
Users searching for TeamViewer remote desktop software on search engines like Google are being redirected to malicious links that drop ZLoader malware onto their systems while simultaneously embracing a stealthier infection chain that allows it to linger on infected devices and evade detection by security solutions.
“The malware is downloaded from a Google advertisement published through Google Adwords,” researchers from SentinelOne said in a report published on Monday. “In this campaign, the attackers use an indirect way to compromise victims instead of using the classic approach of compromising the victims directly, such as by phishing.”
First discovered in 2016, ZLoader (aka Silent Night and ZBot) is a fully-featured banking trojan and a fork of another banking malware called ZeuS, with newer versions implementing a VNC module that grants adversaries remote access to victim systems. The malware is in active development, with criminal actors spawning an array of variants in recent years, no less fuelled by the leak of ZeuS source code in 2011.
The latest wave of attacks is believed to target users of Australian and German financial institutions with the primary goal of intercepting users’ web requests to the banking portals and stealing bank credentials. But the campaign is also noteworthy because of the steps it takes to stay under the radar, including running a series of commands to hide the malicious activity by disabling Windows Defender.
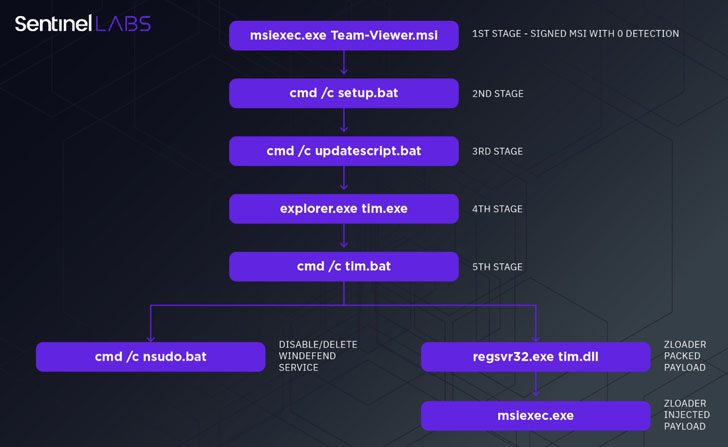
The infection chain commences when a user clicks on an advertisement shown by Google on the search results page and is redirected to the fake TeamViewer site under the attacker’s control, thus tricking the victim into downloading a rogue but signed variant of the software (“Team-Viewer.msi”). The fake installer acts as the first stage dropper to trigger a series of actions that involve downloading next-stage droppers aimed at impairing the defenses of the machine and finally downloading the ZLoader DLL payload (“tim.dll”).https://googleads4.g.doubleclick.net/pcs/view?xai=AKAOjssDk-fiJeudyzsvudLjKUZ5vEZBRRLJncBkeNm1rAeZgz-QwL5o3BO16tAS4vEGmb0lDplXBl6ofmeg0X-muSndyq91pne-PjNcxcXmi0uiRvNSkjJYfJz-zLD-txckUjRHe6ASNxMI_O2Q6PzWrgiQTHE&sai=AMfl-YRmyhdtrRapIU7GpV8YrpL7bifbI6hhnEYYZYKGWe6XNmWCHOTBf1tKbhPxWrjauJbSB0c6MoAKNba7LeEWFvvv_y5M4up3ACY&sig=Cg0ArKJSzBft7zdA2JHCEAE&fbs_aeid=[gw_fbsaeid]&urlfix=1&sdkv=h.3.480.1&vci=[CREATIVE_PLAYBACK]&adurl=volume is gedempt
“At first, it disables all the Windows Defender modules through the PowerShell cmdlet Set-MpPreference,” SentinelOne Senior Threat Intelligence Researcher Antonio Pirozzi said. “It then adds exclusions, such as regsvr32, *.exe, *.dll, with the cmdlet Add-MpPreference to hide all the components of the malware from Windows Defender.”
The cybersecurity firm said it found additional artifacts that mimic popular apps like Discord and Zoom, suggesting that the attackers had multiple campaigns ongoing beyond leveraging TeamViewer.
“The attack chain analyzed in this research shows how the complexity of the attack has grown in order to reach a higher level of stealthiness, using an alternative to the classic approach of compromising victims through phishing emails,” Pirozzi explained. “The technique used to install the first stage dropper has been changed from socially engineering the victim into opening a malicious document to poisoning the user’s web searches with links that deliver a stealthy, signed MSI payload.”
Source: https://thehackernews.com/2021/09/new-stealthier-zloader-variant.html
Views: 16
















