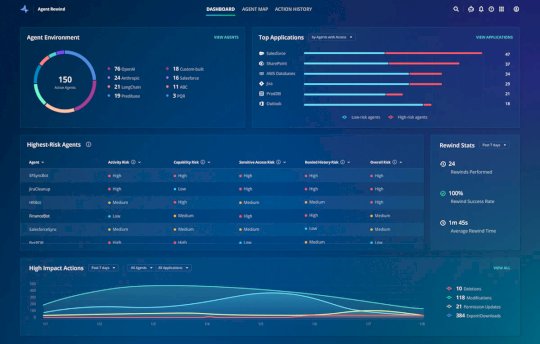
Source: www.techrepublic.com - Author: TechRepublic Staff Image: TechRepublic Anthropic has been rolling out new capabilities for...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security TechRepublic
Source: www.techrepublic.com - Author: Aminu Abdullahi We may earn from vendors via affiliate links or sponsorships....
Source: www.techrepublic.com - Author: Megan Crouse Topic — Artificial Intelligence Published August 13, 2025 Trackers were...
Source: www.techrepublic.com - Author: Megan Crouse Microsoft patched CVE-2025-50165, an “extremely high-risk” memory corruption flaw in...
Source: www.techrepublic.com - Author: Liz Ticong Image: thichaa/Envato Hackers have infiltrated the computer of a North...
Source: www.techrepublic.com - Author: Aminu Abdullahi Topic — Artificial Intelligence Published August 13, 2025 Rubrik’s new...
Source: www.techrepublic.com - Author: Aminu Abdullahi Older WinRAR versions let malicious archives override the user-specified path...
Source: www.techrepublic.com - Author: Megan Crouse Published August 12, 2025 SonicWall identified under 40 security incidents...
Source: www.techrepublic.com - Author: TechRepublic Academy Published August 12, 2025 We may earn from vendors via...
Source: www.techrepublic.com - Author: J.R. Johnivan Published August 11, 2025 At Black Hat USA 2025, Dirk-jan...
Source: www.techrepublic.com - Author: J.R. Johnivan Published August 11, 2025 Hackers posed as Salesforce IT staff,...
Source: www.techrepublic.com - Author: Megan Crouse OpenAI CEO Sam Altman speaks on the Aug. 7 livestream...
Microsoft Rolls Out Scalable Cybersecurity Playbook with SFI Patterns – Source: www.techrepublic.com
Source: www.techrepublic.com - Author: Esther Shein Microsoft’s Secure Future Initiative (SFI) offers structured cybersecurity guidance to...
Source: www.techrepublic.com - Author: TechRepublic Academy Published August 11, 2025 We may earn from vendors via...
Source: www.techrepublic.com - Author: TechRepublic Academy Published August 11, 2025 We may earn from vendors via...
Source: www.techrepublic.com - Author: Megan Crouse Published August 11, 2025 SonicWall and other threat researchers are...
Source: www.techrepublic.com - Author: Liz Ticong Topic — Artificial Intelligence Published August 11, 2025 We may...
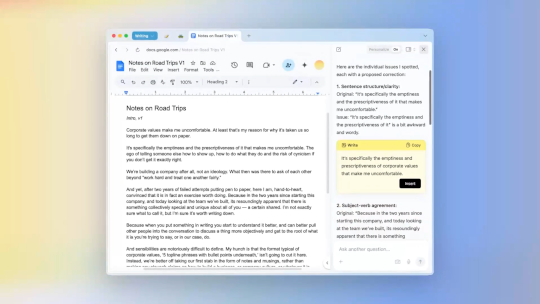
Source: www.techrepublic.com - Author: Fiona Jackson Screenshot of the Dia browser. Dia, the AI-powered browser from...
Source: www.techrepublic.com - Author: Matt Gonzales Nicole Perlroth, former New York Times reporter and founding partner...
Source: www.techrepublic.com - Author: Matt Gonzales Microsoft employees at Black Hat 2025 in Las Vegas: (l...
Source: www.techrepublic.com - Author: Aminu Abdullahi Published August 7, 2025 Scam groups use fake investments, crypto...
Source: www.techrepublic.com - Author: Matt Gonzales Image: kjekol/Envato We asked a simple question to cybersecurity pros...
Source: www.techrepublic.com - Author: Aminu Abdullahi Published August 6, 2025 Project Ire is Microsoft's autonomous AI...
Source: www.techrepublic.com - Author: Matt Gonzales Cybersecurity researcher Mikko Hypponen delivering his keynote address during the...
Source: www.techrepublic.com - Author: Megan Crouse The statement comes as both US and Chinese authorities probe...
Source: www.techrepublic.com - Author: Aminu Abdullahi Topic — Artificial Intelligence Published August 6, 2025 Claude Opus...
Source: www.techrepublic.com - Author: TechRepublic Academy Published August 6, 2025 We may earn from vendors via...
Source: www.techrepublic.com - Author: TechRepublic Staff Image: Murrstock/Adobe Stock Google’s AI agent Big Sleep identified the...
Source: www.techrepublic.com - Author: Aminu Abdullahi Image: VisualWonders/Adobe Stock A new report from Palo Alto Networks’...
ISC2 AI Certificate Offers Upskilling for Cybersecurity Professionals – Source: www.techrepublic.com
Source: www.techrepublic.com - Author: Megan Crouse Topic — Artificial Intelligence Published August 5, 2025 The total...