Three FIFA World Cup Scams You Should Know Contributed by George Mack, Content Marketing Manager, Check...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Cyber Talk
Are we at a tipping point when it comes to data loss? By Deryck Mitchelson, Field...
As a technology leader, Celebrate National Computer Security Day! EXECUTIVE SUMMARY: As a technology leader, you...
A Q&A with Mimi Keshani, COO and Co-Founder of Hadean Mimi Keshani is Hadean’s COO, driving its pioneering work in...
Canada advances cyber security via Indo-Pacific Strategy EXECUTIVE SUMMARY: On Sunday, Canada launched its much-anticipated Indo-Pacific...
6 simple & straightforward Cyber Monday fraud prevention tips EXECUTIVE SUMMARY: Starting on November 28th, Cyber...
27 expert cyber security predictions for 2023 that will help prevent attacks EXECUTIVE SUMMARY: In the...
One easy way to secure your Android Contributed by George Mack, Content Marketing Manager, Check Point...
What is purple teaming and why is it useful? EXECUTIVE SUMMARY: Networks are under attack and...
Harris Center ISO perspective: Product evaluation, board engagement & career advice In this interview, Wes Farris,...
Ransomware attack on CommonSpirit Health could affect 20 million Americans Hackers are targeting the healthcare industry....
Beware of these Black Friday scams that could spoil your holiday season EXECUTIVE SUMMARY: Black Friday...
A CISO’s 100-day run to cyber success Check Point Software’s cyber security evangelist Ashwin Ram shares...
Ransomware attack on CommonSpirit Health could affect 20 million Americans Hackers are targeting the healthcare industry....
6 ways to keep your employees safe online in 2022 By Anas Baig. With the increase...
Top 5 email newsletters that will make you smarter in the digital age Contributed by George...
The Harris Center for Mental Health & IDD ISO shares perspectives on cyber security Wes Farris...
What are eavesdropping attacks? Everything you need to know EXECUTIVE SUMMARY: Eavesdropping attacks are easy to...
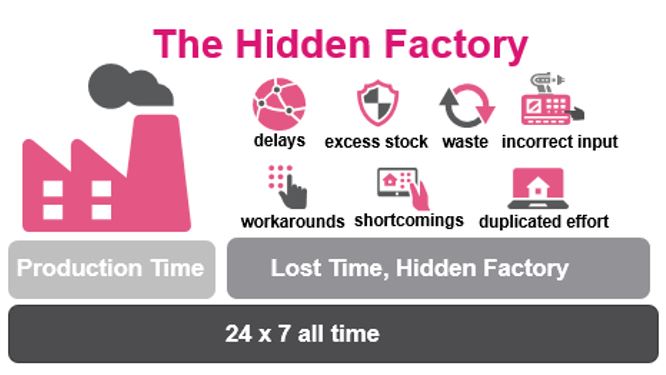
How addressing “Hidden Factory” can boost the transition to “Green Factory” Antoinette Hodes is a Check...
10 secrets for successful digital transformations EXECUTIVE SUMMARY: Digitize to survive and thrive? Digital transformations account...
What are eavesdropping attacks? Everything you need to know EXECUTIVE SUMMARY: Eavesdropping attacks are easy to...
What are eavesdropping attacks? Everything you need to know EXECUTIVE SUMMARY: Eavesdropping attacks are easy to...
Maple Leaf Foods confirms outage due to cyber security incident EXECUTIVE SUMMARY: After discovering the breach,...
New ransomware tactics include intermittent encryption, IABs By Zac Amos, Features Editor, Rehack.com. Ransomware is evolving with...
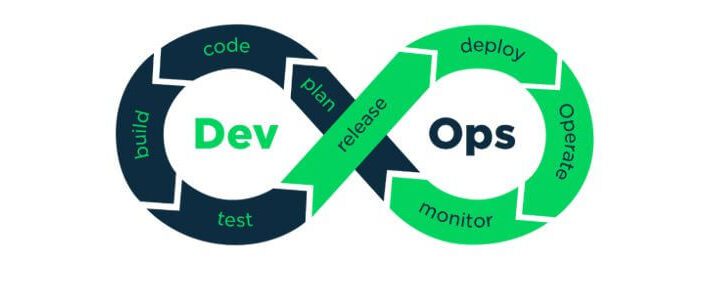
The trendiest buzzword in cyber security right now… EXECUTIVE SUMMARY: Moving to a more agile and...
Key challenges of shift-left tactics By Musa Nadir Sani. Software development has continued to evolve over...
New Microsoft Teams update, you can ‘assign seats’ in meetings EXECUTIVE SUMMARY: Together Mode is an...
Supply chain attack on U.S. news websites EXECUTIVE SUMMARY: Due to a supply chain attack involving...
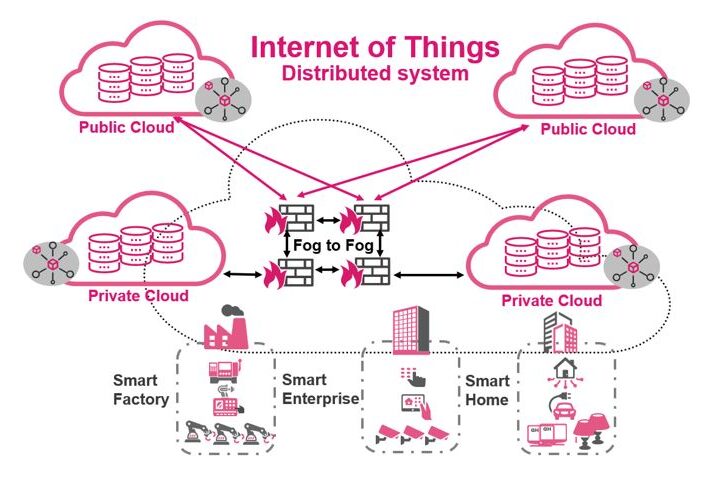
Challenges of the monolithic and distributed IoT realms Antoinette Hodes is a Check Point Solutions Architect...
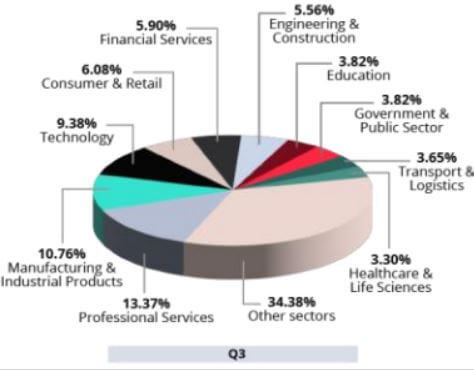
For $4M, hackers buy access to corporate networks; possibly yours EXECUTIVE SUMMARY: Cyber criminals are selling...