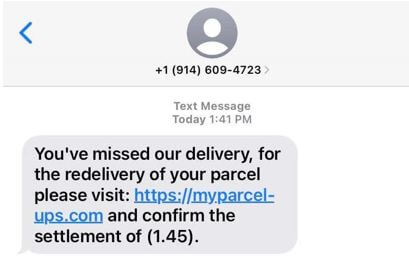
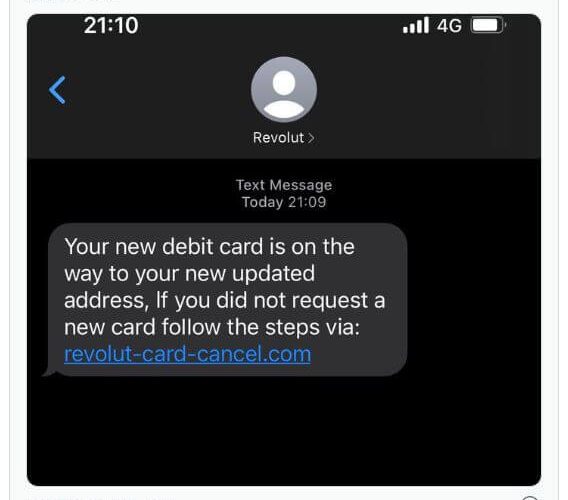
What C-Suite leaders should know to recognize phishing By Miguel Angulo, Channel Engineer and Evangelist, Check...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Cyber Talk
3 simple, strategic measures to stop phishing attacks EXECUTIVE SUMMARY: To celebrate Cyber Security Awareness Month,...
A global CISO’s secrets to high-performing security awareness initiatives Jonathan Fischbein is the Chief Information Security...
Security benefits of Hyperautomation Devin Partida writes about cyber security and technology. She is also the...
Single chip transfers the entire internet’s traffic in a second EXECUTIVE SUMMARY: A single chip has...
The art of cyber threat intelligence: How to identify & fight potential attackers Dave is an...
How to become a revenue-generating CIO EXECUTIVE SUMMARY: Businesses are increasingly looking to IT leaders as...
Addressing the cyber security talent shortage: APAC and beyond EXECUTIVE SUMMARY: Globally, in the last year,...
Click or treat? Scary good security tips for a happy Halloween! EXECUTIVE SUMMARY: Halloween is a...
SMiShing: Short, sweet and evil By Miguel Angulo, Channel Engineer and Evangelist, Check Point Software. Have...
Single chip transfers the entire internet’s traffic in a second EXECUTIVE SUMMARY: A single chip has...
Single chip transfers the entire internet’s traffic in a second EXECUTIVE SUMMARY: A single chip has...
Single chip transfers the entire internet’s traffic in a second EXECUTIVE SUMMARY: A single chip has...
Single chip transfers the entire internet’s traffic in a second EXECUTIVE SUMMARY: A single chip has...
8 essential ways to prevent ever-infuriating keyless car theft EXECUTIVE SUMMARY: The era of hotwiring cars...
8 mistakes CIOs make and how to avoid them From driving transformative change, to sharing insights...
Essential best practices: Securing critical national infrastructure By Deryck Mitchelson, Field CISO EMEA, Check Point Software...
American Airlines learns breach caused by phishing EXECUTIVE SUMMARY: The US airline, which reportedly owns the...
How hardware impacts cyber security By Zac Amos, Features Editor, Rehack.com. Cyber security has been an important...
Adware installed 13 million times + how to uninstall it EXECUTIVE SUMMARY: Cyber security researchers have...
Hacker breaches Fast Company, sending offensive notifications EXECUTIVE SUMMARY: The business publication known as Fast Company...
Remote work security statistics in 2022 By Pete Nicoletti, Field CISO Americas, Check Point Software. After...
American Airlines learns breach caused by phishing EXECUTIVE SUMMARY: The US airline, which reportedly owns the...
8 mistakes CIOs make and how to avoid them From driving transformative change, to sharing insights...
8 mistakes CIOs make and how to avoid them From driving transformative change, to sharing insights...
8 mistakes CIOs make and how to avoid them From driving transformative change, to sharing insights...
Did hackers gain full access to Uber’s critical IT systems? EXECUTIVE SUMMARY: Last week, Uber Technologies...
The prevention-first approach for SOC that your team needs to adopt Alon Bar, Product Marketing, Threat...
Revolut cyber attack exposes data belonging to thousands of customers EXECUTIVE SUMMARY: The London-based FinTech startup...
Did hackers gain full access to Uber’s critical IT systems? EXECUTIVE SUMMARY: Last week, Uber Technologies...