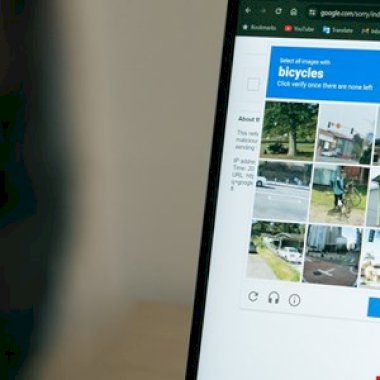
Source: www.infosecurity-magazine.com - Author: HP's latest Threat Insights Report has revealed a surge in malicious CAPTCHA...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Infosecurity Magazine
FishMonger APT Group Linked to I-SOON in Espionage Campaigns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com - Author: A Chinese cyber-espionage group known as FishMonger has been directly linked to...
Source: www.infosecurity-magazine.com - Author: A new analysis of mobile security threats by Zimperium has revealed that...
Source: www.infosecurity-magazine.com - Author: The leadership team at UK-based cyber consultancy Bridewell has raised concerns about...
Source: www.infosecurity-magazine.com - Author: British law enforcers are celebrating a major haul after arresting hundreds and...
Over Half a Million Hit by Pennsylvania Schools Union Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com - Author: More than half a million current and former members of the Pennsylvania...
Source: www.infosecurity-magazine.com - Author: The UK’s National Cyber Security Centre (NCSC) has urged organizations to completely...
Windows Shortcut Flaw Exploited by 11 State-Sponsored Groups – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com - Author: Written by A newly discovered cyber vulnerability, ZDI-CAN-25373, has been actively exploited...
Source: www.infosecurity-magazine.com - Author: A surge in browser-based phishing attacks has been recorded over the past...
Source: www.infosecurity-magazine.com - Author: World-renowned physicist, Professor Brian Cox, has been announced as a keynote speaker...
Source: www.infosecurity-magazine.com - Author: The US Cybersecurity and Infrastructure Security Agency (CISA) has confirmed that a...
Source: www.infosecurity-magazine.com - Author: Written by Security firm Barracuda has reported over a million phishing-as-a-service (PhaaS)...
Source: www.infosecurity-magazine.com - Author: Within two years, AI agents will accelerate the time it takes threat...
Source: www.infosecurity-magazine.com - Author: Digital and AI technologies are enabling “hybrid” threat actors from Russia and...
Source: www.infosecurity-magazine.com - Author: A cyber threat intelligence researcher at Cato Networks has discovered a new...
Source: www.infosecurity-magazine.com - Author: A new report from cybersecurity experts at Specops has revealed the most...
Source: www.infosecurity-magazine.com - Author: A newly leaked trove of internal chat logs has exposed potential connections...
Source: www.infosecurity-magazine.com - Author: Google has announced its intent to acquire Wiz, an Israeli-founded cloud security...
Source: www.infosecurity-magazine.com - Author: The volume of data breaches grew 6% year-on-year (YoY) in 2024, fueled...
Source: www.infosecurity-magazine.com - Author: A large-scale ad fraud campaign has resulted in more than 60 million...
Source: www.infosecurity-magazine.com - Author: UK companies have larger, more complex and more exposed digital supply chains...
Source: www.infosecurity-magazine.com - Author: Read more about Apple's UK backdoor court battle: Experts Dismayed at UK’s...
Source: www.infosecurity-magazine.com - Author: UK social media and email account compromises surged by 57% in 2024,...
Source: www.infosecurity-magazine.com - Author: A global non-profit has launched a new mapping database designed to help...
Source: www.infosecurity-magazine.com - Author: Over 23,000 organizations unwittingly had their secrets exposed over the weekend after...
Source: www.infosecurity-magazine.com - Author: Venture capital (VC) funds flowed in their billions to cybersecurity startups in...
UK ICO Fires GDPR “Warning Shot” Over Use of Children’s Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com - Author: The UK’s data protection watchdog has warned that a new investigation into...
Source: www.infosecurity-magazine.com - Author: Several members of the ISACA London Chapter have raised their concerns over the...
Source: www.infosecurity-magazine.com - Author: Apple has released iOS 18.3.2 and iPadOS 18.3.2 to fix a critical...
Source: www.infosecurity-magazine.com - Author: The US Cybersecurity and Infrastructure Agency (CISA) is undergoing significant changes under...