Apple fixed two new zero-day flaws exploited by threat actorsApple addressed two zero-day vulnerabilities, exploited by threat actors, affecting iOS, iPadOS, and macOS devices. Apple this week released security...
Day: August 18, 2022
PoC exploit code for critical Realtek RCE flaw released online
PoC exploit code for critical Realtek RCE flaw released onlineExploit code for a critical vulnerability affecting networking devices using Realtek RTL819x system on a chip released...
Apple fixed two new zero-day flaws exploited by threat actors
Apple fixed two new zero-day flaws exploited by threat actorsApple addressed two zero-day vulnerabilities, exploited by threat actors, affecting iOS, iPadOS, and macOS devices. Apple this week released security...
BlueSky Ransomware Detection: Targets Windows Hosts and Leverages Multithreading for Faster Encryption
BlueSky Ransomware Detection: Targets Windows Hosts and Leverages Multithreading for Faster Encryption BlueSky ransomware represents a rapidly evolving malware family that involves sophisticated anti-analysis capabilities and...
Zeppelin Ransomware Detection: CISA and FBI Issue a Joint Advisory for Enhanced Protection Against RaaS Threats
Zeppelin Ransomware Detection: CISA and FBI Issue a Joint Advisory for Enhanced Protection Against RaaS Threats According to SOC Prime’s Detection as Code Innovation Report covering...
Product Adoption Specialist (US)
Product Adoption Specialist (US)Our Perfect Candidate You are highly disciplined, self-motivated, and influential. You have confidence in prospecting and communicating with C-level executives and advanced technical...
Detecting SEABORGIUM Campaigns: A Cyberespionage Group Targeting Governments, Military, and NGOs Across Europe
Detecting SEABORGIUM Campaigns: A Cyberespionage Group Targeting Governments, Military, and NGOs Across Europe Cybersecurity experts from Microsoft Threat Intelligence Center (MSTIC) have disrupted the infrastructure of...
South Staffordshire Water Confirms Cyberattack
South Staffordshire Water Confirms CyberattackSouth Staffordshire Water, a company that provides 1.6 consumers daily with 330 million liters of drinking water, has confirmed an IT outage...
Safeguarding Industrial Control Systems Environments
Safeguarding Industrial Control Systems EnvironmentsPreventing internal & external cybersecurity breaches with zero trust OT network segmentation By Ryan Lung, Senior product manager […] The post Safeguarding...
Here Comes BlackByte Ransomware 2.0
Here Comes BlackByte Ransomware 2.0The BlackByte ransomware has returned with an advanced version of its operation, including a new data leak website using novel extortion strategies...
It’s Time to Rethink Endpoint Security
It’s Time to Rethink Endpoint SecurityBy Carolyn Crandall, Chief Security Advocate, Attivo Networks Sometimes, organizations change from within, while other times change is […] The post...
SOC Prime Threat Bounty — July 2022 Results
SOC Prime Threat Bounty — July 2022 Results July ‘22 Updates During the previous month, we introduced several improvements to content validation and Sigma Rules Bot...
The Emergence of Dynamic Threat Hunting
The Emergence of Dynamic Threat HuntingA review of the evolving cyber security industry over 15 years in business By James “Jim” McMurry, CEO […] The post...
Securing Your Organization During Global Turmoil
Securing Your Organization During Global TurmoilRepelling Cyber Criminals Trying to Capitalize on a Crisis By Kevin Orr, President, RSA Federal Current geopolitical crises […] The post...
What is Cyber Threat Hunting? The Ultimate Guide
What is Cyber Threat Hunting? The Ultimate Guide Cyber Threat Hunting is a novel approach to Threat Detection which is aimed at finding cyber threats within...
Remotely Controlling Touchscreens
Remotely Controlling TouchscreensThis is more of a demonstration than a real-world vulnerability, but researchers can use electromagnetic interference to remotely control touchscreens. From a news article:...
Zoom Exploit on MacOS
Zoom Exploit on MacOSThis vulnerability was reported to Zoom last December: The exploit works by targeting the installer for the Zoom application, which needs to run...
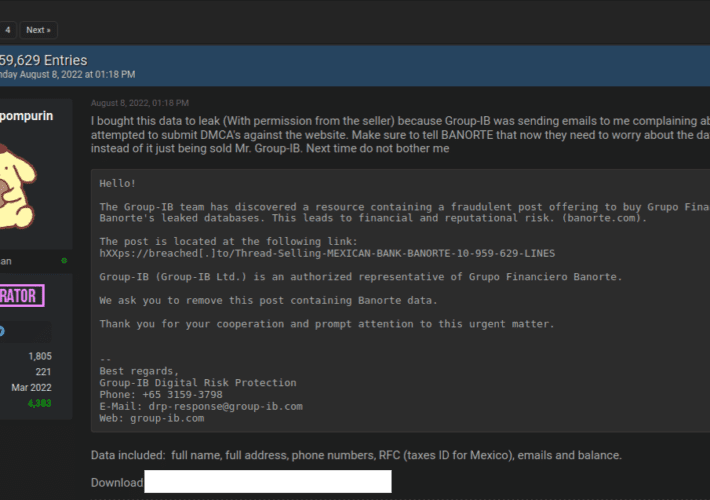
When Efforts to Contain a Data Breach Backfire
When Efforts to Contain a Data Breach BackfireEarlier this month, the administrator of the cybercrime forum Breached received a cease-and-desist letter from a cybersecurity firm. The...
A Parent’s Guide To The Metaverse – Part One
A Parent’s Guide To The Metaverse – Part One We’ve all heard about the Metaverse. And there’s no doubt it has certainly captured the attention of...
Apple security updates fix 2 zero-days used to hack iPhones, Macs
Apple security updates fix 2 zero-days used to hack iPhones, MacsApple has released emergency security updates today to fix two zero-day vulnerabilities previously exploited by attackers...
Africa – the most cyber attacked continent, a 2022 review of trends
Africa – the most cyber attacked continent, a 2022 review of trendsIssam El Haddioui: Head of Security Engineering, EMEA – Africa | Security Evangelist with the...
Kage – Graphical User Interface For Metasploit Meterpreter And Session Handler
Kage – Graphical User Interface For Metasploit Meterpreter And Session HandlerKage (ka-geh) is a tool inspired by AhMyth designed for Metasploit RPC Server to interact with...
Google Chrome Zero-Day Found Exploited in the Wild
Google Chrome Zero-Day Found Exploited in the WildThe high-severity security vulnerability (CVE-2022-2856) is due to improper user-input validation.Leer másDark ReadingThe high-severity security vulnerability (CVE-2022-2856) is due...
TechScape: Why can’t crypto exterminate its bugs?
TechScape: Why can’t crypto exterminate its bugs?‘Provenance hashes’ and bug bounties are supposed to protect platforms. Why do so many flaws in crypto and open-source projects...
Google Cloud Adds Curated Detection to Chronicle
Google Cloud Adds Curated Detection to ChronicleThe curated detection feature for Chronicle SecOps Suite provides security teams with actionable insights on cloud threats and Windows-based attacks...
Discover Cloud Smart Networking and Security at VMware Explore 2022
Discover Cloud Smart Networking and Security at VMware Explore 2022The battleground has shifted dramatically. As networks expand and become more complex with the growth of multi-cloud...
VMware’s Karen Worstell Recognized as 2022 ISSA International Distinguished Fellow
VMware’s Karen Worstell Recognized as 2022 ISSA International Distinguished FellowAt Black Hat USA, VMware senior cybersecurity strategist Karen Worstell was recognized as a 2022 ISSA International...
The Complete Networking Professionals’ Guide to VMware Explore
The Complete Networking Professionals’ Guide to VMware ExploreThe rapid shift from on-premises to the cloud is answering as many questions as it is creating. You need...
The Definitive Security Professionals’ Guide to VMware Explore
The Definitive Security Professionals’ Guide to VMware ExploreAs the architectures used by your organization continue to rapidly evolve with the growth of multi-cloud environments, so do...