NTLMv1 vs NTLMv2: Digging into an NTLM Downgrade AttackOverview During the summer, my colleague Derya Yavuz and I published an article on some of the different...
Day: August 30, 2022
BSidesTLV 2022 – Keren Elazari’s ‘Closing Remarks’
BSidesTLV 2022 – Keren Elazari’s ‘Closing Remarks’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's YouTube channel. Permalink The post BSidesTLV 2022...
Establishing trust in your software supply chain with an SBOM
Establishing trust in your software supply chain with an SBOM A software Bill of Materials or SBOM provides transparency into an organization’s software, protecting it from...
Smart Cities Need to Keep Cybersecurity in Mind – Techstrong TV
Smart Cities Need to Keep Cybersecurity in Mind – Techstrong TV Karen, Senior Cybersecurity Strategist at VMware, and Charlene discuss smart city cybersecurity—why security is not...
3 Truths about the State of CRQ
3 Truths about the State of CRQI had an exciting time attending Blackhat 2022 in Last Vegas. Blackhat is great each year, but this year was...
Video: 5 P’s to Start Quantitative Risk Management – No 2 People
Video: 5 P’s to Start Quantitative Risk Management – No 2 People At RiskLens, we call our playbook for launching a cyber risk quantification (CRQ) program...
0ktapus/‘Scatter Swine’ Hacking Gang Stole 10,000 Corp Logins via Twilio
0ktapus/‘Scatter Swine’ Hacking Gang Stole 10,000 Corp Logins via Twilio More on the Twilio débâcle from earlier this month: Researchers reveal the hackers swiped at least 9,931...
Why Do You Need a WAF For Your Websites?
Why Do You Need a WAF For Your Websites?Businesses have to worry about different kinds of cyberattacks, many of which could bring down their websites, wipe...
Qualys Discovers Two Major Vulnerabilities – Techstrong TV
Qualys Discovers Two Major Vulnerabilities – Techstrong TV Bharat Jogi, Director of Security and Threat Research at Qualys, discusses the discovery of two recent vulnerabilities, the...
JavaScript bugs aplenty in Node.js ecosystem – found automatically
JavaScript bugs aplenty in Node.js ecosystem – found automaticallyHow to get the better of bugs in all the possible packages in your supply chain?Leer másNaked SecurityHow...
Hands-on Review: Stellar Cyber Security Operations Platform for MSSPs
Hands-on Review: Stellar Cyber Security Operations Platform for MSSPsAs threat complexity increases and the boundaries of an organization have all but disappeared, security teams are more...
Hackers Use ModernLoader to Infect Systems with Stealers and Cryptominers
Hackers Use ModernLoader to Infect Systems with Stealers and CryptominersAs many as three disparate but related campaigns between March and Jun 2022 have been found to...
Importance of being agile & the necessary ingredients
Importance of being agile & the necessary ingredientsFraud represents an asymmetric challenge. A fast reaction time plays an important role in minimizing the attacker’s advantage and...
What is mobile security?
What is mobile security?The use of smartphones has surged, but the users’ knowledge regarding the security of mobile devices has not kept pace with this uptick....
Automatic Restoration of Corrupted UPX-packed Samples
Automatic Restoration of Corrupted UPX-packed SamplesIn this blog, we share a tool (available on Git Hub) that can automatically fix various types of tampered UPX-packed files...
Pondurance Innovations and Integrations for Cloud Security
Pondurance Innovations and Integrations for Cloud SecurityCloud computing has created the biggest tectonic shift in IT this century. It has reshaped and optimized the process of...
Educational institutions and students on hacker’s radar
Educational institutions and students on hacker’s radarOver the last two months, hackers have stepped up attacks on academic institutions and students thereby opening a new frontier...
Consistent Authentication and Device Posture policies for SaaS
Consistent Authentication and Device Posture policies for SaaSThe adoption of SaaS (Software as a Service) started as far back as the 1960s, but picked up steam...
New Golang-based ‘Agenda Ransomware’ Can Be Customized For Each Victim
New Golang-based 'Agenda Ransomware' Can Be Customized For Each VictimA new ransomware strain written in Golang dubbed "Agenda" has been spotted in the wild, targeting healthcare...
FTC Sues Data Broker Over Selling Location Data for Hundreds of Millions of Phones
FTC Sues Data Broker Over Selling Location Data for Hundreds of Millions of PhonesThe U.S. Federal Trade Commission (FTC) on Monday said it filed a lawsuit...
FBI Warns Investors to Take Precautions with Decentralized Financial Platforms
FBI Warns Investors to Take Precautions with Decentralized Financial PlatformsThe U.S. Federal Bureau of Investigation (FBI) on Monday warned of cyber criminals increasingly exploiting flaws in...
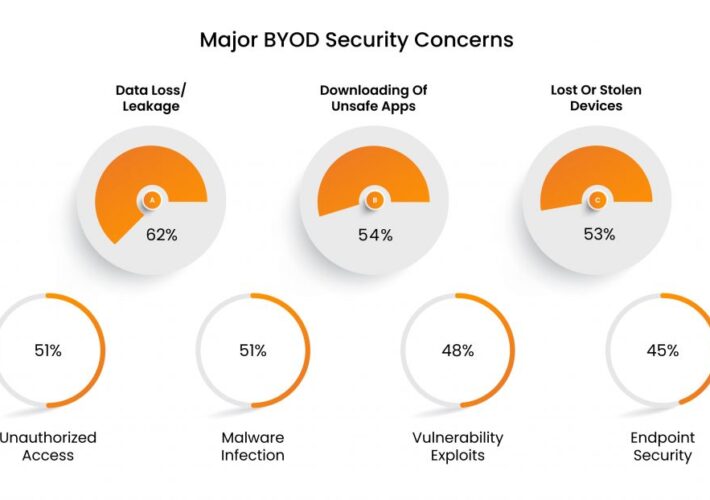
The Emergence Of BYOD: Are Personal Devices Acceptable?
The Emergence Of BYOD: Are Personal Devices Acceptable?To bring or not to ‘bring your own device’ to work, that is the question! During COVID-19, when organizations...
India’s Newest Airline Akasa Air Found Leaking Passengers’ Personal Information
India's Newest Airline Akasa Air Found Leaking Passengers' Personal InformationAkasa Air, India's newest commercial airline, exposed the personal data belonging to its customers that the company...
Forrester: CISO Budgets Not Immune to Cuts
Forrester: CISO Budgets Not Immune to Cuts With looming pullbacks in enterprise technology budgets—including, potentially, security budgets—despite rising digital attacks, regulatory pressure, increasing enterprise business-technology architectural...
LastPass source code breach – do we still recommend password managers?
LastPass source code breach – do we still recommend password managers?What does the recent LastPass breach mean for password managers? Just a bump in the road,...
Why It’s Important to Take Notice of AWS IAM Roles Anywhere
Why It’s Important to Take Notice of AWS IAM Roles Anywhere IAM Roles Anywhere may be a pivotal moment for security; it lets you enrich the arsenal...
Sophisticated BEC scammers bypass Microsoft 365 multi-factor authentication
Sophisticated BEC scammers bypass Microsoft 365 multi-factor authenticationBusiness email compromise (BEC) attacks, where hackers hijack finance-related email threads and trick employees into wiring money to the...
Confessions of a Network Engineer – Remote Access VPNs
Confessions of a Network Engineer – Remote Access VPNs In 2001, I joined a global retailer based in the Pacific Northwest as a network engineer. My...
Critical hole in Atlassian Bitbucket allows any miscreant to hijack servers
Critical hole in Atlassian Bitbucket allows any miscreant to hijack serversGrab and deploy this backend update if you offer even repo read access A critical command-injection...
Google Play to ban Android VPN apps from interfering with ads
Google Play to ban Android VPN apps from interfering with adsDevelopers say this is not the privacy protection it's made out to be Google in November...