April 13, 2021Ravie Lakshmanan

Microsoft has warned organizations of a “unique” attack campaign that abuses contact forms published on websites to deliver malicious links to businesses via emails containing fake legal threats, in what’s yet another instance of adversaries abusing legitimate infrastructure to mount evasive campaigns that bypass security protections.
“The emails instruct recipients to click a link to review supposed evidence behind their allegations, but are instead led to the download of IcedID, an info-stealing malware,” the company’s threat intelligence team said in a write-up published last Friday.
IceID is a Windows-based banking trojan that’s used for reconnaissance and exfiltration of banking credentials, alongside features that allow it to connect to a remote command-and-control (C2) server to deploy additional payloads such as ransomware and malware capable of performing hands-on-keyboard attacks, stealing credentials, and moving laterally across affected networks.
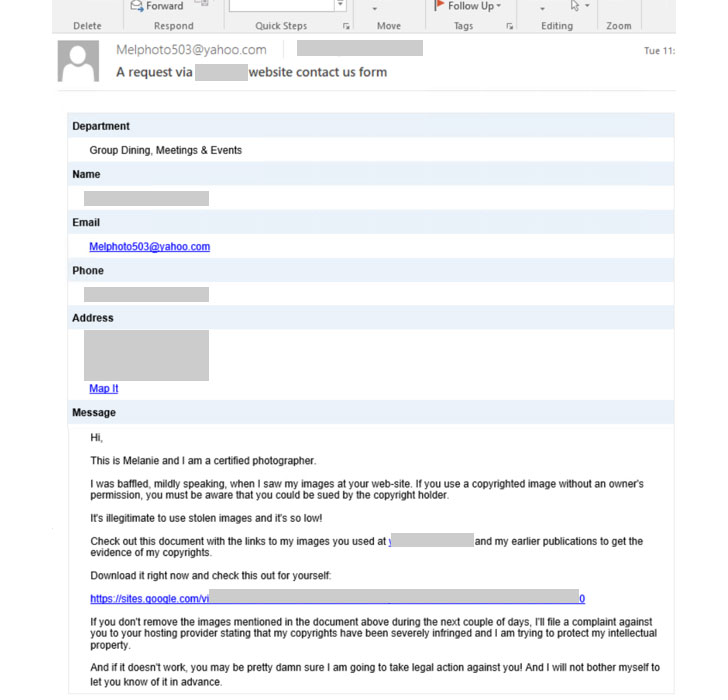
Microsoft researchers said the attackers might have used an automated tool to deliver the emails by abusing the enterprises’ contact forms while circumventing CAPTCHA protections. The emails themselves employ legal threats to intimidate victims, claiming that the recipients “allegedly used their images or illustrations without their consent, and that legal action will be taken against them.”
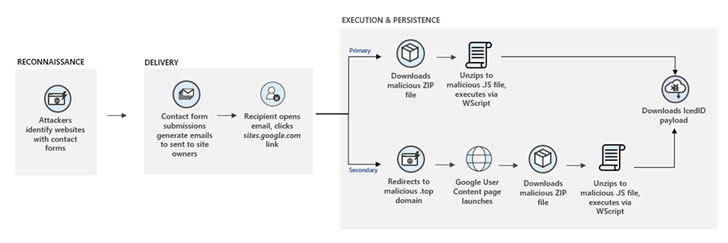
By invoking a sense of urgency, the idea is to lead the victim into revealing sensitive information, click a sketchy link, or open a malicious file. In this infection chain, it’s a link to a sites.google.com page, which requires users to sign in with their Google credentials, following which a ZIP archive file is automatically downloaded.
The ZIP file contains a heavily obfuscated JavaScript file that downloads the IcedID malware. What’s more, the malicious code has the capacity to download secondary implants like Cobalt Strike, potentially putting affected victims at further risk.
The novel intrusion route notwithstanding, the attacks are yet another sign of how threat actors constantly tweak their social engineering tactics to target companies with an intent to distribute malware while evading detection.
“The scenarios […] offer a serious glimpse into how sophisticated attackers’ techniques have grown, while maintaining the goal of delivering dangerous malware payloads such as IcedID,” the researchers said. “Their use of submission forms is notable because the emails don’t have the typical marks of malicious messages and are seemingly legitimate.”
Views: 0




















































