Chinese Cyber Espionage Hackers Continue to Target Pulse Secure VPN Devices

Cybersecurity researchers from FireEye unmasked additional tactics, techniques, and procedures (TTPs) adopted by Chinese threat actors who were recently found abusing Pulse Secure VPN devices to drop malicious web shells and exfiltrate sensitive information from enterprise networks.
FireEye’s Mandiant threat intelligence team, which is tracking the cyber espionage activity under two activity clusters UNC2630 and UNC2717, said the intrusions line up with key Chinese government priorities, adding “many compromised organizations operate in verticals and industries aligned with Beijing’s strategic objectives outlined in China’s recent 14th Five Year Plan.”
On April 20, the cybersecurity firm disclosed 12 different malware families, including STEADYPULSE and LOCKPICK, that have been designed with the express intent to infect Pulse Secure VPN appliances and put to use by at least two cyber espionage groups believed to be affiliated with the Chinese government.
- UNC2630 – SLOWPULSE, RADIALPULSE, THINBLOOD, ATRIUM, PACEMAKER, SLIGHTPULSE, and PULSECHECK
- UNC2717 – HARDPULSE, QUIETPULSE, AND PULSEJUMP
FireEye’s continued investigation into the attacks as part of its incident response efforts has uncovered four more malware families deployed by UNC2630 — BLOODMINE, BLOODBANK, CLEANPULSE, and RAPIDPULSE — for purposes of harvesting credentials and sensitive system data, allowing arbitrary file execution, and removing forensic evidence.
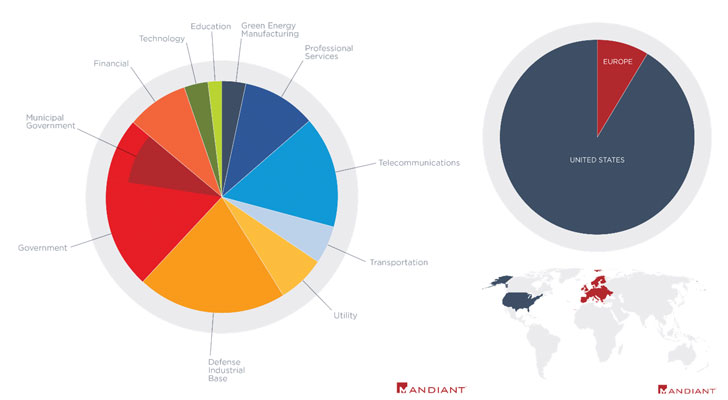
In addition, the threat actors were also observed removing web shells, ATRIUM, and SLIGHTPULSE, from dozens of compromised VPN devices between April 17 and April 20 in what the researchers describe as “unusual,” suggesting “this action displays an interesting concern for operational security and a sensitivity to publicity.”
At the heart of these intrusions lies CVE-2021-22893, a recently patched vulnerability in Pulse Secure VPN devices that the adversaries exploited to gain an initial foothold on the target network, using it to steal credentials, escalate privileges, conduct internal reconnaissance by moving laterally across the network, before maintaining long-term persistent access, and accessing sensitive data.
“Both UNC2630 and UNC2717 display advanced tradecraft and go to impressive lengths to avoid detection. The actors modify file timestamps and regularly edit or delete forensic evidence such as logs, web server core dumps, and files staged for exfiltration,” the researchers said. “They also demonstrate a deep understanding of network appliances and advanced knowledge of a targeted network. This tradecraft can make it difficult for network defenders to establish a complete list of tools used, credentials stolen, the initial intrusion vector, or the intrusion start date.”
Views: 2
















