack: How can firms spot and recover from these threats?Ransomware has been one of the biggest cybersecurity trends of the last few...
Interested in Reducing Your Risk Profile? Jamf Has a Solution for That
Interested in Reducing Your Risk Profile? Jamf Has a Solution for ThatThe threat landscape has changed dramatically over the past decade. While cybercriminals continue to look...
Google Launches New Open Source Bug Bounty to Tackle Supply Chain Attacks
Google Launches New Open Source Bug Bounty to Tackle Supply Chain AttacksGoogle on Monday introduced a new bug bounty program for its open source projects, offering...
Chinese Hackers Used ScanBox Framework in Recent Cyber Espionage Attacks
Chinese Hackers Used ScanBox Framework in Recent Cyber Espionage AttacksA months-long cyber espionage campaign undertaken by a Chinese nation-state group targeted several entities with reconnaissance malware...
Hackers Hide Malware in Stunning Images Taken by James Webb Space Telescope
Hackers Hide Malware in Stunning Images Taken by James Webb Space TelescopeA persistent Golang-based malware campaign dubbed GO#WEBBFUSCATOR has leveraged the deep field image taken from...
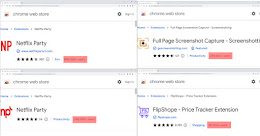
Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million Users
Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million UsersFive imposter extensions for the Google Chrome web browser masquerading as Netflix viewers and others...
Back to School: 7 Top Cybersecurity Tips at this Busy Time
Back to School: 7 Top Cybersecurity Tips at this Busy Time It’s the last week of the summer holidays, and parents, kids, teens, college students... The...
Chrome patches 24 security holes, enables “Sanitizer” safety system
Chrome patches 24 security holes, enables “Sanitizer” safety system24 existing bugs fixed. And, we hope, numerous potential future bugs prevented.Leer másNaked Security24 existing bugs fixed. And,...
Unicorn? Soonicorn? Make Sure SOX ITGC is in Your Sights | anecdotes
Unicorn? Soonicorn? Make Sure SOX ITGC is in Your Sights | anecdotesIf your company is thinking about going IPO, streamlining SOX ITGC Compliance with automation should...
LastPass: When the Password Manager Gets Owned
LastPass: When the Password Manager Gets Owned The LastPass hack currently generating media attention is distressingly common. We’re told that an “unauthorized party” was somehow able...
The Exploitation of Privileged Accounts
The Exploitation of Privileged Accounts The flow of news about data breaches and ransomware attacks is relentless. Businesses of all sizes—large companies included—continue to suffer. Not only...
Find a security hole in Google’s open source and you could bag a $31,337 reward
Find a security hole in Google's open source and you could bag a $31,337 rewardWill it be enough to prevent the next software supply-chain attack? Google...
China-linked APT40 gang targets wind farms, Australian government
China-linked APT40 gang targets wind farms, Australian governmentScanBox installed after victims lured to fake Murdoch news sites with phishing emails Researchers at security company Proofpoint and...
Decisions on health data sharing should not be taken by politicians, citizen juries find
Decisions on health data sharing should not be taken by politicians, citizen juries findBritain's National Data Guardian report also warns NHS needs to earn people’s trust,...
Cryptominer Disguised as Google Translate Targeted 11 Countries
Cryptominer Disguised as Google Translate Targeted 11 CountriesCreated by a Turkish-speaking entity, the malware claimed around 111,000 victims in 11 countriesLeer másCreated by a Turkish-speaking entity,...
Baker & Taylor’s Systems Remain Offline a Week After Ransomware Attack
Baker & Taylor's Systems Remain Offline a Week After Ransomware AttackThe company said it will proceed to restore its systems as soon as they are sanitizedLeer...
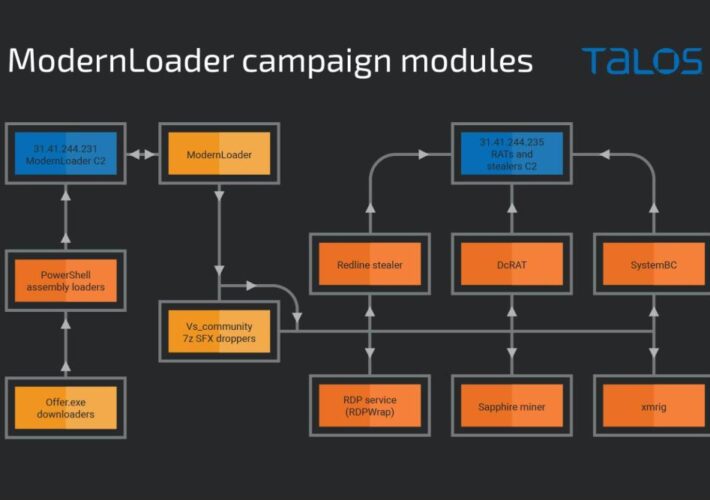
ModernLoader Delivers Stealers, Cryptominers and RATs Via Fake Amazon Gift Cards
ModernLoader Delivers Stealers, Cryptominers and RATs Via Fake Amazon Gift CardsThe association between the three apparently unrelated campaigns was made by Cisco TalosLeer másThe association between...
ICO Pursues Traffic Accident Data Thieves
ICO Pursues Traffic Accident Data ThievesData protection regulator begins criminal proceedingsLeer másData protection regulator begins criminal proceedings
TikShock: Don’t get caught out by these 5 TikTok scams
TikShock: Don’t get caught out by these 5 TikTok scamsAre you aware of the perils of the world’s no. 1 social media? Do you know how...
Ukrainian Police Bust Crypto Fraud Call Centers
Ukrainian Police Bust Crypto Fraud Call CentersScammers spoofed legitimate banks’ phone numbersLeer másScammers spoofed legitimate banks’ phone numbers
Initiative Aims to Encourage Diverse Talent into Cyber
Initiative Aims to Encourage Diverse Talent into CyberNational Cybersecurity Alliance launches HBCU career programLeer másNational Cybersecurity Alliance launches HBCU career program
Intel Selects Check Point Quantum IoT Protect for RISC-V Platform
Intel Selects Check Point Quantum IoT Protect for RISC-V PlatformIoT device manufacturers can now incorporate security at the start of the product life-cycleLeer másIoT device manufacturers...
Three campaigns delivering multiple malware, including ModernLoader and XMRig miner
Three campaigns delivering multiple malware, including ModernLoader and XMRig minerResearchers spotted three campaigns delivering multiple malware, including ModernLoader, RedLine Stealer, and cryptocurrency miners Cisco Talos researchers...
A new Google bug bounty program now covers Open Source projects
A new Google bug bounty program now covers Open Source projectsGoogle this week launched a new bug bounty program that covers the open source projects of...
Russian streaming platform Start discloses a data breach impacting 7.5M users
Russian streaming platform Start discloses a data breach impacting 7.5M usersThe Russian subscription-based streaming service Start discloses a data breach affecting 7.5 million users. The Russian...