Source: heimdalsecurity.com – Author: Andra Andrioaie
The principle of least privilege (POLP), also named the “principle of least authority” (POLA) or “the principle of minimal privilege” (POMP), stands for a cybersecurity best practice based upon granting the minimum required access that a user needs to perform an assigned task.
Contrary to popular belief, POLP does not cover only active entities but also passive entities such as processes, systems, and files, in other words, nonuser entities. In simple terms, the concept refers to users, machines, or systems not being able to access information or do actions unless they absolutely must in order to do their jobs or, respectively, perform their tasks.
POLP promotes restrictive access rights in order to mitigate companies’ exposure to cyberattacks by minimizing the connection between users and systems, being a core component of the zero-trust strategies, and guarding the privileged access to assets and data of high-value.
The focus of this article is going to be the concept of least privilege applied to your employees, or in other words, how limiting your users’ rights to the lowest level possible will close security holes in your organization. Therefore, we are going to discuss the principle of least privilege and defense in depth.
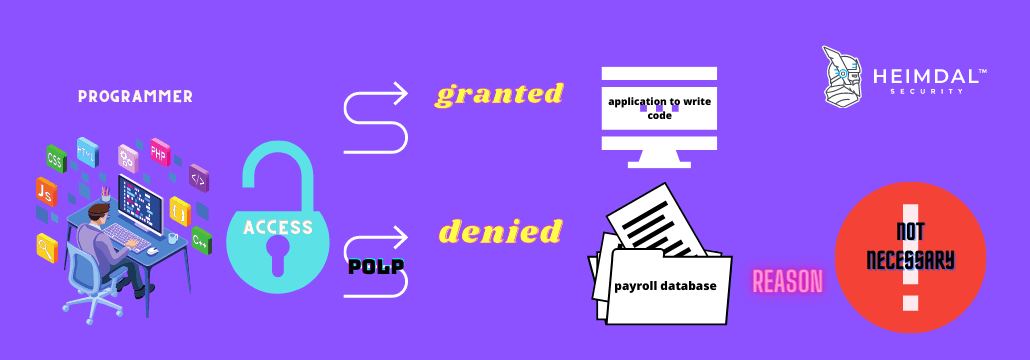
There are 2 major concepts related to POLP:
1. Privilege bracketing
Privilege bracketing refers to the practice of reducing users’ permission levels to the shortest timeframe possible for them to complete a task and afterward de-escalating their rights. Unlike standard user accounts, admin accounts have increased privileges and therefore pose higher risks. From a cybersecurity standpoint, it’s best to grant admin rights to your users only when they actually need them and for the shortest time possible that still enables them to complete their tasks.
2. Privilege creep
Also called permission bloat, the privilege creep or the access creep is a concept that applies to users who gradually gather unnecessary permissions. How can it happen? The behavior commonly occurs in companies where employees change job functions or departments and their user privileges are not modified to reflect their new roles. This way, users end up having redundant privileges for multiple positions.
Benefits of the Principle of Least Privilege
As you can probably already tell, the principle of least privilege is of utmost importance inside any organization. Its purpose is to protect a company’s assets from both potential insider and outsider threats. This way an HR employee that needs permission to the employees’ database would not have access to the finance department’s information and a developer who needs rights to write lines of code would not have permission to pull out employees’ records.
Here are some major benefits of applying the principle of least privilege for your organization:
Decrease the cyberattack surface
For instance, let’s suppose a system has been infected by malware. If this system is part of an organization that follows the principle of least privilege it will not be able to spread to other computers, avoiding SQL injection attacks for instance. This means that you will reduce the chances of viruses, worms, or rootkits being executed since most of your employees will not have the admin rights that enable their installation. Furthermore, since a potentially affected user has limited rights, the malware will not be able to produce any catastrophic damage, such as permanently deleting or downloading proprietary data.
Better security
You wouldn’t think that an employee would do any harm to the corporation he’s working in. Well, statistics say something else.
Statistics from Embroker’s website show that the cause of 20% of cybercrimes is that privileges are misused and 50% of the companies do not protect properly their data having over 1000 confidential documents, out of which 22% are at the disposal of each employee.
Assigning the proper privileges to each user’s job function will prevent malicious employees from stealing data and getting access to confidential information, using it for their own gain, and selling it on the dark web. By enforcing the principle of least privilege, if a user’s credentials get compromised, the cyber attacker will only have limited access to your organization’s resources.
What’s more, the danger of unintentional insider threats can always exist inside your organization. This means that some employees may unknowingly do harm by clicking on phishing links or following instructions received from imposters.
Increased system stability
Enforcing POLP helps you avoid human error. If a user has limited access to resources, he cannot mistakenly delete files or reconfigure something, for instance. Besides, if an application is vulnerable, it will not impact other applications as access is restricted. All these will provide a better system and network stability.
Achieve compliance & enhance audit readiness
By applying POLP in your organization, you can improve audit readiness and at the same time achieve regulatory compliance. Currently, many standards require companies to grant employees only the rights they need to complete their daily operations. However, even if it’s not mandatory for your business to comply with these regulations, keep in mind that as a best practice, the principle of least privilege should always be implemented.
Improved productivity
If users are granted access to an application for a limited amount of time, then it will make them perform the task better and faster, and also the IT guys won’t have to deal with lots of tickets like “I need access there and there. Help me troubleshoot this and that.”
This is linked to the just-in-time privilege elevation measure I am going to talk about later.
Better data classification
The principle of least privilege can also help your company better classify its data. This way, you will always know who has access to what data and where exactly it’s stored in case someone gains unauthorized access.
Practical Examples of the Principle of Least Privilege
On the CISA’s website, there are some examples related to the principle of least privilege, how it is violated and why it should be implemented. I will explain the principle of least privilege by referring to three of them, 2 related to the principle of least privilege as applied to cybersecurity, and one to real life.
In cybersecurity
The most common and relevant example is related to UNIX systems. The flaw lies in the fact that user root access checks are not applied. Thus, users have unlimited access through root permission to read, write or execute files. If the principle of least privilege would have been applied, a user who needs only to do a back-up should not have the right to delete files.
Another good example related to POLP would be represented by programmers. They require more access than needed just in case. So, they will choose the default setting to have excessive rights, because getting restrictive rights could be more challenging and require more steps. This is a violation of the principle.
In real-life
The need-to-know concept used in the U.S. Government clearance system is a real-life principle of least privilege example. This means that people are not allowed to require to see every secret document they are authorized to and know it exists in order to avoid the violation of the clearance level. So, they only have access to what “they need to know” in order to do a specific task.
We can go further and depict a movie’s example:
This might sound funny, but believe me, it is relevant to illustrate the principle of least privilege. Remember Harry Potter’s restricted library sector? Students did not have access to the books there that might contain sensitive information about the dark magic that in hands of an evil-minded student could compromise the security of the school. Students did not need information from the restricted sector to do their daily homework, they only needed access to the usual library. Therefore, the school applied the principle of least privilege.
Best Practices for the Principle of Least Privilege. How to Implement POLP
Here are the top 10 ways on how to implement the principle of least privilege in your organization. Number 10 is the cherry on top of the list which will give you a solution that beats them all.
1) Set up a privilege audit
This is the first step that will allow you to verify all your accounts. This helps you analyze passwords, SSH keys, and access keys. Thus, you can see exactly what permissions have been granted to your users.
2) Define what level of privilege each account needs: Separation of privilege
By default, all accounts should have the lowest level of privileges possible. You should only increase privilege rights as required for certain people to be able to perform their jobs.
What I want to mention here is that there are 2 types of accounts: super-user and standard accounts or technically said least-privileged users (LPUs).
Generally, super-user accounts are used by system admins who demand these privileges. However, the majority of employees who need access only to perform specific routine tasks should not have special and additional accesses, making use of standard user accounts, not super-user ones.
Thus you achieve less exposure to threats by enforcing the separation of privileges and limiting super-user and administrator privileges.
3) Just-in-time access
Here you can apply the concept of privilege bracketing we have talked about at the beginning of the article. This means that privileges should be given to users who absolutely require them to perform their jobs for a limited time only. It’s advisable to use a tool that enables you to escalate and de-escalate your users’ rights and set up expiry times for their privileges.
4) One-time use credentials to avoid the Pass-the-Hash technique
You can perform least privilege enforcement by combining method 3 (just-in-time access) with a digital vault or disposable credentials also called password rotation.
Let’s say Martin needs root privileges twice a year. There is no need to give him access more than twice a year. Because he needs this access so rarely, he can use disposable credentials. This way, you can monitor Martin’s activity much better.
Another solution would be a digital vault. This helps with the safe storage of privileged accounts’ passwords. This measure avoids the Pass the Hash technique where the hacker obtains the password hash and uses it for authentication and lateral access to networks.
5) Use automatic auditing for constant monitoring
And of course, you are not always aware if Martin needs access or you might not remember he needs it twice a year. This leads us to the next least of privilege enforcement method.
Through this method, you can also avoid privilege creep (unnecessary cumulated rights over time) by being constantly aware of what has been run by your users during the time their rights were elevated. This method gives you full in-hand access to audit trails so you can detect and mitigate any unusual activity.
6) Bear in mind the danger of physical devices
In some cases, implementing POLP might be as easy as simply disabling USB ports from your devices so your employees are not able to insert USB drives to download your confidential information or infect your systems with malware.
7) Enforce the principle of least privilege to your third-parties too
Even if you implement the principle of least privilege, your third-party associates may not do so. This only poses a threat to your organization. Make sure that you apply the principle of least privilege to contractors, vendors, and remote sessions and establish if they really are a threat or not.
8) IT accounts should have MFA
Since the IT guys in your company are the most trustworthy people, they are granted super-user accounts as they are sysadmins. Better said, they have unlimited access to perform any action on the network. A multi-factor authentication solution will be a good least privilege enforcement for super-user accounts.
They could also just use admin accounts only for very special tasks and standard ones for daily routine.
9) The network segmentation technique
You can make use of firewall configurations and rules to build various zones. Thus, you can control who moves and has access between zones. Firewalls have the role to stop unauthorized privileged access and create demilitarized zones (DMZ) between a public and a corporate network.
As applied to your employees, this technique helps you separate user groups from services. This way, the information intended to be accessed is seen only by the right people.
10) A privileged access management solution
You’ve probably heard before about Privilege Access Management (PAM). Generally efficient, the methods I listed above can at the same time not be enough.
The good news is that we have a better solution. You can now implement the principle of least privilege by using our Privileged Access Management (PAM) solution. Why is Heimdal PAM better than everything and what does it do? Because it is the only tool that both escalates and de-escalates users’ rights and at the same time makes you achieve two vital things: full compliance, being NIST AC-1,6 compliant, and also increased productivity. A cool centralized dashboard will allow your sysadmins to manage access granting efficiently and offer you a complete overview of your users’ activity.
This being said, the truth is that you need PAM. What is better than you being the one in control of everything? You make constant efforts to better secure your company and keep the business protected and thriving, so you deserve the finest solution. Our solution is just one click away. We succeed where others fail!
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Wrapping up…
The importance of Principle of Least Privilege (PoLP) cannot be emphasized enough in this age of increasing cyber threats. It limits access to sensitive information by ensuring only the authorized users have access. Making PoLP an integral part of a company’s privileged access management policy can mitigate risk, fortify security controls and counter potential threats. Following these guidelines helps organizations keep their data secure while granting their employees only the required system access for their job roles. Various tools are available to make it easier to apply this principle in your organization, so take advantage of them and remain alert when it comes to safeguarding your data!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/what-is-the-principle-of-least-privilege-polp/
Category & Tags: Access Management,Cybersecurity Basics,PAM,POLP,principle of least privilege,privileged access management – Access Management,Cybersecurity Basics,PAM,POLP,principle of least privilege,privileged access management
Views: 1





















































