Twilio Hackers Scarf 10K Okta Credentials in Sprawling Supply-Chain AttackThe "0ktapus" cyberattackers set up a well-planned spear-phishing effort that affected at least 130 orgs beyond Twilio...
Day: August 29, 2022
Capital One Joins Open Source Security Foundation
Capital One Joins Open Source Security FoundationOpenSSF welcomes Capital One as a premier member affirming its commitment to strengthening the open source software supply chain.Read MoreDark...
Endpoint Protection / Antivirus Products Tested for Malware Protection
Endpoint Protection / Antivirus Products Tested for Malware ProtectionSix out of the eight products achieved an "A" rating or higher for blocking malware attacks. Reports are...
How DevSecOps Empowers Citizen Developers
How DevSecOps Empowers Citizen DevelopersDevSecOps can help overcome inheritance mentality, especially in low- and no-code environments.Read MoreDark ReadingDevSecOps can help overcome inheritance mentality, especially in low-...
‘No-Party’ Data Architectures Promise More Control, Better Security
'No-Party' Data Architectures Promise More Control, Better SecurityConsumers gain control of their data while companies build better relationships with their customers — but third-party ad-tech firms...
‘Sliver’ Emerges as Cobalt Strike Alternative for Malicious C2
'Sliver' Emerges as Cobalt Strike Alternative for Malicious C2Microsoft and others say they have observed nation-state actors, ransomware purveyors, and assorted cybercriminals pivoting to an open...
LastPass Suffers Data Breach, Source Code Stolen
LastPass Suffers Data Breach, Source Code StolenResearchers warned that cyberattackers will be probing the code for weaknesses to exploit later.Read MoreDark ReadingResearchers warned that cyberattackers will...
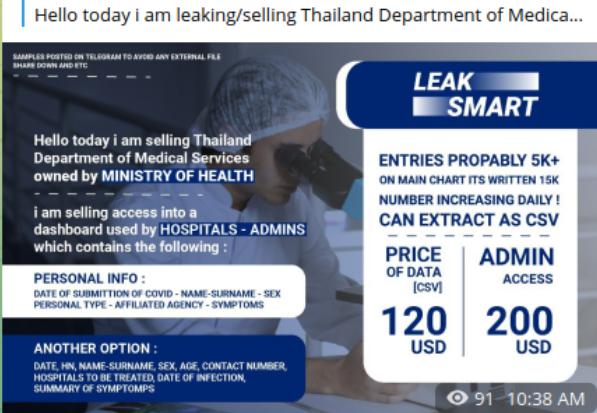
COVID-19 data put for sale on Dark Web
COVID-19 data put for sale on Dark WebResearchers discovered leaked PII stolen from Thailand’s Department of Medical Sciences containing information about citizens with COVID-19. Resecurity, a...
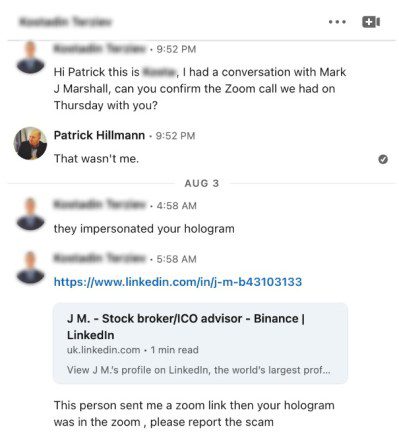
Scammers used a deepfake AI hologram of Binance executive to scam crypto projects
Scammers used a deepfake AI hologram of Binance executive to scam crypto projectsScammers used a deepfake AI hologram of the Binance chief communications officer for fraudulent...
CISA adds 10 new flaws to its Known Exploited Vulnerabilities Catalog
CISA adds 10 new flaws to its Known Exploited Vulnerabilities CatalogThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) added 10 new flaws to its Known Exploited Vulnerabilities...
Janet Jackson Can Crash Laptops, Credential Phishing Attacks Skyrocket, A Phone Carrier That Doesn’t Track You
Janet Jackson Can Crash Laptops, Credential Phishing Attacks Skyrocket, A Phone Carrier That Doesn’t Track YouJanet Jackson’s “Rhythm Nation” has been recognized as an exploit for...
Extra, Extra, VERT Reads All About It: Cybersecurity News for the Week of August 22, 2022
Extra, Extra, VERT Reads All About It: Cybersecurity News for the Week of August 22, 2022All of us at Tripwire’s Vulnerability Exposure and Research Team (VERT)...
Your DevOps Process Needs to Integrate API Security
Your DevOps Process Needs to Integrate API Security If your organization relies on the cloud, you also rely on APIs. “Whatever the project of the day...
OpenText/Micro Focus Deal Signals New Phase of Consolidation
OpenText/Micro Focus Deal Signals New Phase of Consolidation After 30 years in and around the security industry, it’s no surprise to me that business cycles repeat...
CISA Adds 10 New Known Actively Exploited Vulnerabilities to its Catalog
CISA Adds 10 New Known Actively Exploited Vulnerabilities to its CatalogThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added 10 new actively exploited vulnerabilities...
A CISO’s Ultimate Security Validation Checklist
A CISO's Ultimate Security Validation ChecklistIf you're heading out of the office on a well-deserved vacation, are you certain the security controls you have in place...
Twilio Breach Also Compromised Authy Two-Factor Accounts of Some Users
Twilio Breach Also Compromised Authy Two-Factor Accounts of Some UsersTwilio, which earlier this month became a sophisticated phishing attack, disclosed last week that the threat actors also...
Nitrokod Crypto Miner Infected Over 111,000 Users with Copies of Popular Software
Nitrokod Crypto Miner Infected Over 111,000 Users with Copies of Popular SoftwareA Turkish-speaking entity called Nitrokod has been attributed to an active cryptocurrency mining campaign that...
LastPass Admits Hackers Stole Source Code, Proprietary Tech Info
LastPass Admits Hackers Stole Source Code, Proprietary Tech Info The last thing any company that makes its living from security wants is a security incident, but...
BSidesTLV 2022 – Rani Hod’s ‘How Not To Encrypt Your Files’
BSidesTLV 2022 – Rani Hod’s ‘How Not To Encrypt Your Files’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's YouTube channel. Permalink...
Exposing a Compilation of Known Ransomware Group’s Dark Web Onion Web Sites – An OSINT Analysis
Exposing a Compilation of Known Ransomware Group’s Dark Web Onion Web Sites – An OSINT Analysis Dear blog readers, I've decided to share with everyone some...
Will Voluntary CISA Cyber Goals Be Enough to Protect Critical Infrastructure?
Will Voluntary CISA Cyber Goals Be Enough to Protect Critical Infrastructure?The Cybersecurity and Infrastructure Security Agency is getting pushback from critical infrastructure owners and operators on...
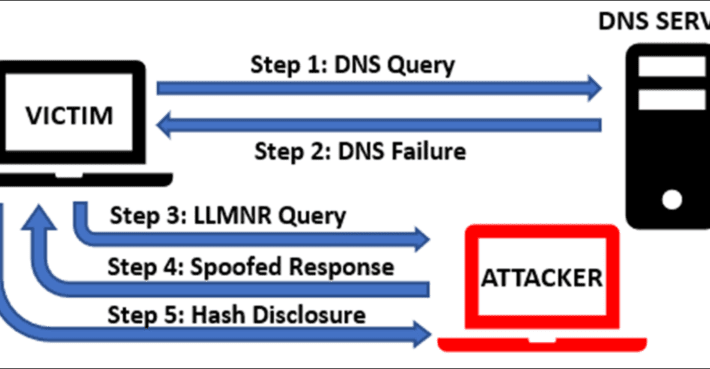
How to Prevent High Risk Authentication Coercion Vulnerabilities
How to Prevent High Risk Authentication Coercion VulnerabilitiesMost of us already know the basic principle of authentication, which, in its simplest form, helps us to identify...
BSidesTLV 2022 – Philip Tsukerman’s And Amir Kutcher’s ‘Unmasked! – Fighting Stealthy Execution Methods Using Process Creation Properties’
BSidesTLV 2022 – Philip Tsukerman’s And Amir Kutcher’s ‘Unmasked! – Fighting Stealthy Execution Methods Using Process Creation Properties’Our thanks to BSidesTLV for publishing their outstanding conference...
Key Points from the IBM Cost of a Data Breach Report 2022
Key Points from the IBM Cost of a Data Breach Report 2022The volume and impact of data breaches have accelerated largely in 2022, which has contributed...
Twilio hackers also breached the food delivery firm DoorDash
Twilio hackers also breached the food delivery firm DoorDashTwilio hackers also compromised the food delivery firm DoorDash, the attackers had access to company data, including customer...
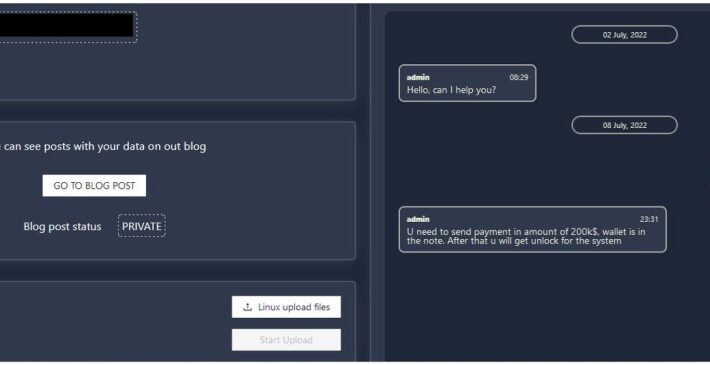
New Agenda Ransomware appears in the threat landscape
New Agenda Ransomware appears in the threat landscapeTrend Micro researchers warn of a new ransomware family called Agenda, which has been used in attacks on organizations...
Security Affairs newsletter Round 381
Security Affairs newsletter Round 381A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
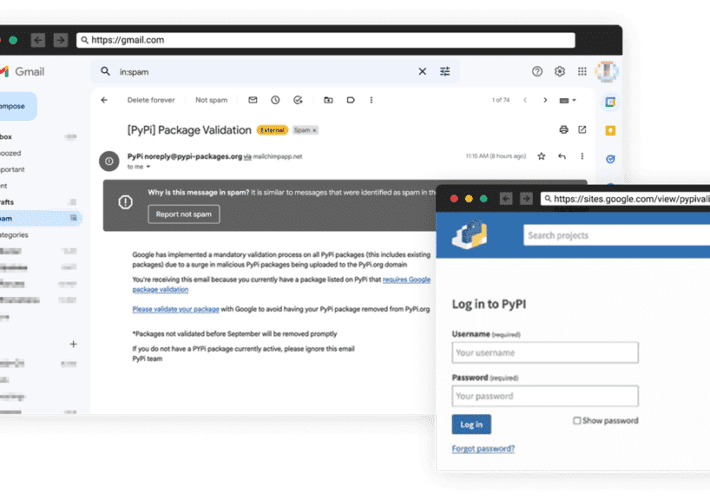
Experts warn of the first known phishing attack against PyPI
Experts warn of the first known phishing attack against PyPIThe Python Package Index (PyPI) warns of an ongoing phishing campaign to steal developer credentials and distribute...
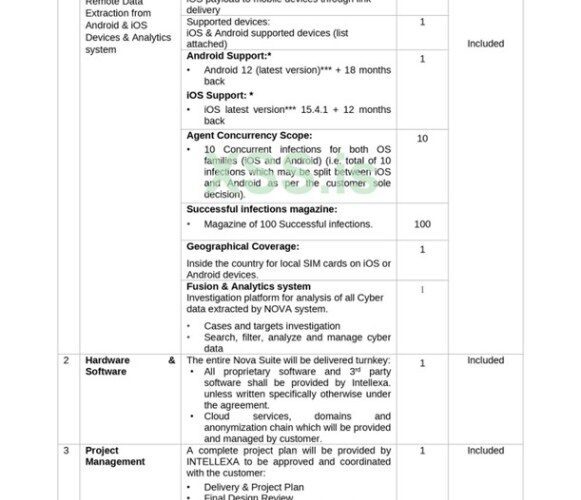
Surveillance firm’s leaked docs show the purchase of an $8M iOS RCE zero-day exploit
Surveillance firm’s leaked docs show the purchase of an $8M iOS RCE zero-day exploitLeaked documents show the surveillance firm Intellexa offering exploits for iOS and Android...