UK Spies Fund New Course for Female CodersGCHQ wants to improve diversity for better resultsLeer másGCHQ wants to improve diversity for better results
Day: August 30, 2022
FBI: Hackers Are Exploiting DeFi Bugs to Steal Funds
FBI: Hackers Are Exploiting DeFi Bugs to Steal FundsUsers of decentralized finance platforms at riskLeer másUsers of decentralized finance platforms at risk
New Go-based Ransomware ‘Agenda’ Delivers Customized Attacks
New Go-based Ransomware 'Agenda' Delivers Customized AttacksAgenda can reboot systems in safe mode and stop many server-specific processes and servicesLeer másAgenda can reboot systems in safe...
Google Launches Major Open Source Bug Bounty Program
Google Launches Major Open Source Bug Bounty ProgramInitiative is part of $10bn commitment to improve cybersecurityLeer másInitiative is part of $10bn commitment to improve cybersecurity
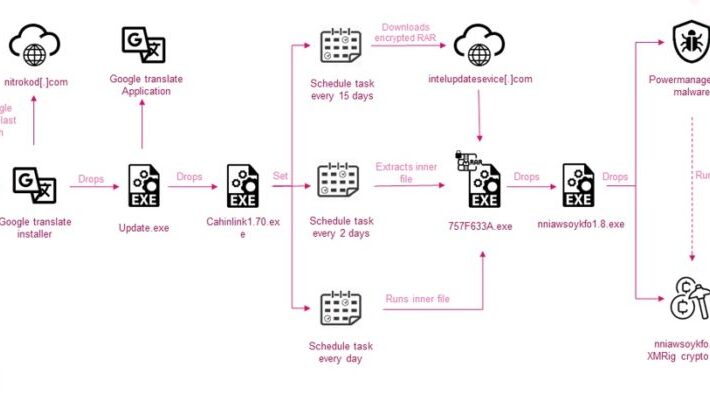
Nitrokod crypto miner infected systems across 11 countries since 2019
Nitrokod crypto miner infected systems across 11 countries since 2019Researchers spotted a Turkish-based crypto miner malware campaign, tracked as Nitrokod, which infected systems across 11 countries....
US FTC sued US data broker Kochava for selling sensitive and geolocation data
US FTC sued US data broker Kochava for selling sensitive and geolocation dataThe U.S. FTC sued US data broker Kochava for selling sensitive and precise geolocation...
Twilio breach let attackers access Authy two-factor accounts of 93 users
Twilio breach let attackers access Authy two-factor accounts of 93 usersThreat actors behind the Twilio hack also gained access to the accounts of 93 individual users...
World’s largest distributors of books Baker & Taylor hit by ransomware
World’s largest distributors of books Baker & Taylor hit by ransomwareBaker & Taylor, one of the world’s largest distributors of books, revealed that it was hit...
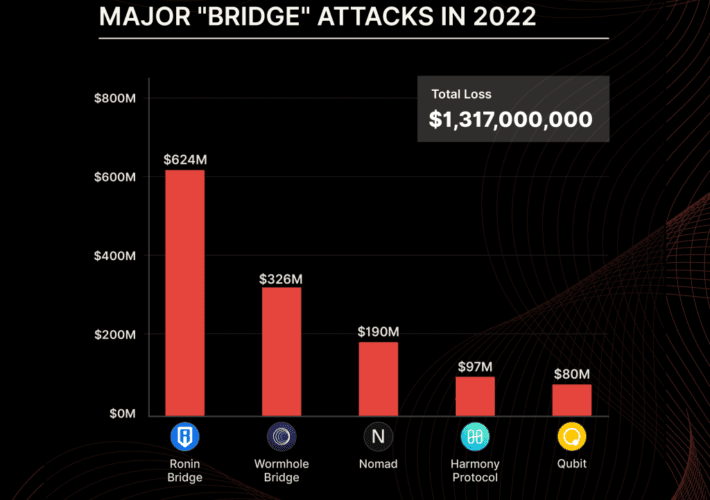
Crooks are increasingly targeting DeFi platforms to steal cryptocurrency
Crooks are increasingly targeting DeFi platforms to steal cryptocurrencyThe U.S. FBI warns investors that crooks are increasingly exploiting security issues in Decentralized Finance (DeFi) platforms to...
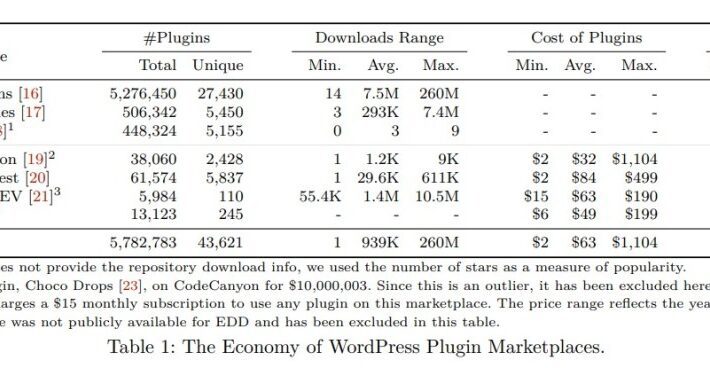
A study on malicious plugins in WordPress Marketplaces
A study on malicious plugins in WordPress MarketplacesA group of researchers from the Georgia Institute of Technology discovered malicious plugins on tens of thousands of WordPress...
LockBit Malware Group Threatens with Triple Extortion
LockBit Malware Group Threatens with Triple ExtortionLockBit ransomware gang – a ransomware operation that has been active for almost three years now listing over 700 victims...
Cryptocurrency Mining Campaign Goes Undetected Since 2019
Cryptocurrency Mining Campaign Goes Undetected Since 2019An ongoing cryptocurrency mining campaign that developed undetected since 2019 has been attributed to a Turkish-speaking agent called Nitrokod. The...
Content Anarchy: The Lurking Security Risk in A Digital-First World
Content Anarchy: The Lurking Security Risk in A Digital-First WorldBy Ellen Benaim, Chief Information Security Officer, Templafy More than two years since the onset of the...
Collective Resilience in an Era of Data Traps, Digital Borders, and Techtonic Geopolitical Shifts
Collective Resilience in an Era of Data Traps, Digital Borders, and Techtonic Geopolitical ShiftsBy Andrea Little Limbago, SVP Research & Analysis, Interos The technological explosion of...
Crisis Point
Crisis PointHow the skills shortage is threatening cyber security By Jamal Elmellas, COO, Focus-on-Security Finding sufficient talent has been […] The post Crisis Point appeared first...
What Is Malware? Malware Types to Watch Out For
What Is Malware? Malware Types to Watch Out For Malware stands for malicious software and denotes software that is designed to execute computer instructions that are...
Boots lets down its customers, by only offering SMS-based 2FA
Boots lets down its customers, by only offering SMS-based 2FAI must admit I was delighted to receive an email today from UK high street pharmacy Boots...
Levels of Assurance for DoD Microelectronics
Levels of Assurance for DoD MicroelectronicsThe NSA has has published criteria for evaluating levels of assurance required for DoD microelectronics. The introductory report in a DoD...
FTC Sues Data Broker
FTC Sues Data BrokerThis is good news: The Federal Trade Commission (FTC) has sued Kochava, a large location data provider, for allegedly selling data that the...
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel Sectors
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel SectorsContenido de la entradaLeer másProofpoint News Feed
Announcing Google’s Open Source Software Vulnerability Rewards Program
Announcing Google’s Open Source Software Vulnerability Rewards ProgramPosted by Francis Perron, Open Source Security Technical Program Manager, and Krzysztof Kotowicz, Information Security Engineer Today, we are...
NIST’s Expanding International Engagement on Cybersecurity
NIST’s Expanding International Engagement on CybersecurityIn providing a foundation for cybersecurity advancements over the years, NIST has taken the global context into account when determining priorities...
Google launches open-source software bug bounty program
Google launches open-source software bug bounty programGoogle will now pay security researchers to find and report bugs in the latest versions of Google-released open-source software (Google...
6 different types of CISOs and the environments they thrive in
6 different types of CISOs and the environments they thrive inEXECUTIVE SUMMARY: The CISO’s role is to protect the business from cyber threats, but often times...
CVE-2022-2560: CompleteFTP Directory Traversal Arbitrary File Deletion Flaw
CVE-2022-2560: CompleteFTP Directory Traversal Arbitrary File Deletion FlawA high EnterpriseDT CompleteFTP vulnerability (CVE-2022-2560), which was discovered by rgod on Jun 7, 2022, just goes public today...
CVE-2022-31656: critical auth bypass flaw in multiple VMware products
CVE-2022-31656: critical auth bypass flaw in multiple VMware productsVMware on Tuesday announced patches for several critical and high-severity vulnerabilities affecting VMware Workspace ONE Access, Identity Manager,...
GUEST ESSAY: Stolen logons, brute force hacking get used the most to breach web, email servers
GUEST ESSAY: Stolen logons, brute force hacking get used the most to breach web, email serversWeb application attacks directed at organizations’ web and mail servers continue...
Black Hat Fireside Chat: Taking the fight to the adversaries — with continuous, proactive ‘pen tests’
Black Hat Fireside Chat: Taking the fight to the adversaries — with continuous, proactive ‘pen tests’Penetration testing – pen tests – traditionally have been something companies...
Receipt for €8M iOS Zero-Day Sale Pops Up on Dark Web
Receipt for €8M iOS Zero-Day Sale Pops Up on Dark WebDocuments appear to show that Israeli spyware company Intellexa sold a full suite of services around...
A Peek Into CISA’s Post-Quantum Cryptography Roadmap
A Peek Into CISA's Post-Quantum Cryptography RoadmapTo help organizations with their plans, NIST and the Department of Homeland Security developed the Post-Quantum Cryptography Roadmap.Leer másDark ReadingTo...