The prevention-first approach for SOC that your team needs to adopt Alon Bar, Product Marketing, Threat...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Cyber Talk
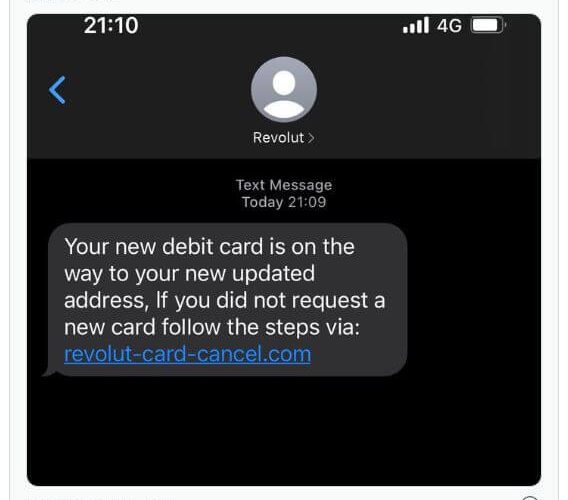
Revolut cyber attack exposes data belonging to thousands of customers EXECUTIVE SUMMARY: The London-based FinTech startup...
How to prevent sneaky zero day attacks on fleets of smartphones EXECUTIVE SUMMARY: Smartphones make us...
7 CISO succession planning best practices EXECUTIVE SUMMARY: Given the volume and complexity of security incidents,...
Becoming anti-fragile: Going beyond resilience to prevent ransomware Cindi Carter, Field CISO Americas, Check Point Software...
Warning of ransomware attacks on schools, here’s how to prepare… EXECUTIVE SUMMARY: Earlier today, US agencies...
14 ways to secure business data, in layman’s language Mazhar Hamayun is a cyber security professional...
Warning of ransomware attacks on schools, here’s how to prepare… EXECUTIVE SUMMARY: Earlier today, US agencies...
14 ways to secure business data, in layman’s language Mazhar Hamayun is a cyber security professional...
Credential phishing prevention best practices Credential phishing prevention best practices can help your employees prevent cyber...
The secret to managing deepfakes includes AI/DL & provenance Keely Wilkins is an Evangelist with the...
6 different types of CISOs and the environments they thrive in EXECUTIVE SUMMARY: The CISO’s role...
This is why securing critical infrastructure is so important Galina Antova is the co-founder and Chief...
17 incredible cloud native benefits that you should be aware of EXECUTIVE SUMMARY: Cloud native applications...
Top mobile security trends that you have to follow Augusto Morales is a Technology Lead (Threat...
6 different types of CISOs and the environments they thrive in EXECUTIVE SUMMARY: The CISO’s role...
6 different types of CISOs and the environments they thrive in EXECUTIVE SUMMARY: The CISO’s role...
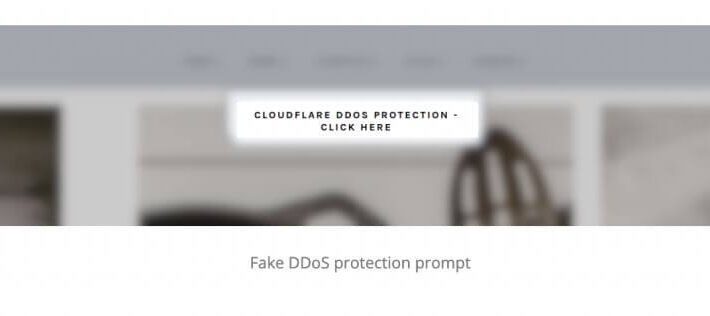
Fake DDoS pages on WordPress install the following… EXECUTIVE SUMMARY: WordPress-based sites hacked? Security researchers say...
UK claims the unenviable title of “Fraud Capital of Europe” By Gergo Varga, Evangelist, SEON. Plenty...
Zero Trust Segmentation: A primer for CISOs EXECUTIVE SUMMARY: CISOs and network managers need to know...
Ex-Twitter security chief alleges ‘egregious’ and ‘reckless’ practices EXECUTIVE SUMMARY: Twitter’s security poses a threat to...
Educating the world about email security one call at a time With over 20 years of...
Ex-Twitter security chief alleges ‘egregious’ and ‘reckless’ practices EXECUTIVE SUMMARY: Twitter’s security poses a threat to...
It’s never too early to start securing your startup Many startups find it difficult to strike...
What is a BISO? + everything else to know about the role EXECUTIVE SUMMARY: In 2020,...
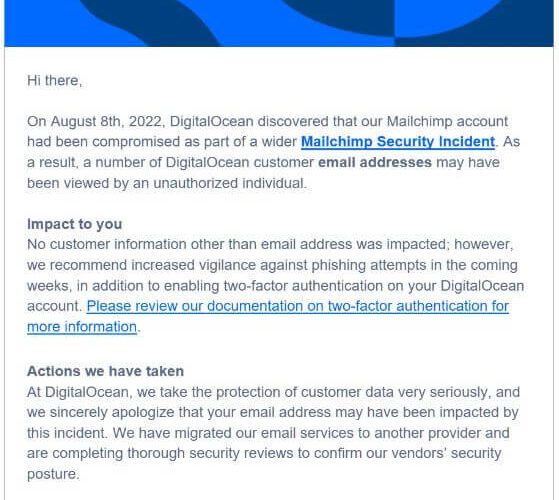
MailChimp breach exposes email addresses and Callback phishing EXECUTIVE SUMMARY: The cloud giant known as DigitalOcean...
Healthcare payer CISO shares real-world insights: Protecting healthcare data in the cloud In this interview, the...
Africa – the most cyber attacked continent, a 2022 review of trends Issam El Haddioui: Head...
Using automated release management to increase data security Devin Partida writes about cyber security and technology....
10 key facts about callback phishing attacks Is callback phishing on your radar screen? Hackers launch...