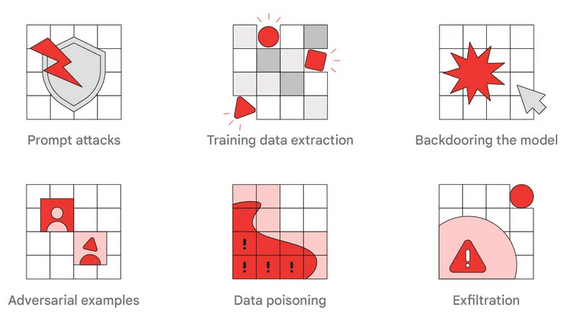
Source: www.securityweek.com - Author: Eduard Kovacs Google has created a red team that focuses on artificial...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire Three vulnerabilities in Apache OpenMeetings potentially expose organizations to remote...
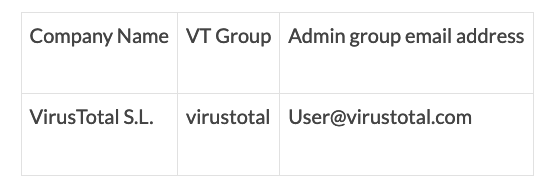
Source: www.securityweek.com - Author: Eduard Kovacs VirusTotal on Friday provided clarifications on the recent data leak...
Source: www.securityweek.com - Author: AFP The White House said Friday that OpenAI and others in the artificial...
Source: www.securityweek.com - Author: Ionut Arghire A North Korean threat actor has been observed targeting employees...
Source: www.securityweek.com - Author: Ionut Arghire Tampa General Hospital this week started informing patients that their...
Source: www.securityweek.com - Author: Eduard Kovacs Firmware and hardware security company Eclypsium has disclosed information on...
Source: www.securityweek.com - Author: Ionut Arghire The cyberattack that directory, identity, and access management company JumpCloud...
Source: www.securityweek.com - Author: Eduard Kovacs Cosmetics giant Estée Lauder has disclosed a data breach just...
Source: www.securityweek.com - Author: Kevin Townsend The process of encouraging secure cyber habits in end users...
Source: www.securityweek.com - Author: Ionut Arghire Multiple distributed denial-of-service (DDoS) botnets are targeting a vulnerability in...
Source: www.securityweek.com - Author: Ionut Arghire A newly discovered peer-to-peer (P2P) worm is targeting Redis servers...
Source: www.securityweek.com - Author: Joshua Goldfarb APIs have certainly changed the way in which businesses operate. APIs...
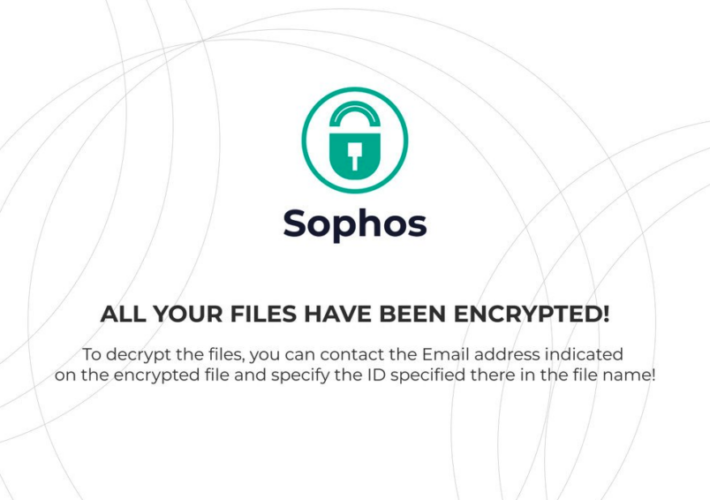
Source: www.securityweek.com - Author: Ionut Arghire A Rust-based file-encrypting ransomware was found this week to be...
Source: www.securityweek.com - Author: Eduard Kovacs Adobe has released a second round of patches for some...
Source: www.securityweek.com - Author: SecurityWeek News Kevin Mitnick, a hacker who famously served time in prison...
Source: www.securityweek.com - Author: Ryan Naraine Facing intense pressure to free up access to cloud security...
Source: www.securityweek.com - Author: Ionut Arghire Norwegian recycling giant Tomra has taken some of its systems...
Source: www.securityweek.com - Author: Ionut Arghire Attackers are apparently trying to exploit two path traversal vulnerabilities...
Source: www.securityweek.com - Author: Mike Lennon SecurityWeek’s 2023 Cloud & Data Security Summit kicks off today!...
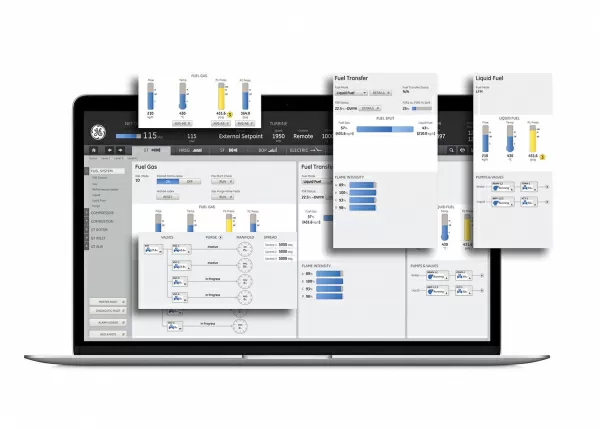
Source: www.securityweek.com - Author: Eduard Kovacs Over a dozen vulnerabilities patched recently by GE in its...
Source: www.securityweek.com - Author: Kevin Townsend Security awareness training isn’t working to the level it needs...
Source: www.securityweek.com - Author: Ionut Arghire Oracle on Tuesday announced the release of 508 new security...
Source: www.securityweek.com - Author: Eduard Kovacs Citrix on Tuesday announced patches for three vulnerabilities, including an...
Source: www.securityweek.com - Author: Ionut Arghire Google on Tuesday announced the release of Chrome 115 to...
Source: www.securityweek.com - Author: Ryan Naraine The U.S. government’s clampdown on commercial spyware and mercenary hacking...
Source: www.securityweek.com - Author: Ionut Arghire The National Security Agency (NSA) and the Cybersecurity and Infrastructure...
Source: www.securityweek.com - Author: Eduard Kovacs A Nigerian national who had been living in the United...
Source: www.securityweek.com - Author: Ionut Arghire A threat actor infected their own computer with an information...
Source: www.securityweek.com - Author: Ionut Arghire Threat actors have started hacking WordPress websites by exploiting a...