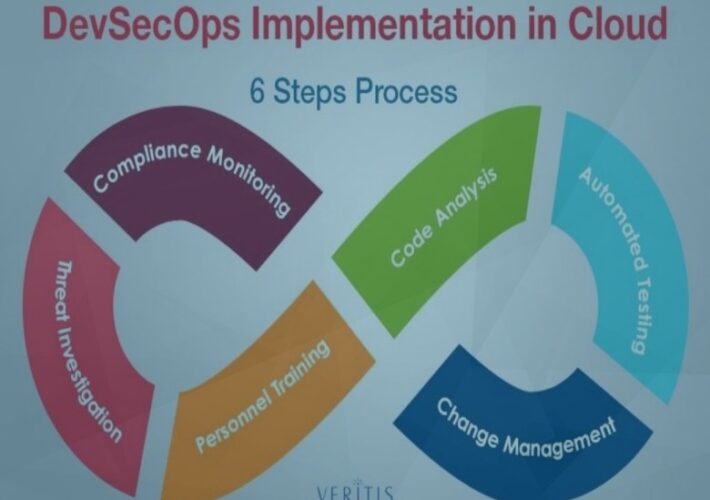
Source: www.cyberdefensemagazine.com - Author: News team Different Types of Risk Exposure and Best Practices for Protecting...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
cyberdefense magazine
Source: www.cyberdefensemagazine.com - Author: Stevin By Stan Vitek, Resident Geopolitical Analyst, Cyfirma Introduction As Israel’s military...
Source: www.cyberdefensemagazine.com - Author: Stevin Diving into a new sophisticated campaign, exploiting Microsoft’s Open Redirect vulnerability...
Source: www.cyberdefensemagazine.com - Author: Stevin By Adam Bennett, CEO, Red Piranha Red Piranha is Australia’s leading...
Source: www.cyberdefensemagazine.com - Author: News team By Laurent Halimi, Founder, Cyberr In the wake of 4...
Source: www.cyberdefensemagazine.com - Author: News team By Tom Tovar, Co-creator and CEO of Appdome There’s a...
Source: www.cyberdefensemagazine.com - Author: News team The critical role end-user experience plays in organizational security By...
Source: www.cyberdefensemagazine.com - Author: Gary It’s been an amazing journey and we are so thankful to...
Source: www.cyberdefensemagazine.com - Author: News team Adversarial Cyber Exercises Are The New Mandate By Stephen Gates,...
Source: www.cyberdefensemagazine.com - Author: News team Harnessing the Power of AI for Advanced Cyber Threat Intelligence...
Source: www.cyberdefensemagazine.com - Author: Stevin By Jyoti Bansal, CEO and Co-Founder, Traceable AI In the dynamic...
Source: www.cyberdefensemagazine.com - Author: Stevin By Milica D. Djekic There are a plenty of methods to...
Source: www.cyberdefensemagazine.com - Author: Stevin By Ken Westin, Field CISO, Panther Labs This week at the...
Source: www.cyberdefensemagazine.com - Author: Stevin Evaluate your needs and prioritize solutions that offer open integration and...
Source: www.cyberdefensemagazine.com - Author: Stevin Trends to Look Out for in 2024 By Yashin Manraj, CEO,...
Source: www.cyberdefensemagazine.com - Author: Stevin By Sagie Dulce, VP Research, Zero Networks A Brief History of...
Source: www.cyberdefensemagazine.com - Author: News team By Craig Burland, CISO, Inversion6 In the dynamic and unpredictable...
Source: www.cyberdefensemagazine.com - Author: News team By Dwayne McDaniel, GitGuardian Developer and Security Advocate, GitGuardian The...
Source: www.cyberdefensemagazine.com - Author: Stevin By Alex Serdiuk, CEO, Respeecher Newer and more impactful technological advancements...
Source: www.cyberdefensemagazine.com - Author: Stevin Navigating Access and Security in the Stolen Credentials Landscape By Tom...
Source: www.cyberdefensemagazine.com - Author: Gary In an alarming revelation, officials from the Minnesota-based UnitedHealth Group disclosed...
Source: www.cyberdefensemagazine.com - Author: Stevin By Nick France, CTO at Cybersecurity Leader Sectigo Given the fact...
Source: www.cyberdefensemagazine.com - Author: Stevin Thanks to AI, phishing attacks are better than ever. So is...
Source: www.cyberdefensemagazine.com - Author: Stevin By Rigo Van den Broeck, Executive Vice President, Cyber Security Product...
Source: www.cyberdefensemagazine.com - Author: Stevin By Roger Spears, Schneider Downs Whenever the new year rolls around,...
Source: www.cyberdefensemagazine.com - Author: Gary Nick Shevelyov, Senior Executive Reporter, Cyber Defense Magazine On February 7,...
Source: www.cyberdefensemagazine.com - Author: News team By Charlie Thomas, CEO, Deepwatch The ever-increasing volume of security...
Source: www.cyberdefensemagazine.com - Author: Stevin How Biographic and Biometric Information Work as a Team to Solve...
Source: www.cyberdefensemagazine.com - Author: Gary by Lena Allen Introduction In this era of unprecedented technological interconnectedness,...
Source: www.cyberdefensemagazine.com - Author: Stevin How to start ahead of the curve? By Vishakha Sadhwani, Customer...