By Byron V. AcohidoAdopting personas and rubbing elbows with criminal hackers and fraudsters is a tried-and-true...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
The Last Watchdog
Good intelligence in any theater of war is invaluable. Timely, accurate intel is the basis of...
By Byron V. AcohidoEmbedding security into the highly dynamic way new software gets created and put...
By Byron V. AcohidoDomain Name Service. DNS. It’s the phone directory of the Internet.Related: DNS —...
By Byron V. AcohidoOne of the nascent security disciplines already getting a lot of buzz as...
By Harman SinghNo organization is immune to cybersecurity threats. Even the most well-protected companies can be...
At 10 am PDT, next Wednesday, April 19th, I’ll have the privilege of appearing as a...
By Lise LapointeInstilling a culture of cyber security at your organization requires your people to maintain...
By Chandrashekhar BasavannaModern cyber attacks are ingenious — and traditional vulnerability management, or VM, simply is...
By Adam DennisImagine being a young person who wants a career, of whatever type you can...
By Matthew T. CarrOrganizations with strong cybersecurity cultures experience fewer cyberattacks and recover faster than others.Related:...
By Byron V. AcohidoAPIs have been a linchpin as far as accelerating digital transformation — but...
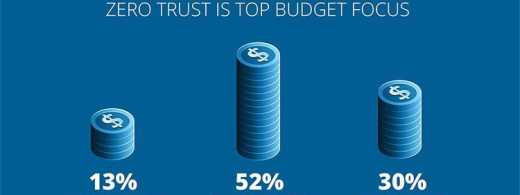
By Zac AmosThe cybersecurity landscape is constantly changing. While it might seem like throwing more money...
By Collin McNultyOne common misconception is that scammers usually possess a strong command of computer science...
By Byron V. AcohidoA new report from the Bipartisan Policy Center (BPC) lays out — in...
By Jess BurnThis year has kicked off with a string of high-profile layoffs — particularly in...
By Rakshith RaoAPIs (Application Programming Interfaces) play a critical role in digital transformation by enabling communication...
The IT world relies on digital authentication credentials, such as API keys, certificates, and tokens, to...
By Sashi JeyaretnamA new generation of security frameworks are gaining traction that are much better aligned...
GUEST ESSAY: Here’s why a big cybersecurity budget won’t necessarily keep your company safe The cybersecurity...
FIRESIDE CHAT: U.S. banking regulators call out APIs as embodying an attack surface full of risk...
GUEST ESSAY: Scammers leverage social media, clever con games to carry out digital exploitation One common...
SHARED INTEL Q&A: Bi-partisan report calls a for a self-sacrificing approach to cybersecurity A new report...
GUEST ESSAY: Could CISOs be on the verge of disproving the ‘security-as-a-cost-center’ fallacy? This year has...
GUEST ESSAY: Five stages to attain API security — and mitigate attack surface exposures APIs (Application...
GUEST ESSAY: Why CISOs absolutely must take authentication secrets much more seriously The IT world relies...
GUEST ESSAY: Testing principles to mitigate real-world risks to ‘SASE’ and ‘Zero Trust’ systems A new...
GUEST ESSAY: The case for complying with ISO 27001 — the gold standard of security frameworks...
FIRESIDE CHAT: New automated tools, practices ascend to help companies wrangle PKI Arguably one of the...
GUEST ESSAY: Advanced tools are ready to help SMBs defend Microsoft 365, Google Workspace Throughout 2022,...