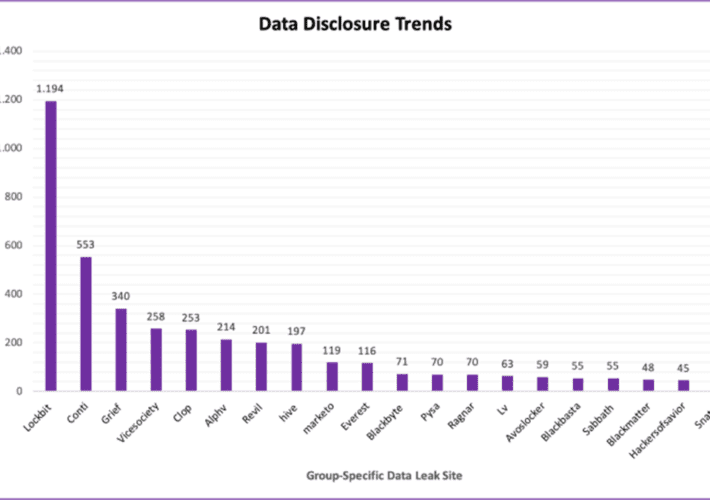
Twilio Hackers Scarf 10K Okta Credentials in Sprawling Supply Chain Attack The “0ktapus” cyberattackers set up...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
DARKReading
Efficient ‘MagicWeb’ Malware Subverts AD FS Authentication, Microsoft Warns The Russia-backed Nobelium APT has pioneered a...
CISA: Just-Disclosed Palo Alto Networks Firewall Bug Under Active Exploit The bug tracked as CVE-2022-0028 allows...
Efficient ‘MagicWeb’ Malware Subverts AD FS Authentication, Microsoft Warns The Russia-backed Nobelium APT has pioneered a...
Mudge Blows Whistle on Alleged Twitter Security Nightmare Lawmakers and cybersecurity insiders are reacting to a...
Thoma Bravo Buying Spree Highlights Hot Investor Interest in IAM Market M&A activity in the identity...
DevSecOps Gains Traction — but Security Still Lags Almost half of teams develop and deploy software...
Cybersecurity Solutions Must Evolve, Says Netography CEO Just as cyber criminals change tactics and strategy for...
State-Sponsored APTs Dangle Job Opps to Lure In Spy Victims APTs continue to exploit the dynamic...
Patch Now: 2 Apple Zero-Days Exploited in Wild The fact that the flaws enable remote code...
NIST Weighs in on AI Risk NIST is developing the AI Risk Management Framework and a...
Intel Adds New Circuit to Chips to Ward Off Motherboard Exploits The countermeasure, which compares the...
Banyan Recommends Phased Approach When Introducing Zero Trust Banyan Security’s Jayanth Gummaraju makes the case for...
DeepSurface Adds Risk-Based Approach to Vulnerability Management DeepSurface’s Tim Morgan explains how network complexity and cloud...
The HEAT Is On, Says Menlo Security Neko Papez, senior manager, cybersecurity strategy for Menlo Security,...
PIXM: Stopping Targeted Phishing Attacks With ‘Computer Vision’ Chris Cleveland, founder of PIXM, talks about phishers’...
Mimecast: Mitigating Risk Across a Complex Threat Landscape Garret O’Hara of Mimecast discusses how companies can...
Google Chrome Zero-Day Found Exploited in the Wild The high-severity security vulnerability (CVE-2022-2856) is due to...
Google Cloud Adds Curated Detection to Chronicle The curated detection feature for Chronicle SecOps Suite provides...
Patch Madness: Vendor Bug Advisories Are Broken, So Broken Dustin Childs and Brian Gorenc of ZDI...
Cybercriminals Weaponizing Ransomware Data for BEC Attacks Attacked once, victimized multiple times: Data marketplaces are making...
How and Why to Apply OSINT to Protect the Enterprise Here’s how to flip the tide...
Patch Madness: Vendor Bug Advisories Are Broken, So Broken Duston Childs and Brian Gorenc of ZDI...
Microsoft: We Don’t Want to Zero-Day Our Customers The head of Microsoft’s Security Response Center defends...
How to Clear Security Obstacles and Achieve Cloud Nirvana Back-end complexity of cloud computing means there’s...
Novel Ransomware Comes to the Sophisticated SOVA Android Banking Trojan Unusually, SOVA, which targets US users,...
Software Supply Chain Chalks Up a Security Win With New Crypto Effort GitHub, the owner of...
Microsoft Patches Zero-Day Actively Exploited in the Wild The computing giant issued a massive Patch Tuesday...
Software Development Pipelines Offer Cybercriminals ‘Free-Range’ Access to Cloud, On-Prem A Q&A with NCC Group’s Viktor...
Looking Back at 25 Years of Black Hat The Black Hat USA conference’s silver jubilee is...