Source: www.securityweek.com - Author: Ionut Arghire Peer-to-peer digital asset transactional network Mixin Network has suspended deposits...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire A stealthy advanced persistent threat (APT) actor known as Gelsemium...
Source: www.securityweek.com - Author: Ionut Arghire A Nigerian national residing in South Africa last week pleaded...
Source: www.securityweek.com - Author: Eduard Kovacs The National Student Clearinghouse, an educational nonprofit that provides reporting,...
Source: www.securityweek.com - Author: Ionut Arghire The City of Dallas has announced that an $8.5 million...
Source: www.securityweek.com - Author: Ionut Arghire A critical vulnerability in the TeamCity CI/CD server could be...
Source: www.securityweek.com - Author: Eduard Kovacs The Predator spyware has been delivered to iPhones and Android...
Source: www.securityweek.com - Author: Associated Press A leading Egyptian opposition politician was targeted with spyware after...
Source: www.securityweek.com - Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a...
Source: www.securityweek.com - Author: Eduard Kovacs Chinese state-sponsored threat groups have targeted telecommunications, financial and government...
Source: www.securityweek.com - Author: Ionut Arghire Air Canada, the largest airline in the country, this week...
Source: www.securityweek.com - Author: Ionut Arghire The Internet Systems Consortium (ISC) has released security updates to...
Source: www.securityweek.com - Author: Ionut Arghire The Known Exploited Vulnerabilities (KEV) Catalog maintained by the US...
Source: www.securityweek.com - Author: Eduard Kovacs A survey conducted by the SANS Institute shows that the...
Source: www.securityweek.com - Author: Eduard Kovacs Apple announced on Thursday that its latest operating system updates...
Source: www.securityweek.com - Author: Ryan Naraine A new and mysterious APT group has been spotted targeting...
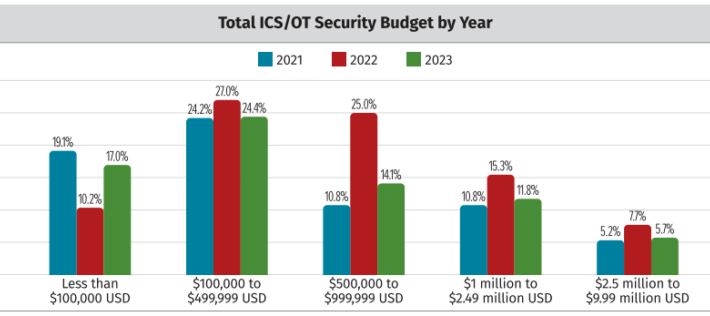
Source: www.securityweek.com - Author: John Maddison Every network today is now an OT network. Or it...
Navigating the Digital Frontier in Cybersecurity Awareness Month 2023 – Source: www.securityweek.com
Source: www.securityweek.com - Author: Torsten George This October will mark the 20th anniversary of Cybersecurity Awareness...
TransUnion Denies Breach After Hacker Publishes Allegedly Stolen Data – Source: www.securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire Credit reporting firm TransUnion this week denied being breached, after...
Source: www.securityweek.com - Author: Ionut Arghire Application security posture management firm Legit Security on Wednesday announced...
Source: www.securityweek.com - Author: Eduard Kovacs Cisco on Thursday announced that it has entered into a...
Source: www.securityweek.com - Author: Ionut Arghire Atlassian this week announced patches for four high-severity vulnerabilities impacting...
Source: www.securityweek.com - Author: Eduard Kovacs Research-focused security services provider IOActive has conducted an analysis of...
Source: www.securityweek.com - Author: Associated Press British lawmakers have approved an ambitious but controversial new internet...
Source: www.securityweek.com - Author: Ionut Arghire The FBI and the cybersecurity agency CISA on Wednesday published...
Source: www.securityweek.com - Author: Eduard Kovacs Chip giant Intel announced on the second day of its...
Source: www.securityweek.com - Author: Ionut Arghire Authorities in Finland and Europol on Tuesday announced the seizure...
Source: www.securityweek.com - Author: Joshua Goldfarb Have you ever been in a meeting where someone keeps...
Discern Security Emerges From Stealth Mode With $3 Million in Funding – Source: www.securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire AI-driven policy management cybersecurity startup Discern Security on Tuesday announced...
Source: www.securityweek.com - Author: Ionut Arghire The US Department of Homeland Security (DHS) on Tuesday published...