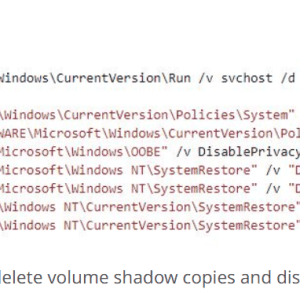
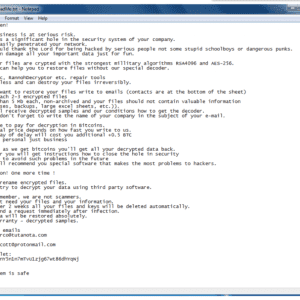
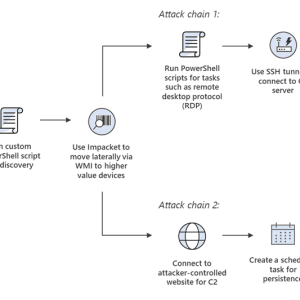
Source: securityaffairs.com - Author: Pierluigi Paganini. Threat actors are hacking poorly secured and Interned-exposed Microsoft SQL...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
SecurityAffairs.com
Source: securityaffairs.com - Author: Pierluigi Paganini. Russian national Denis Mihaqlovic Dubnikov has been sentenced to time...
Source: securityaffairs.com - Author: Pierluigi Paganini. Google rolled out emergency security patches to address another actively...
Source: securityaffairs.com - Author: Pierluigi Paganini. UK and US agencies are warning of Russia-linked APT28 group exploiting vulnerabilities...
Source: securityaffairs.com - Author: Pierluigi Paganini. An Iran-linked APT group tracked as Mint Sandstorm is behind a string...
Source: securityaffairs.com - Author: Pierluigi Paganini. Citizen Lab reported that Israeli surveillance firm NSO Group used...
Source: securityaffairs.com - Author: Pierluigi Paganini. Security experts from ESET, have temporarily disrupted the operations of...
Source: securityaffairs.com - Author: Pierluigi Paganini. US Cybersecurity and Infrastructure Security Agency (CISA) added Chrome and...
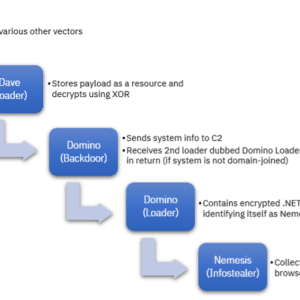
Source: securityaffairs.com - Author: Pierluigi Paganini. A new malware, dubbed Domino, developed by the FIN7 cybercrime...
Source: securityaffairs.com - Author: Pierluigi Paganini. The Israeli surveillance firm QuaDream is allegedly shutting down its operations...
Source: securityaffairs.com - Author: Pierluigi Paganini. Kaspersky researchers warn of a new QBot campaign leveraging hijacked...
Source: securityaffairs.com - Author: Pierluigi Paganini. China-linked APT41 group used the open-source red teaming tool GC2...
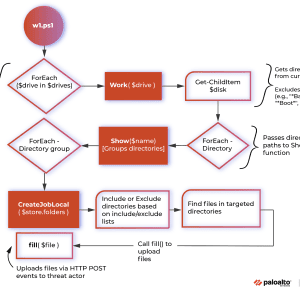
Source: securityaffairs.com - Author: Pierluigi Paganini. Vice Society ransomware operators have been spotted using a PowerShell...
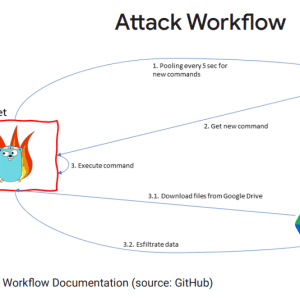
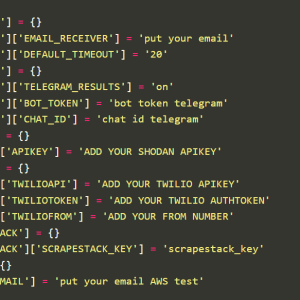
Source: securityaffairs.com - Author: Pierluigi Paganini. Legion is an emerging Python-based credential harvester and hacking tool...
Source: securityaffairs.com - Author: Pierluigi Paganini. Researchers warn that the LockBit ransomware gang has developed encryptors...
NCR was the victim of the BlackCat/ALPHV ransomware gang, the attack caused an outage on the...
Privacy Overview This website uses cookies to improve your experience while you navigate through the website....
Microsoft warns of a new Remcos RAT campaign targeting US accounting and tax return preparation firms...
A new Android malware named Goldoson was distributed through 60 legitimate apps on the official Google...
Siemens Metaverse, a virtual space built to mirror real machines, factories, and other highly complex systems,...
US Cybersecurity and Infrastructure Security Agency (CISA) added Android and Novi Survey flaws to its Known...
The Brazilian retail arm of car manufacturing giant Volvo leaked sensitive files, putting its clientele in...
The Cornwall Community Hospital in Ontario, Canada, is under a cyber attack that is causing delays...
Google released an emergency security update to address a zero-day vulnerability in Chrome which is actively exploited in the...
Open-source media player software provider Kodi discloses a data breach after threat actors stole its MyBB...
Cybersecurity firm Trellix analyzed the activity of an emerging cybercriminal group called ‘Read The Manual’ RTM...
Chinese video surveillance giant Hikvision addressed a critical vulnerability in its Hybrid SAN and cluster storage...
Poland intelligence linked the Russian APT29 group to a series of attacks targeting NATO and European...
Security experts warn that a Kyocera Android printing app is vulnerable to improper intent handling and can...
Fortinet addressed a critical vulnerability that can lead to remote, unauthenticated access to Redis and MongoDB...