Source: securityaffairs.com – Author: Pierluigi Paganini
Xenomorph malware is back after months of hiatus and expands the list of targets
Pierluigi Paganini
September 26, 2023

A new campaign is spreading Xenomorph malware to Android users in the United States, Spain, Portugal, Italy, Canada, and Belgium.
Researchers from ThreatFabric uncovered a new campaign spreading Xenomorph malware to Android users in the United States and all over the world.
In February 2022, researchers from ThreatFabric first spotted the Xenomorph malware, which was distributed via the official Google Play Store reaching over 50,000 installations.
The banking Trojan was used to target 56 European banks and steal sensitive information from the devices of their customers. The analysis of the code revealed the presence of not implemented features and the large amount of logging present, a circumstance that suggests that this threat is under active development.
Xenomorph shares similarities with the Alien banking trojan, but it has functionalities radically different from the Alien’s one.
The experts noticed that the was continuously improved during 2022 and was distributed in small campaigns. The operators first distributed the Android malware via the GymDrop dropper operation, later the malicious code was also distributed via the Zombinder operation.
In March, experts warned of a new variant tracked as Xenomorph.C that was significantly improved.
The new variant supports a new automated transfer system (ATS) framework and can target over 400 banks and financial institutions mainly from Spain, Turkey, Poland, the United States, Australia, Canada, Italy, Portugal, France, Germany, UAE, and India.
This new version of the malware adds many new capabilities to an already feature rich Android Banker, most notably the introduction of a very extensive runtime engine powered by Accessibility services, which is used by actors to implement a complete ATS framework. With these new features, Xenomorph is now able to completely automate the whole fraud chain, from infection to funds exfiltration, making it one of the most advanced and dangerous Android Malware trojans in circulation.” reads the report published by Threat Fabric. “In addition, the samples identified by ThreatFabric featured configurations with Target lists made of more than 400 banking and financial institutions, including several cryptocurrency wallets, with an increase of more than 6 times with comparison to its previous variants, including financial institutions from all continents.”
The ATS framework allows operators to automate the exfiltration of credentials, check account balances, conduct transactions, and steal money from target apps without human interaction from an operator.
In August 2023 ThreatFabric discovered new samples distributed via phishing webpages designed to trick recipients into installing malicious APKs. The list of targets is larger than previous versions.
The list adds dozens of new overlays for institutions from the United States, Portugal, and multiple crypto wallets.
The campaign also targeted users in Spain, Portugal, Italy, Canada, and Belgium.
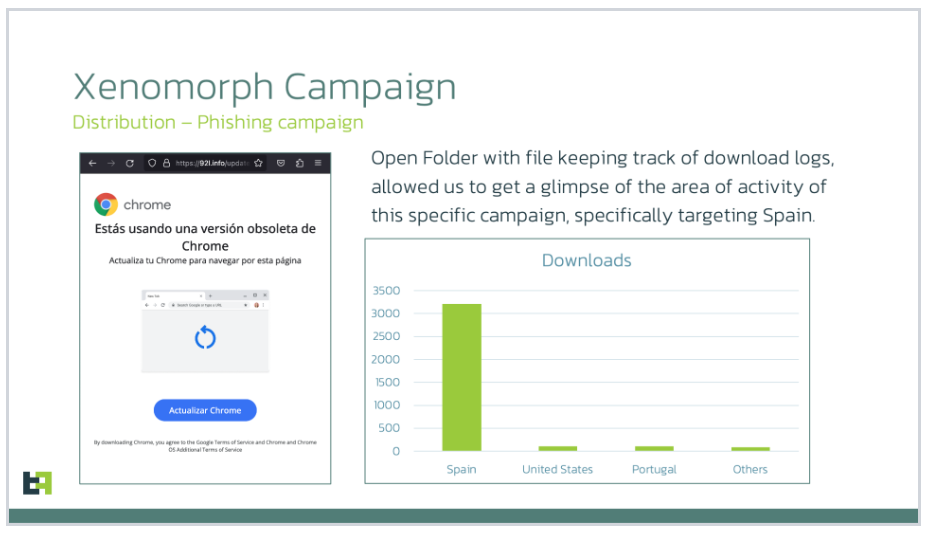
“However, this latest campaign also added plenty of financial institutions from the United States, together with multiple crypto-wallet applications, totaling more than 100 different targets per sample, each one using a specifically crafted overlay to steal precious PII from the victim’s infected device.” reads the report from ThreatFabric. “ThreatFabric was able to identify active campaigns distributing the malware via phishing pages. In these cases, the malware was distributed through phishing pages posing as a Chrome update.“
While investigating the campaign the researchers noticed that threat actors made an important mistake exposing without restrictions the server folder containing the files necessary to distribute the malware.
This allowed the researchers to monitor the server, identifying multiple interesting files.
One of the files, named count.txt, contains a list of entries (IPs, user agents, and dates) that were the list of the targeted systems attempting to download the payload of the phishing page. Most of the downloads were from Spain.

The new samples of Xenomorph do not feature major modifications from their previous iteration. The samples support an Antisleep Feature and a ‘Mimic’ Feature. The latter feature gives the option to the malware to act as any other application and removes one behaviour that is often associated with malware.
Another new feature implemented in the latest sample is “ClickOnPoint,”, which allows the malware to simulate taps at specific screen coordinates.
“Xenomorph, after months of hiatus, is back, and this time with distribution campaigns targeting some regions that have been historically of interest for this family, like Spain or Canada, and adding a large list of targets from the United States, as well as multiple new Cryptowallets.” concludes the report.
“Xenomorph maintains its status as an extremely dangerous Android Banking malware, featuring a very versatile and powerful ATS engine, with multiple modules already created, with the idea of supporting multiple manufacturer’s devices.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
Original Post URL: https://securityaffairs.com/151443/malware/xenomorph-malware-is-back.html
Category & Tags: Breaking News,Cyber Crime,Hacking,Malware,Mobile,Android,Cybercrime,information security news,IT Information Security,malware,mobile,Pierluigi Paganini,Security News,Xenomorph – Breaking News,Cyber Crime,Hacking,Malware,Mobile,Android,Cybercrime,information security news,IT Information Security,malware,mobile,Pierluigi Paganini,Security News,Xenomorph
Views: 0