Nobelium APT uses new Post-Compromise malware MagicWebRussia-linked APT group Nobelium is behind a new sophisticated post-exploitation malware tracked by Microsoft as MagicWeb. Microsoft security researchers discovered...
Day: August 27, 2022
LastPass data breach: threat actors stole a portion of source code
LastPass data breach: threat actors stole a portion of source codePassword management software firm LastPass has suffered a data breach, threat actors have stole source code...
0ktapus phishing campaign: Twilio hackers targeted other 136 organizations
0ktapus phishing campaign: Twilio hackers targeted other 136 organizationsThe threat actors behind Twilio and Cloudflare attacks have been linked to a phishing campaign that targeted other 136 organizations. The...
GoldDragon campaign: North-Korea linked Kimsuky APT adopts victim verification technique
GoldDragon campaign: North-Korea linked Kimsuky APT adopts victim verification techniqueThe North Korea-linked Kimsuky APT is behind a new campaign, tracked as GoldDragon, targeting political and diplomatic...
CISA Releases Guidelines to Aid Companies Transition to Post-quantum Cryptography
CISA Releases Guidelines to Aid Companies Transition to Post-quantum CryptographyThe guide provides overview of potential impacts of quantum computing on National Critical FunctionsLeer másThe guide provides...
Iran-linked Mercury APT exploited Log4Shell in SysAid Apps for initial access
Iran-linked Mercury APT exploited Log4Shell in SysAid Apps for initial accessAn Iran-linked Mercury APT group exploited the Log4Shell vulnerability in SysAid applications for initial access to...
Talos Renews Cybersecurity Support For Ukraine on Independence Day
Talos Renews Cybersecurity Support For Ukraine on Independence DayCisco and Talos both have resources available to organizations in Ukraine in need of assistanceLeer másCisco and Talos...
HavanaCrypt Ransomware Detection: New Ransomware Family Wreaks Havoc
HavanaCrypt Ransomware Detection: New Ransomware Family Wreaks Havoc A new ransomware package dubbed HavanaCrypt quickly catapulted into operation earlier this summer and has already caused a...
Microsoft Attributes New Post-Compromise Capability to Nobelium
Microsoft Attributes New Post-Compromise Capability to NobeliumMagicWeb improves on FoggyWeb by facilitating covert access directly via a malicious DLLLeer másMagicWeb improves on FoggyWeb by facilitating covert...
Critical flaw impacts Atlassian Bitbucket Server and Data Center
Critical flaw impacts Atlassian Bitbucket Server and Data CenterAtlassian addressed a critical vulnerability in Bitbucket Server and Data Center that could lead to malicious code execution on vulnerable...
LastPass Hackers Stole Source Code
LastPass Hackers Stole Source CodePassword management firm reveals incident in early AugustLeer másPassword management firm reveals incident in early August
Threat actor abuses Genshin Impact Anti-Cheat driver to disable antivirus
Threat actor abuses Genshin Impact Anti-Cheat driver to disable antivirusThreat actors abused a vulnerable anti-cheat driver for the Genshin Impact video game to disable antivirus software....
Block Faces Class Action Suit After 2021 Breach
Block Faces Class Action Suit After 2021 BreachPlaintiffs argue firm’s security posture was ineffectiveLeer másPlaintiffs argue firm’s security posture was ineffective
Weekly Update 310
Weekly Update 310By all accounts, this was one of the best weekly updates ever courtesy of a spam caller giving me a buzz at the 38:40...
Unprecedented cyber attack hit State Infrastructure of Montenegro
Unprecedented cyber attack hit State Infrastructure of MontenegroThe state Infrastructure of Montenegro was hit by a massive and “unprecedented” cyber attack, authorities announced. An unprecedented cyber...
Cosmetics Giant Sephora to Pay $1m+ Privacy Settlement
Cosmetics Giant Sephora to Pay $1m+ Privacy SettlementCalifornia’s data protection law bares its teethLeer másCalifornia’s data protection law bares its teeth
0ktapus Phishing Campaign Targets Okta Identity Credentials
0ktapus Phishing Campaign Targets Okta Identity CredentialsDespite using low-skill methods, the campaign compromised a large number of well-known companiesLeer másDespite using low-skill methods, the campaign compromised...
TeamTNT Targeted Cloud Instances and Containerized Environments For Two Years
TeamTNT Targeted Cloud Instances and Containerized Environments For Two YearsThe hacking group most likely originates from GermanyLeer másThe hacking group most likely originates from Germany
Iran-Based MuddyWater Targets Log4j 2 Vulnerabilities in SysAid Apps in Israel
Iran-Based MuddyWater Targets Log4j 2 Vulnerabilities in SysAid Apps in IsraelIt is the first campaign in which the hacker group exploits SysAid apps as a vector...
Apple flaws put company networks at risk
Apple flaws put company networks at risk Last week, Apple found two zero-day vulnerabilities in both iOS 15.6.1 and iPadOS 15.6.1 that hackers may have actively...
This Week in Malware – 450 Packages and a Phishing Campaign Against PyPI Maintainers
This Week in Malware – 450 Packages and a Phishing Campaign Against PyPI Maintainers This week in malware we discovered and analyzed 450 packages flagged as...
XKCD ‘Tetherball Configurations’
XKCD ‘Tetherball Configurations’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post XKCD ‘Tetherball Configurations’ appeared first on Security...
When to Use Penetration Testing Software, Services, or Both
When to Use Penetration Testing Software, Services, or BothThe post When to Use Penetration Testing Software, Services, or Both appeared first on Digital Defense. The post...
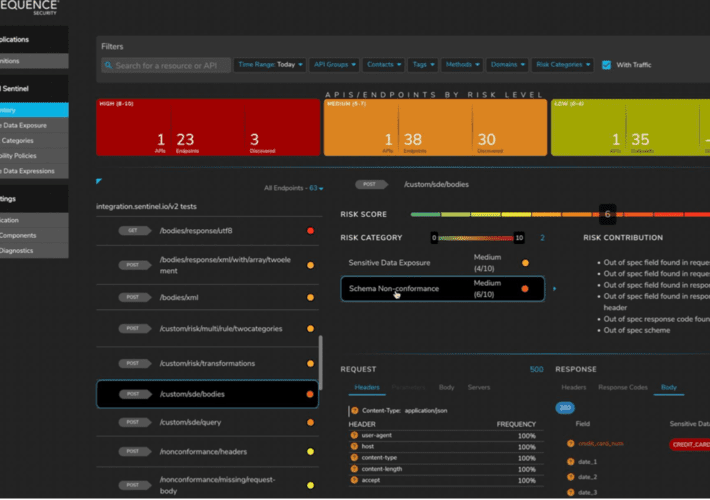
Unified API Protection for Telcos and Mobile Carriers – Time to Value
Unified API Protection for Telcos and Mobile Carriers – Time to ValueLargest Mobile Carrier Identified 4,600 APIs in Days, not Weeks, or Months The security team...
BSidesTLV 2022 – Shira Stepansky’s ‘Diamond Model Analysis Of Whatsapp Security Breach’
BSidesTLV 2022 – Shira Stepansky’s ‘Diamond Model Analysis Of Whatsapp Security Breach’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's YouTube channel....
IAM budget in a recession
IAM budget in a recessionHow to make the most out of your 2023 IAM budget The looming recession is causing the C-suite to re-evaluate spending priorities....
LastPass Breach Raises Disclosure Transparency Concerns
LastPass Breach Raises Disclosure Transparency Concerns In the graphic novel “The Watchman” by Alan Moore and Dave Gibbons, one of the recurring themes is ‘Who watches...
The inevitable pivot to BYOA (Bring Your Own Application): Mitigating risk to enable innovation
The inevitable pivot to BYOA (Bring Your Own Application): Mitigating risk to enable innovationSecurity teams should view BYOA as an opportunity in efficiency and innovation The...
Critical Vulnerability Discovered in Atlassian Bitbucket Server and Data Center
Critical Vulnerability Discovered in Atlassian Bitbucket Server and Data CenterAtlassian has rolled out fixes for a critical security flaw in Bitbucket Server and Data Center that could lead...
Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target Israeli Organizations
Iranian Hackers Exploiting Unpatched Log4j 2 Bugs to Target Israeli OrganizationsIranian state-sponsored actors are leaving no stone unturned to exploit unpatched systems running Log4j to target...