Source: www.securityweek.com - Author: Matt Honea Email has been around a long time. My early days...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire The US government announced on Friday that the DHS’s Cyber...
Source: www.securityweek.com - Author: Eduard Kovacs Vulnerabilities in power management products made by CyberPower and Dataprobe...
Source: www.securityweek.com - Author: Ionut Arghire US authorities have announced the seizure of LolekHosted.net, the domain...
Source: www.securityweek.com - Author: Ionut Arghire American car maker Ford says that a vulnerability in the...
Iagona ScrutisWeb Vulnerabilities Could Expose ATMs to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com - Author: Eduard Kovacs Several vulnerabilities discovered in the ScrutisWeb ATM fleet monitoring software...
Source: www.securityweek.com - Author: Associated Press White House officials concerned by AI chatbots’ potential for societal...
Source: www.securityweek.com - Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a...
Source: www.securityweek.com - Author: Eduard Kovacs Over a dozen vulnerabilities discovered by Microsoft researchers in Codesys...
Source: www.securityweek.com - Author: Associated Press Northern Ireland’s top police officer apologized Thursday for what he...
Source: www.securityweek.com - Author: Eduard Kovacs Hundreds of companies and organizations showcased their cybersecurity products and...
Source: www.securityweek.com - Author: Associated Press Indian lawmakers Wednesday approved a data protection legislation that “seeks...
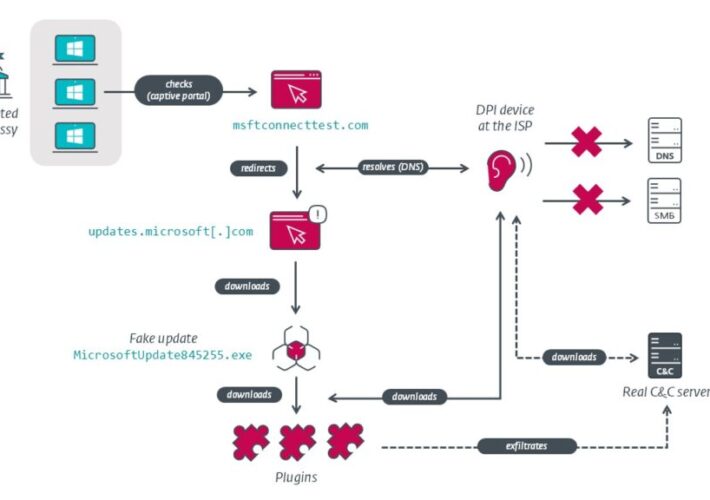
Source: www.securityweek.com - Author: Eduard Kovacs Foreign embassies in Belarus have been targeted by a cyberespionage...
Source: www.securityweek.com - Author: Mike Lennon Network security giant Check Point Software (NASDAQ: CHKP) on Thursday...
Source: www.securityweek.com - Author: Joshua Goldfarb Recently, on my morning jog, I saw a garbage truck...
Source: www.securityweek.com - Author: Eduard Kovacs Symmetry Systems has raised $17.7 million in an insider funding...
Source: www.securityweek.com - Author: Eduard Kovacs Norway-based startup Pistachio on Thursday announced raising €3.25 million (roughly...
Source: www.securityweek.com - Author: Eduard Kovacs The US Cybersecurity and Infrastructure Security Agency (CISA) has added...
Source: www.securityweek.com - Author: AFP The White House on Wednesday launched a competition offering millions of...
Source: www.securityweek.com - Author: Eduard Kovacs Critical vulnerabilities discovered by IoT and industrial cybersecurity firm Claroty...
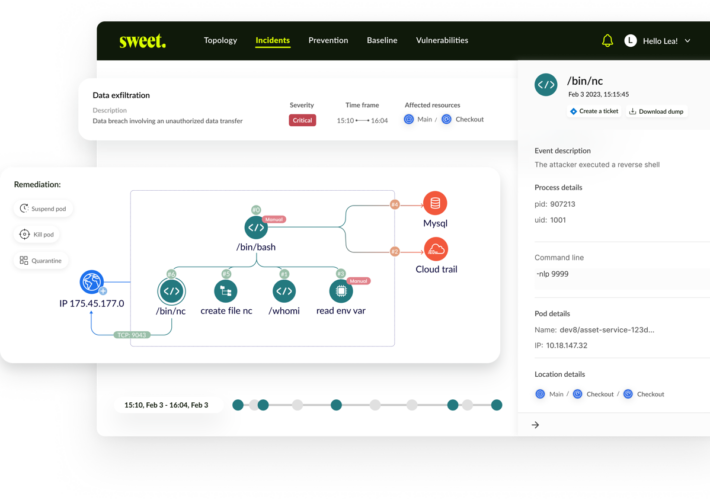
Source: www.securityweek.com - Author: Kevin Townsend Israeli startup Sweet Security has emerged from stealth, launched a...
Source: www.securityweek.com - Author: Eduard Kovacs For the fourth consecutive year, Microsoft has announced paying out...
Source: www.securityweek.com - Author: Eduard Kovacs Intel on Tuesday released a total of 46 new security...
Source: www.securityweek.com - Author: Eduard Kovacs German software giant SAP has fixed more than a dozen...
Source: www.securityweek.com - Author: Eduard Kovacs Researchers on Tuesday disclosed the details of a new CPU...
Source: www.securityweek.com - Author: Eduard Kovacs Just over 40 vulnerabilities have been patched by Google in...
Source: www.securityweek.com - Author: Eduard Kovacs The details of a new side-channel attack targeting Intel processors...
Source: www.securityweek.com - Author: Mike Lennon Rapid7 (NASDAQ: RPD) is the latest cybersecurity vendor to announce...
Source: www.securityweek.com - Author: Matt Wilson It is well known that when it comes to cybersecurity,...
Source: www.securityweek.com - Author: Eduard Kovacs CrowdStrike on Tuesday released its 2023 Threat Hunting Report, warning...