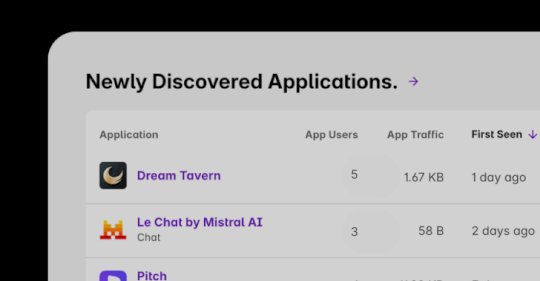
Source: thehackernews.com - Author: . Salesloft has revealed that the data breach linked to its Drift...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
The Hacker News
Source: thehackernews.com - Author: . Cybersecurity researchers have detailed a new sophisticated malware campaign that leverages...
Source: thehackernews.com - Author: . A threat actor possibly of Russian origin has been attributed to...
Source: thehackernews.com - Author: . Cybersecurity never slows down. Every week brings new threats, new vulnerabilities,...
Source: thehackernews.com - Author: . When Attackers Get Hired: Today’s New Identity Crisis What if the...
Source: thehackernews.com - Author: . A threat actor possibly of Russian origin has been attributed to...
Source: thehackernews.com - Author: . A new set of four malicious packages have been discovered in...
Source: thehackernews.com - Author: . Federal Civilian Executive Branch (FCEB) agencies are being advised to update...
Source: thehackernews.com - Author: . The threat actor behind the malware-as-a-service (MaaS) framework and loader called...
Source: thehackernews.com - Author: . A critical security vulnerability impacting SAP S/4HANA, an Enterprise Resource Planning...
Source: thehackernews.com - Author: . Cybersecurity researchers have flagged a new malware campaign that has leveraged...
Source: thehackernews.com - Author: . The Russian state-sponsored hacking group tracked as APT28 has been attributed...
Source: thehackernews.com - Author: . Cybersecurity researchers have lifted the lid on a previously undocumented threat...
Source: thehackernews.com - Author: . Cybersecurity researchers have flagged a new technique that cybercriminals have adopted...
Source: thehackernews.com - Author: . The French data protection authority has fined Google and Chinese e-commerce...
Source: thehackernews.com - Author: . The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added...
Source: thehackernews.com - Author: . Cybersecurity researchers have discovered two new malicious packages on the npm...
Source: thehackernews.com - Author: . Threat actors are attempting to leverage a newly released artificial intelligence...
Source: thehackernews.com - Author: . In January 2025, cybersecurity experts at Wiz Research found that Chinese...
Source: thehackernews.com - Author: . Google has shipped security updates to address 120 security flaws in...
Source: thehackernews.com - Author: . An Iran-nexus group has been linked to a "coordinated" and "multi-wave"...
Source: thehackernews.com - Author: . Cloudflare on Tuesday said it automatically mitigated a record-setting volumetric distributed...
Source: thehackernews.com - Author: . The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added...
Source: thehackernews.com - Author: . Salesloft on Tuesday announced that it's taking Drift temporarily offline "in...
Source: thehackernews.com - Author: . The North Korea-linked threat actor known as the Lazarus Group has...
Source: thehackernews.com - Author: . Cybersecurity researchers have disclosed a stealthy new backdoor called MystRodX that...
Source: thehackernews.com - Author: . The Harsh Truths of AI Adoption MITs State of AI in...
Source: thehackernews.com - Author: . Cybersecurity researchers have flagged a Ukrainian IP network for engaging in...
Source: thehackernews.com - Author: . The threat actor known as Silver Fox has been attributed to...
Source: thehackernews.com - Author: . Cybersecurity researchers have discovered a malicious npm package that comes with...