Source: www.securityweek.com - Author: Ionut Arghire A zero-day vulnerability in Samsung’s mobile processors has been leveraged...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Eduard Kovacs Germany’s CERT@VDE has alerted organizations to several critical and high-severity...
Source: www.securityweek.com - Author: Ionut Arghire The Alphv/BlackCat ransomware gang might have pulled an exit scam...
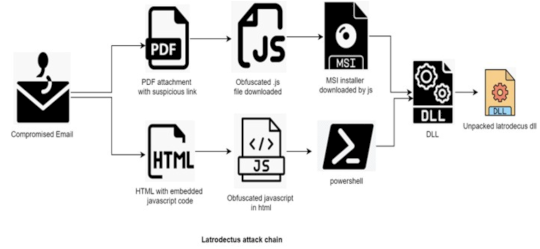
Source: www.securityweek.com - Author: Kevin Townsend The Latrodectus malware has been increasingly used by cybercriminals, with...
Source: www.securityweek.com - Author: Ryan Naraine Enterprise anti-malware vendor Sophos on Monday announced plans to acquire...
Source: www.securityweek.com - Author: Eduard Kovacs ESET has launched an investigation after the systems of its...
Source: www.securityweek.com - Author: Ionut Arghire Researchers can earn bug bounty rewards of up to $101,010...
Source: www.securityweek.com - Author: Eduard Kovacs Cisco on Friday confirmed that some of its files have...
Source: www.securityweek.com - Author: Ionut Arghire Atlassian has announced security updates that resolve six high-severity vulnerabilities...
Source: www.securityweek.com - Author: Ionut Arghire Japanese electric motor manufacturer Nidec has confirmed that various types...
Source: www.securityweek.com - Author: Kevin Townsend AI hacking (both of and with AI), hardware hacking, and...
Source: www.securityweek.com - Author: Ionut Arghire A threat actor was caught attempting to exploit a recent...
Source: www.securityweek.com - Author: SecurityWeek News SecurityWeek’s 2024 ICS Cybersecurity Conference kicks off on Tuesday, October...
Source: www.securityweek.com - Author: Eduard Kovacs Data security company Cyera announced on Thursday that it has...
Source: www.securityweek.com - Author: Ionut Arghire Microsoft on Thursday warned of a recently patched macOS vulnerability...
Source: www.securityweek.com - Author: SecurityWeek News SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy...
Source: www.securityweek.com - Author: Ionut Arghire A North Korean threat actor has exploited a recent Internet...
Source: www.securityweek.com - Author: Jennifer Leggio Few things bring me more joy than this ongoing Rising...
Source: www.securityweek.com - Author: Ionut Arghire Hundreds of companies in the US, UK, and Australia have...
Source: www.securityweek.com - Author: Eduard Kovacs Organizations have been getting faster at detecting incidents in industrial...
Source: www.securityweek.com - Author: Associated Press An Alabama man was arrested Thursday for his alleged role...
Source: www.securityweek.com - Author: Ionut Arghire California network of health centers Omni Family Health is notifying...
Source: www.securityweek.com - Author: Stu Sjouwerman Email phishing is by far one of the most prevalent...
Source: www.securityweek.com - Author: Ionut Arghire The US cybersecurity agency CISA and the FBI have released...
Source: www.securityweek.com - Author: Ionut Arghire F5 on Wednesday published its October 2024 quarterly security notification,...
Source: www.securityweek.com - Author: Ionut Arghire Cisco on Wednesday announced patches for eight vulnerabilities in the...
Source: www.securityweek.com - Author: Ionut Arghire Iranian state-sponsored threat actors have been using brute force and...
Source: www.securityweek.com - Author: Eduard Kovacs Brazil’s Federal Police on Wednesday announced the arrest of a...
Source: www.securityweek.com - Author: Eduard Kovacs The US Justice Department on Wednesday announced charges against two...
Source: www.securityweek.com - Author: Ryan Naraine Artificial intelligence tech giant Nvidia has flagged a major security...