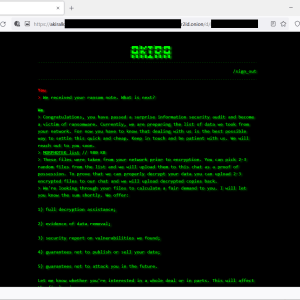
Source: securityaffairs.com - Author: Pierluigi Paganini The FBI warned that patches for a critical Barracuda ESG...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
SecurityAffairs.com
Researchers released PoC exploit for Ivanti Sentry flaw CVE-2023-38035 – Source: securityaffairs.com
Source: securityaffairs.com - Author: Pierluigi Paganini Proof-of-concept exploit code for critical Ivanti Sentry authentication bypass flaw...
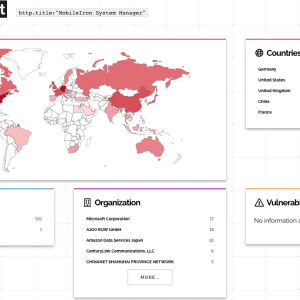
Source: securityaffairs.com - Author: Pierluigi Paganini The North Korea-linked Lazarus group exploits a critical flaw in...
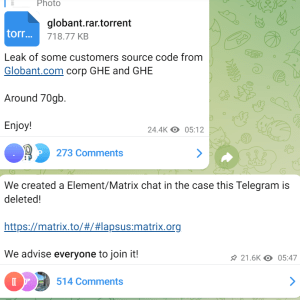
Source: securityaffairs.com - Author: Pierluigi Paganini An 18-year-old member of the Lapsus$ gang has been convicted...
Source: securityaffairs.com - Author: Pierluigi Paganini Researchers warn that more than 3,000 unpatched Openfire servers are...
DoJ charged Tornado Cash founders with laundering more than $1 billion – Source: securityaffairs.com
Source: securityaffairs.com - Author: Pierluigi Paganini The U.S. DoJ charged two men with operating the Tornado...
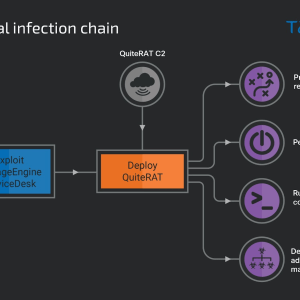
Source: securityaffairs.com - Author: Pierluigi Paganini The U.S. FBI warned that North Korea-linked threat actors may...
Source: securityaffairs.com - Author: Pierluigi Paganini A previously unknown APT group, tracked as Carderbee, was behind...
Source: securityaffairs.com - Author: Pierluigi Paganini Four vulnerabilities in the TP-Link Tapo L530E smart bulb and...
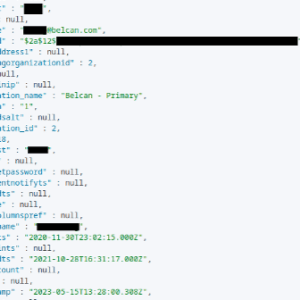
Source: securityaffairs.com - Author: Pierluigi Paganini US Government and defense contractor Belcan left its super admin...
Source: securityaffairs.com - Author: Pierluigi Paganini The Akira ransomware gang targets Cisco VPN products to gain...
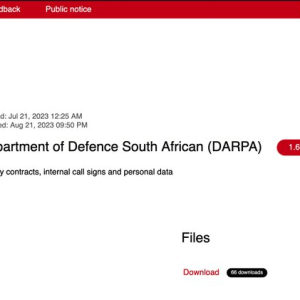
Source: securityaffairs.com - Author: Pierluigi Paganini Snatch gang claims the hack of the Department of Defence...
Source: securityaffairs.com - Author: Pierluigi Paganini US CISA added critical vulnerability CVE-2023-26359 in Adobe ColdFusion to its Known...
Source: securityaffairs.com - Author: Pierluigi Paganini The Australian software provider Energy One announced it was hit...
Source: securityaffairs.com - Author: Pierluigi Paganini Ivanti warned customers of a new critical Sentry API authentication...
Source: securityaffairs.com - Author: Pierluigi Paganini The BlackCat/ALPHV ransomware group claims to have hacked the Japanese...
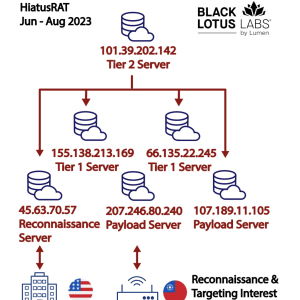
Source: securityaffairs.com - Author: Pierluigi Paganini HiatusRAT malware operators resurfaced with a new wave of attacks...
Source: securityaffairs.com - Author: Pierluigi Paganini White hat hackers at the recent hacking conference Def Con...
Source: securityaffairs.com - Author: Pierluigi Paganini Israel and US government agencies announced the BIRD Cyber Program,...
Source: securityaffairs.com - Author: Pierluigi Paganini North Korea-linked APT Kimsuky launched a spear-phishing campaign targeting US...
Source: securityaffairs.com - Author: Pierluigi Paganini Juniper Networks addressed multiple flaws in the J-Web component of...
Source: securityaffairs.com - Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience...
Source: securityaffairs.com - Author: Pierluigi Paganini Understanding cybersecurity aspects addressed by Cloud Access Security Broker (CASB)...
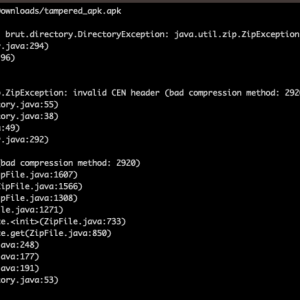
Source: securityaffairs.com - Author: Pierluigi Paganini Threat actors are using Android Package (APK) files with unsupported...
Source: securityaffairs.com - Author: Pierluigi Paganini A flaw impacting the file archiver utility for Windows WinRAR...
Source: securityaffairs.com - Author: Pierluigi Paganini #OpFukushima: The famous collective Anonymous has launched cyberattacks against Japan...
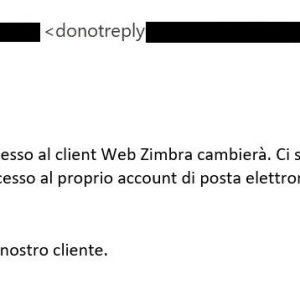
Source: securityaffairs.com - Author: Pierluigi Paganini A massive social engineering campaign is targeting users of the...
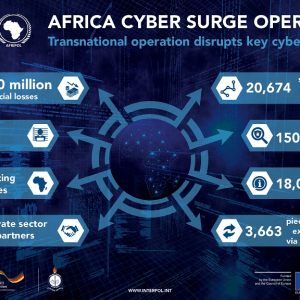
Source: securityaffairs.com - Author: Pierluigi Paganini An international law enforcement operation across 25 African countries has...
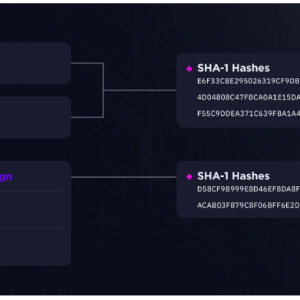
Source: securityaffairs.com - Author: Pierluigi Paganini Experts warn of an ongoing campaign attributed to China-linked Bronze...
Source: securityaffairs.com - Author: Pierluigi Paganini Russia-linked APT29 used the Zulip Chat App in attacks aimed...