The document focuses on assisting organizations in integrating cybersecurity incident response recommendations and considerations into their...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
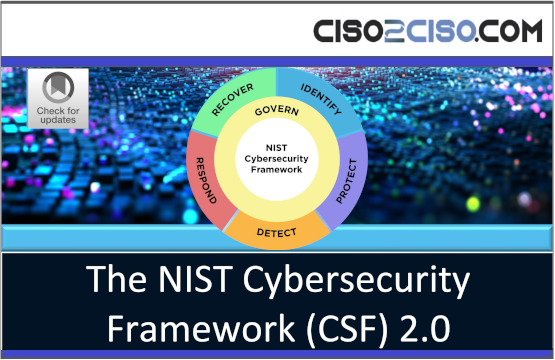
NIST CSF 2.0
The NIST Cybersecurity Framework (CSF) 2.0 provides guidance to industry, government agencies, and organizations of all...
What you need to know about NIST CSF 2.0 The proposed changes to the NIST Cybersecurity...
Draft & Implementation Examples The NIST Cybersecurity Framework is a technical guide for organisations to improve...