Source: www.bleepingcomputer.com – Author: Bill Toulas

An estimated 12,000 Juniper SRX firewalls and EX switches are vulnerable to a fileless remote code execution flaw that attackers can exploit without authentication.
In August, Juniper disclosed numerous ‘PHP environment variant manipulation’ (CVE-2023-36844/CVE-2023-36845) and ‘Missing Authentication for Critical Function’ (CVE-2023-36846/CVE-2023-36847) vulnerabilities that by themselves only had a ‘medium’ severity rating of 5.3.
However, when chained together, these vulnerabilities became a critical remote code execution flaw with a rating of 9.8.
In a later technical report, watchTowr Labs released a PoC that chained the CVE-2023-36845 and CVE-2023-36846 flaws, allowing the researchers to remotely execute code by uploading two files to a vulnerable device.
Today, VulnCheck vulnerability researcher Jacob Baines released another PoC exploit that only utilizes CVE-2023-36845, bypassing the need to upload files while still achieving remote code execution.
As part of Baines’ report, the researcher shared a free scanner on GitHub to help identify vulnerable deployments, showing thousands of vulnerable devices exposed on the internet.
“In this blog, we demonstrated how CVE-2023-36845, a vulnerability flagged as “Medium” severity by Juniper, can be used to remotely execute arbitrary code without authentication,” explains VulnCheck’s report.
“We’ve turned a multi-step (but very good) exploit into an exploit that can be written using a single curl command and appears to affect more (older) systems.”
The impact of the identified security problem is extensive and much more severe than its “medium” CVSS rating suggests, and admins must take immediate action to remediate the situation.
The new exploit
Baines says he purchased an old Juniper SRX210 firewall for testing the exploit but found his device did not have the do_fileUpload() functionality required to upload files to the device.
This effectively broke watchTowr’s exploit chain, causing the researcher to see if there was another way to achieve remote code execution.
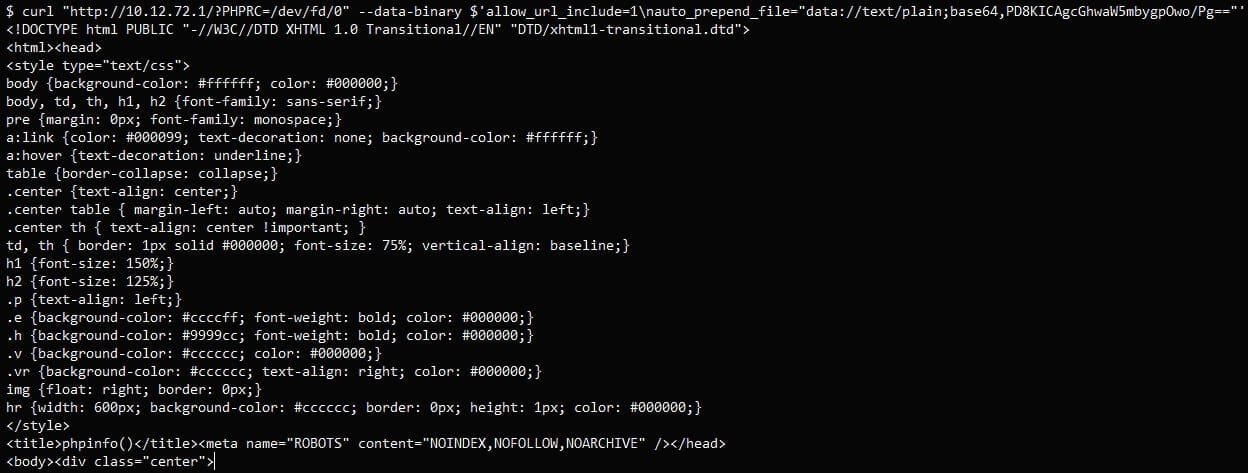
Baines found that you could bypass the need to upload two files on the target servers by manipulating environment variables.
The Juniper firewall’s Appweb web server processes user HTTP requests via stdin when running a CGI script.
Exploiting this, attackers can trick the system into recognizing a pseudo “file,”/dev/fd/0, and by adjusting the PHPRC environment variable and the HTTP request, they can display sensitive data.
Next, VulnCheck harnessed PHP’s ‘auto_prepend_file’ and ‘allow_url_include’ features to run arbitrary PHP code via the data:// protocol without uploading any files.
That said, the severity rating of CVE-2023-36845, which is 5.4, should now be re-evaluated to a much higher critical score due to its ability to achieve remote code execution without any other flaws.
Impact and risk
The CVE-2023-36845 vulnerability impacts the following versions of Junos OS on EX Series and SRX Series:
- All versions before 20.4R3-S8
- 21.1 version 21.1R1 and later versions
- 21.2 versions before 21.2R3-S6
- 21.3 versions before 21.3R3-S5
- 21.4 versions before 21.4R3-S5
- 22.1 versions before 22.1R3-S3
- 22.2 versions before 22.2R3-S2
- 22.3 versions before 22.3R2-S2, 22.3R3
- 22.4 versions before 22.4R2-S1, 22.4R3
The vendor released security updates that addressed the vulnerability on August 17, 2023. However, the low severity rating the flaw received didn’t raise alarms on the impacted users, many of whom might have opted to postpone its application.
VulnCheck’s network scans showed 14,951 Juniper with internet-exposed web interfaces. From a sample size of 3,000 devices, Baines found that 79% were vulnerable to this RCE flaw.
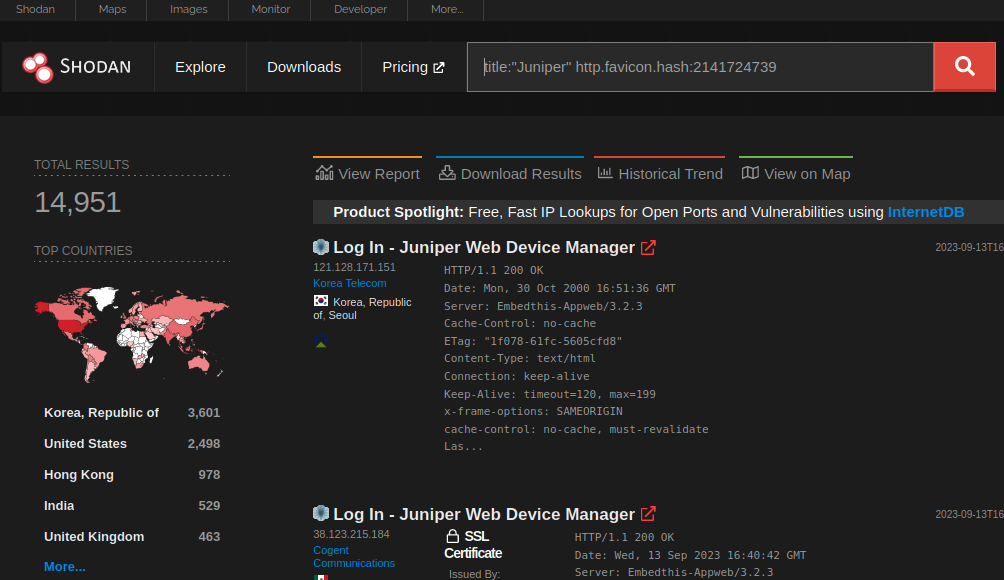
If that percentage is applied to all exposed devices, we may be looking at 11,800 vulnerable devices on the internet.
Finally, the report mentions that Shadowserver and GreyNoise have seen attackers probing Junos OS endpoints, so hackers are already exploring the opportunity to leverage CVE-2023-36845 in attacks.
Therefore, Juniper admins must apply these updates as soon as possible, as they could be used to gain initial access to corporate networks.
Original Post URL: https://www.bleepingcomputer.com/news/security/thousands-of-juniper-devices-vulnerable-to-unauthenticated-rce-flaw/
Category & Tags: Security – Security
Views: 0




















































