Source: www.securityweek.com - Author: Eduard Kovacs Siemens released a dozen advisories covering more than 30 vulnerabilities...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Kevin Townsend The Royal United Services Institute (RUSI) is an independent UK...
Source: www.securityweek.com - Author: Ryan Naraine LAS VEGAS — Once the undisputed hub for the most...
Source: www.securityweek.com - Author: Eduard Kovacs Microsoft on Monday published a summary of its artificial intelligence...
Source: www.securityweek.com - Author: SecurityWeek News Resilience Cyber Insurance Solutions has raised $100 million through a Series...
Source: www.securityweek.com - Author: Eduard Kovacs A Russian defense industrial base organization specializing in missiles and...
Source: www.securityweek.com - Author: Eduard Kovacs Organizations have been warned about a new potentially serious vulnerability...
Source: www.securityweek.com - Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) has unveiled...
Source: www.securityweek.com - Author: Eduard Kovacs The Colorado Department of Higher Education (CDHE) has been targeted...
Source: www.securityweek.com - Author: Associated Press A cyberattack has disrupted hospital computer systems in several states,...
Source: www.securityweek.com - Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a...
Source: www.securityweek.com - Author: Ionut Arghire Threat actors have been observed abusing an open source tool...
Source: www.securityweek.com - Author: Eduard Kovacs A critical Microsoft Power Platform vulnerability exposed organizations’ authentication data...
Source: www.securityweek.com - Author: Ionut Arghire Multiple vulnerabilities in the popular airline and hotel rewards platform...
Source: www.securityweek.com - Author: AFP A married couple from New York dubbed “Bitcoin Bonnie and Crypto...
Source: www.securityweek.com - Author: Eduard Kovacs Exploitation of the recently disclosed Ivanti Endpoint Manager Mobile (EPMM)...
Source: www.securityweek.com - Author: Ionut Arghire Government agencies in Australia, Canada, New Zealand, the UK, and...
Source: www.securityweek.com - Author: Ryan Naraine The US government’s cybersecurity agency CISA is calling attention to...
Source: www.securityweek.com - Author: Ionut Arghire Jericho Security today announced that it has raised $3 million...
Source: www.securityweek.com - Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) disclosed 670...
Source: www.securityweek.com - Author: Ionut Arghire Dozens of vulnerabilities impacting the Milesight UR32L industrial router could...
Source: www.securityweek.com - Author: Kevin Townsend Cloud security specialist Qualys has provided its view of the...
Decommissioned Medical Infusion Pumps Expose Wi-Fi Configuration Data – Source: www.securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire Most medical infusion pumps sold via secondary market sources still...
Source: www.securityweek.com - Author: Eduard Kovacs Forty-two cybersecurity-related merger and acquisition (M&A) deals were announced in...
Source: www.securityweek.com - Author: Ionut Arghire Google on Wednesday announced a Chrome 115 update that patches...
Source: www.securityweek.com - Author: Eduard Kovacs Threat actors have exploited a Salesforce zero-day vulnerability and abused...
Source: www.securityweek.com - Author: Ryan Naraine Just ten months after securing an abnormally large seed-stage funding...
Source: www.securityweek.com - Author: Ryan Naraine Software giant Microsoft on Wednesday sounded an alarm after catching...
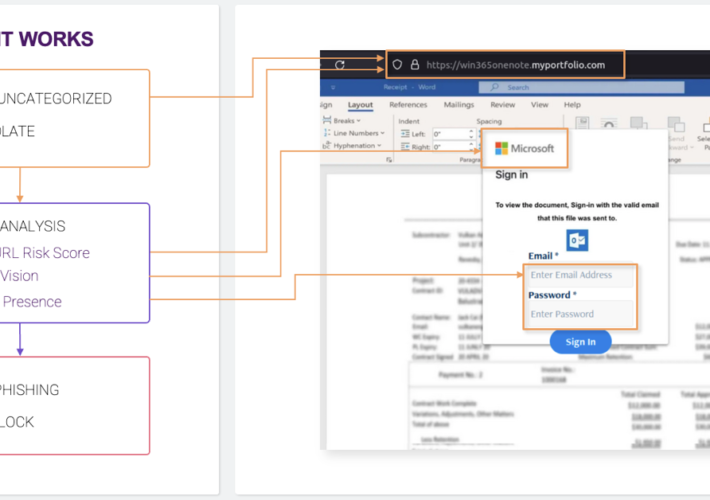
Source: www.securityweek.com - Author: Kevin Townsend Menlo Security has introduced two anti-phishing solutions that tackle the...
Source: www.securityweek.com - Author: Ionut Arghire A new Hidden Virtual Network Computing (hVNC) malware targeting macOS...