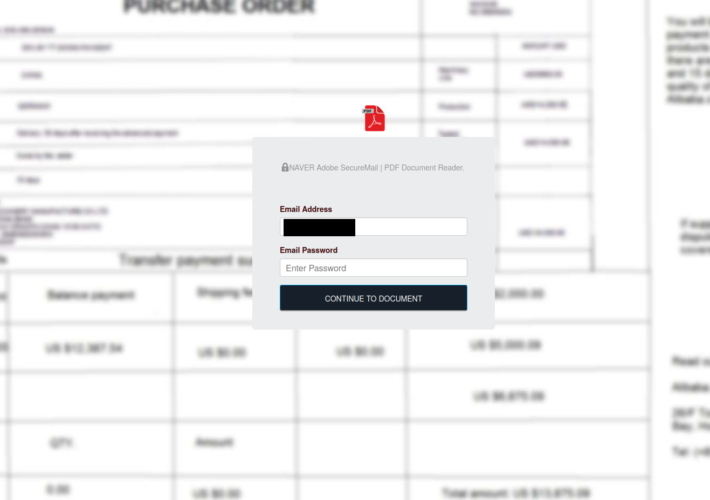
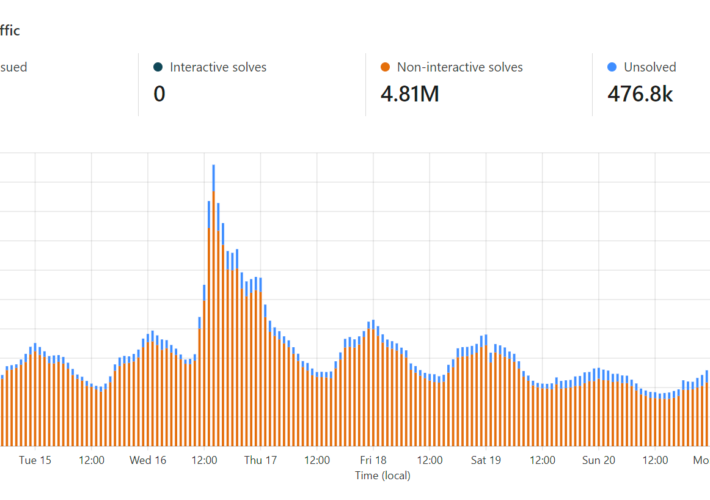
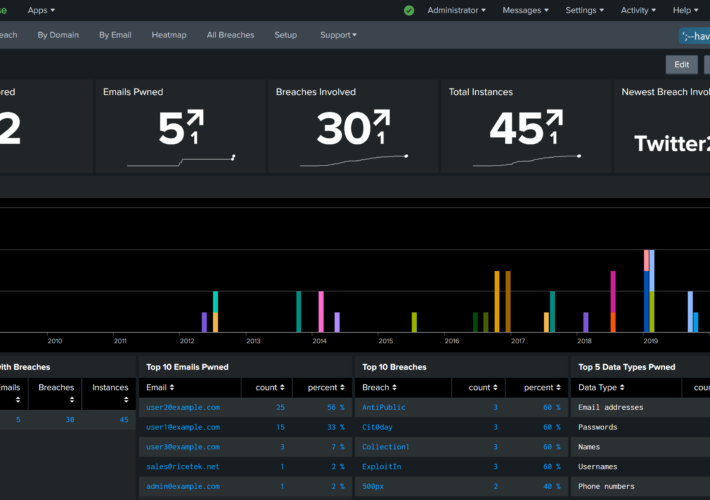
Source: www.troyhunt.com - Author: Troy Hunt Somehow, an hour and a half went by in the...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Troyhunt.com
Source: www.troyhunt.com - Author: Troy Hunt I told ya so. Right from the beginning, it was...
Source: www.troyhunt.com - Author: Troy Hunt Ever hear one of those stories where as it unravels,...
Source: www.troyhunt.com - Author: Troy Hunt I've always thought of it a bit like baseball cards;...
Source: www.troyhunt.com - Author: Troy Hunt I spent longer than I expected talking about Trello this...
Source: www.troyhunt.com - Author: Troy Hunt They're an odd thing, credential lists. Whether they're from a...
Source: www.troyhunt.com - Author: Troy Hunt It feels like not a week goes by without someone...
Source: www.troyhunt.com - Author: Troy Hunt Geez it's nice to be back in Oslo! This city...
Source: www.troyhunt.com - Author: Troy Hunt It's another weekly update from the other side of the...
Source: www.troyhunt.com - Author: Troy Hunt We're in Paris! And feeling proper relaxed after several days...
Source: www.troyhunt.com - Author: Troy Hunt It's that time of the year again, time to head...
Source: www.troyhunt.com - Author: Troy Hunt Imagine you wanted to buy some shit on the internet....
Source: www.troyhunt.com - Author: Troy Hunt Ah, home 😊 It's been more than a month since...
Source: www.troyhunt.com - Author: Troy Hunt Well that's it, Europe is done! I've spent the week...
Source: www.troyhunt.com - Author: Troy Hunt It's another week of travels, this time from our "second...
Source: www.troyhunt.com - Author: Troy Hunt I'm in Spain! Alicante, to be specific, where we've spent...
Source: www.troyhunt.com - Author: Troy Hunt I'm super late pushing out this week's video, I mean...
Source: www.troyhunt.com - Author: Troy Hunt Last week I was contacted by CERT Poland. They'd observed...
Source: www.troyhunt.com - Author: Troy Hunt Today, the US Justice Department announced a multinational operation involving...
Source: www.troyhunt.com - Author: Troy Hunt Somehow in this week's video, I forgot to talk about...
Source: www.troyhunt.com - Author: Troy Hunt There's a "hidden" API on HIBP. Well, it's not "hidden"...
Source: www.troyhunt.com - Author: Troy Hunt This week hasd been manic! Non-stop tickets related to the...
Source: www.troyhunt.com - Author: Troy Hunt I've been teaching my 13-year old son Ari how to...
Source: www.troyhunt.com - Author: Troy Hunt So about those domain searches... 😊 The new subscription model...
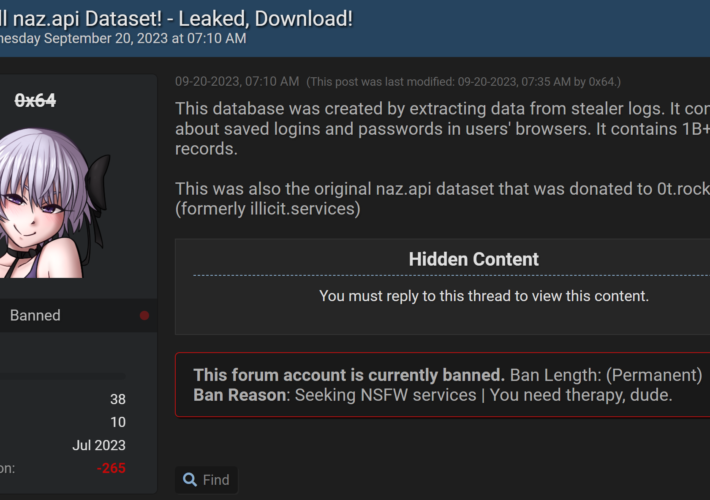
Source: www.troyhunt.com - Author: Troy Hunt This is a big one. A massive one. It's the...
Source: www.troyhunt.com - Author: Troy Hunt Somewhere in the next few hours from publishing this post,...
Source: www.troyhunt.com - Author: Troy Hunt IoT, breaches and largely business as usual so I'll skip...
Source: www.troyhunt.com - Author: Troy Hunt Sad news to wake up to today. Kevin was a...
Source: www.troyhunt.com - Author: Troy Hunt Today was a bit back-to-back having just wrapped up the...
Source: www.troyhunt.com - Author: Troy Hunt Each year since 2011, Microsoft has sent me a lovely...