April 12, 2021Ravie Lakshmanan

An Indian security researcher has publicly published a proof-of-concept (PoC) exploit code for a newly discovered flaw impacting Google Chrome and other Chromium-based browsers like Microsoft Edge, Opera, and Brave.
Released by Rajvardhan Agarwal, the working exploit concerns a remote code execution vulnerability in the V8 JavaScript rendering engine that powers the web browsers. It is believed to be the same flaw demonstrated by Dataflow Security’s Bruno Keith and Niklas Baumstark at Pwn2Own 2021 hacking contest last week.
Keith and Baumstark were awarded $100,000 for leveraging the vulnerability to run malicious code inside Chrome and Edge.
According to the screenshot shared by Agarwal, the PoC HTML file, and its associated JavaScript file, can be loaded in a Chromium-based browser to exploit the security flaw and launch the Windows calculator (calc.exe) app. But it’s worth noting that the exploit needs to be chained with another flaw that can allow it to escape Chrome’s sandbox protections.
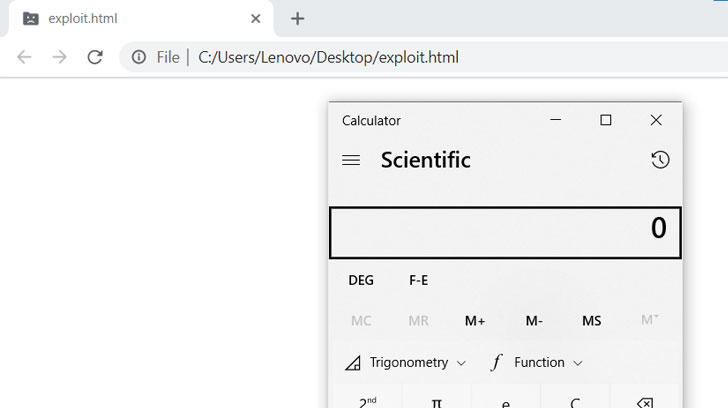
It appears that Agarwal was able to put together the PoC by reverse-engineering the patch that Google’s Chromium team pushed to the open-source component after details of the flaw were shared with the company.
“Getting popped with our own bugs wasn’t on my bingo card for 2021,” Baumstark tweeted. “Not sure it was too smart of Google to add that regression test right away.”
While Google has addressed the issue in the latest version of V8, it’s yet to make its way to the stable channel, thereby leaving the browsers vulnerable to attacks. Google is expected to ship Chrome 90 later today, but it’s not clear if the release will include a patch for the V8 flaw.
We have reached out to Google, and we will update the story if we hear back.
Views: 0




















































