Source: www.cyberdefensemagazine.com - Author: News team On July 1st, 2024, the cybersecurity community was rocked by...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
cyberdefense magazine
Source: www.cyberdefensemagazine.com - Author: News team Federal agencies face a pivotal cybersecurity challenge: prevent unauthorized entities...
Source: www.cyberdefensemagazine.com - Author: Stevin Integrated Governance, Risk, and Compliance Is Critical Business executives in all...
Source: www.cyberdefensemagazine.com - Author: News team Artificial Intelligence (AI) is transforming multiple sectors, driving innovation and...
Source: www.cyberdefensemagazine.com - Author: Stevin In today’s digital landscape, data security and privacy have become top...
Worried about Insider Risk? Pay More Attention to Offboarding – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com - Author: News team Discussions of insider risk inevitably conjure images of disgruntled IT...
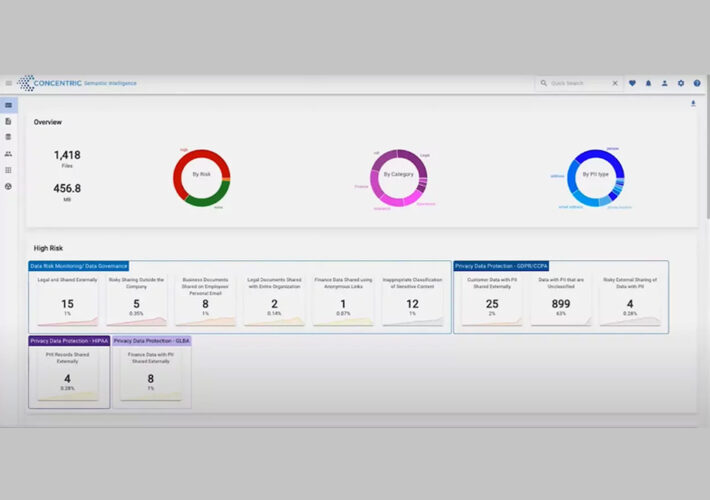
Source: www.cyberdefensemagazine.com - Author: Nick It’s not enough for companies to just discover and monitor sensitive...
Source: www.cyberdefensemagazine.com - Author: News team It is a tale almost as old as time: users...
Source: www.cyberdefensemagazine.com - Author: News team One of the recurring questions we hear from network security...
Source: www.cyberdefensemagazine.com - Author: News team By Nadav Czerninski, Co-founder and CEO, Oligo Security AI has...
Source: www.cyberdefensemagazine.com - Author: News team Diversity Cyber Council Initiative By Donna Segura, Publicist: OleanderPR In...
Source: www.cyberdefensemagazine.com - Author: News team By Angel Vossough, Co-Founder & CEO of BetterAI.io Cybersecurity defenses...
Source: www.cyberdefensemagazine.com - Author: News team Overview of best password generators to secure online accounts By...
Source: www.cyberdefensemagazine.com - Author: News team By Theresa Le, Chief Claims Officer, Cowbell As cyber threats...
Source: www.cyberdefensemagazine.com - Author: News team By Guillermo Gomez, Vice President of Endpoint Product, WatchGuard Technologies...
Source: www.cyberdefensemagazine.com - Author: News team Empowering the Human Firewall: The Bedrock of Cyber Defense By...
Source: www.cyberdefensemagazine.com - Author: News team By Rob Scott, Chief Innovator – Monjur The modern digital...
Source: www.cyberdefensemagazine.com - Author: News team By Stephen de Vries, CEO, IriusRisk In 2023, we saw...
Source: www.cyberdefensemagazine.com - Author: News team Don’t Settle for Less | Make an Informed Decision By...
Source: www.cyberdefensemagazine.com - Author: News team By Nissim Ben-Saadon, Director of Innovation, CYREBRO In today’s digital...
Source: www.cyberdefensemagazine.com - Author: News team By Kimberly Sutherland, vice president, fraud and identity strategy, LexisNexis®...
Source: www.cyberdefensemagazine.com - Author: News team Planning Beyond an Enterprise Security Posture and Toward Reliable Business...
Source: www.cyberdefensemagazine.com - Author: Stevin By Shirley Salzman, CEO and Co-Founder, SeeMetrics As all eyes are...
Source: www.cyberdefensemagazine.com - Author: News team Government cybersecurity may get worse before it gets better. By...
Source: www.cyberdefensemagazine.com - Author: News team The underlying differences between hardware and software when implementing critical...
Source: www.cyberdefensemagazine.com - Author: News team Crises and challenges are a staple of the technology and...
Source: www.cyberdefensemagazine.com - Author: News team By Srinivasan CR, Executive Vice President-Cloud and Cybersecurity Services &...
Source: www.cyberdefensemagazine.com - Author: News team By Guy Rosefelt, Chief Product Officer, Sangfor Technologies In my...
Source: www.cyberdefensemagazine.com - Author: News team By Vivek Ramachandran, CEO & Founder, SquareX Gone are the...
Source: www.cyberdefensemagazine.com - Author: News team By Dr. Pragyansmita Nayak, Chief Data Scientist, Hitachi Vantara Federal...