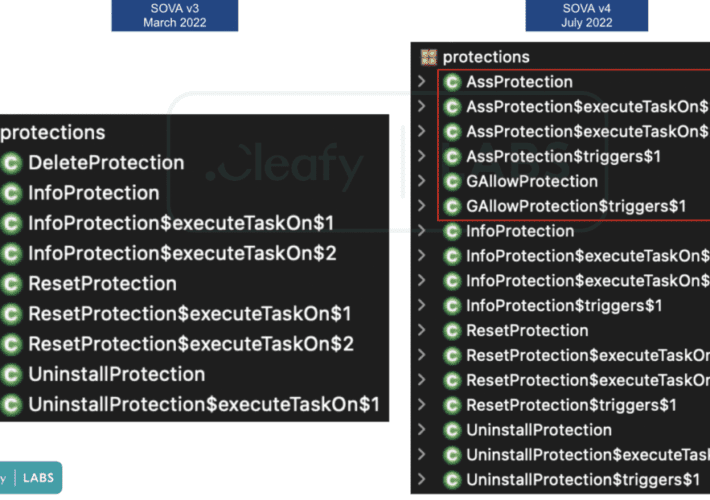
SOVA Android malware now also encrypts victims’ filesSecurity researchers from Cleafy reported that the SOVA Android banking malware is back and is rapidly evolving. The SOVA...
Day: August 15, 2022
Critical Infrastructure at Risk as Thousands of VNC Instances Exposed
Critical Infrastructure at Risk as Thousands of VNC Instances ExposedResearchers find many deployments have authentication disabledLeer másResearchers find many deployments have authentication disabled
Aspen Security Forum 2022 – Moderator: Courtney Kube – Niamh King’s Opening Remarks & National Security Today: Emerging Challenges and Opportunities
Aspen Security Forum 2022 – Moderator: Courtney Kube – Niamh King’s Opening Remarks & National Security Today: Emerging Challenges and OpportunitiesGeneral Richard Clarke, Commander, U.S. Special...
XKCD ‘Coffee Cup Holes’
XKCD ‘Coffee Cup Holes’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post XKCD ‘Coffee Cup Holes’ appeared first...
New Study Reveals Serious Cyber Insurance Shortfalls
New Study Reveals Serious Cyber Insurance ShortfallsMost companies do not have enough coverage to recover from ransomwareLeer másMost companies do not have enough coverage to recover...
Three Extradited from UK to US on $5m BEC Charges
Three Extradited from UK to US on $5m BEC ChargesNigerian nationals accused of targeting US universitiesLeer másNigerian nationals accused of targeting US universities
Aspen Security Forum 2022 – Moderator: Dafna Linzer – The 21st Century Nuclear Arms Race
Aspen Security Forum 2022 – Moderator: Dafna Linzer – The 21st Century Nuclear Arms RaceEmma Belcher, President, Ploughshares Fund Rose Gottemoeller, Former Deputy Secretary General, NATO...
#DEFCON: CISA Director Praises Congress and International Cybersecurity Cooperation
#DEFCON: CISA Director Praises Congress and International Cybersecurity CooperationJen Easterly discusses the progress and challenges at CISALeer másJen Easterly discusses the progress and challenges at CISA
5 tips for spotting and avoiding Pig butchering scams
5 tips for spotting and avoiding Pig butchering scamsA new type of scam, called “pig butchering” is gaining momentum. Pig butchering is a unique scam which...
#DEFCON: How Sanctions Impact Internet Operators
#DEFCON: How Sanctions Impact Internet OperatorsFollowing government sanctions against Russia, Internet providers have had to learn how to implement actionsLeer másFollowing government sanctions against Russia, Internet...
Dutch Authorities Arrest Tornado Cash Developer Following US Sanctions on Crypto Mixer Firm
Dutch Authorities Arrest Tornado Cash Developer Following US Sanctions on Crypto Mixer FirmThe Financial Advanced Cyber Team of the FIOD started the criminal investigation in JuneLeer...
The Importance of Faraday Technology with Aaron Zar from SLNT
The Importance of Faraday Technology with Aaron Zar from SLNTAaron Zar, SLNT founder and director of disconnection joins co-host Tom Eston to discuss the importance of...
Black Hat – Windows isn’t the only mass casualty platform anymore
Black Hat – Windows isn’t the only mass casualty platform anymoreWindows used to be the big talking point when it came to exploits resulting in mass...
Luckymouse Uses Compromised MiMi Chat App to Target Windows and Linux Systems
Luckymouse Uses Compromised MiMi Chat App to Target Windows and Linux SystemsThe news comes from two different security reports published by SEKOIA and Trend MicroLeer másThe...
Software Patches Flaw on macOS Could Let Hackers Bypass All Security Levels
Software Patches Flaw on macOS Could Let Hackers Bypass All Security LevelsAfter deploying the initial attack, the researcher was able to escape the macOS sandboxLeer másAfter...
Black Hat USA 2022: Burnout, a significant issue
Black Hat USA 2022: Burnout, a significant issueThe digital skills gap, especially in cybersecurity, is not a new phenomenon. This problematic is now exacerbate by the...
Comparing Twilio and Slack breach responses
Comparing Twilio and Slack breach responses We recently learned about major security breaches at two tech companies, Twilio and Slack. The manner in which these two...
Top 5 security risks of Open RAN
Top 5 security risks of Open RANWhen a cell phone or other mobile device connects to the nearest cell tower, the communication takes place over something...
Back to School Means More Cyber Concerns
Back to School Means More Cyber ConcernsCyberattacks continue to rise, threatening the educational sector As the 2022-2023 school year looms, so do ongoing cyber threats directly...
Black Hat and DEF CON Roundup
Black Hat and DEF CON Roundup‘Summer Camp’ for hackers features a compromised satellite, a homecoming for hackers and cyberwarfare warnings.Leer másThreatpost‘Summer Camp’ for hackers features a...
The Power of Provenance: From Reactive to Proactive Cybersecurity
The Power of Provenance: From Reactive to Proactive Cybersecurity While next-gen firewalls (NGFW), extended detection and response (XDR) and other security solutions do a great job...
3 ways China’s access to TikTok data is a security risk
3 ways China's access to TikTok data is a security riskThe short-video platform TikTok has come under fire in recent months. Both lawmakers and citizens in...
$23 Million YouTube Royalties Scam
$23 Million YouTube Royalties ScamScammers were able to convince YouTube that other peoples’ music was their own. They successfully stole $23 million before they were caught....
The Week in Cybersecurity: MFA shortcomings paved the way for Cisco breach
The Week in Cybersecurity: MFA shortcomings paved the way for Cisco breach MFA’s shortcomings paved the way for Cisco’s data breach Security Week reports that Cisco released a security...