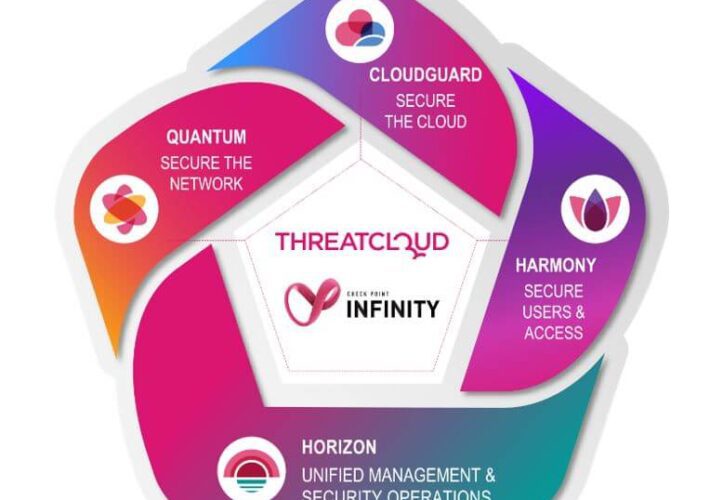
Dangerous cyber threats you should expect in 2023 Contributed by George Mack, Content Marketing Manager, Check...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Cyber Talk
Building powerful security into the fragmented IoT ecosystem EXECUTIVE SUMMARY: Organizations are rapidly adopting connected technologies...
5 essentials for boards to drive cyber readiness Check Point Software’s cyber security evangelist Ashwin Ram...
Uber’s latest data breach reveals how to improve third-party security… EXECUTIVE SUMMARY: In Uber’s latest data...
A tell-all conversation: The biggest cloud security trends, challenges & solutions EXECUTIVE SUMMARY: In this dynamic...
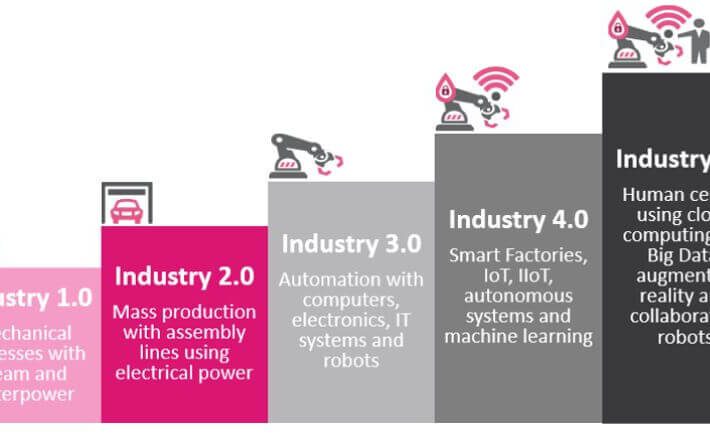
Bringing back the human in technology with Industry 5.0 By Antoinette Hodes, Check Point Solutions Architect...
CPX 360 2023: The most important cyber security event of the year! EXECUTIVE SUMMARY: The premiere...
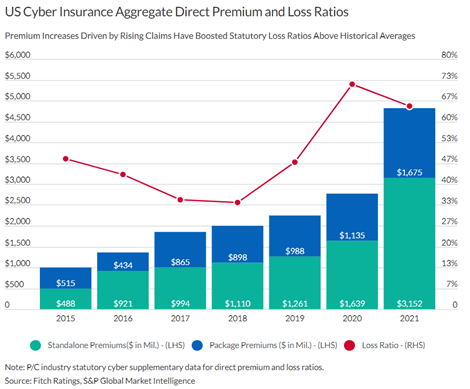
A prevention-first security strategy reduces insurance claims Keely Wilkins is an Evangelist with the Office of...
7 noteworthy ransomware predictions for the new year Get expert ransomware predictions for 2023, and say...
AppMap CEO on building ‘Google Maps for developers’ Elizabeth Lawler is the co-founder and CEO of...
4 CISO perspectives on the future of cyber security EXECUTIVE SUMMARY: As a decision-maker, discover cyber...
Promoting cyber security growth in a recession By Devin Partida, Editor-in-Chief, Rehack.com. The COVID-19 pandemic has...
A CIO’s role in sustainability and pursuing ESG goals EXECUTIVE SUMMARY: Putting people and the planet...
A tell-all conversation: The biggest cloud security trends, challenges & solutions EXECUTIVE SUMMARY: In this dynamic...
A tell-all conversation: The biggest cloud security trends, challenges & solutions EXECUTIVE SUMMARY: In this dynamic...
A tell-all conversation: The biggest cloud security trends, challenges & solutions EXECUTIVE SUMMARY: In this dynamic...
15 seasonal cyber security shopping tips, keep your celebrations bright EXECUTIVE SUMMARY: Many people are eager...
CISO Pete Nicoletti on first-of-their-kind operational necessities for SMBs By Pete Nicoletti, Field CISO, Americas. Pete has...
The Microsoft Teams chat integration into Outlook EXECUTIVE SUMMARY: What would it be like if Microsoft...
(Re) thinking about cyber security in terms of risk management By Tom Boltman, VP of Strategic...
15 seasonal cyber security shopping tips, keep your celebrations bright EXECUTIVE SUMMARY: Many people are eager...
7 step checklist to avoid common cloud security misconfigurations EXECUTIVE SUMMARY: Cloud computing provides a flexible...
Top AWS cloud security tips to secure your environment EXECUTIVE SUMMARY: Remember when CodeSpaces was forced...
How to boost healthcare cyber security in 2023 Contributed by George Mack, Content Marketing Manager, Check...
25+ cyber security experts, driving the security conversation… EXECUTIVE SUMMARY: In cyber security, change is always...
Perspectives from the field: Optimizing your cloud security Konstantina Koukou is a well-rounded, tech-savvy electrical engineering...
Is cloud native security good enough? By Deryck Mitchelson, Field CISO EMEA, Check Point Software Technologies....
Artificial intelligence driving high-performance cloud security transformations EXECUTIVE SUMMARY: Migrating to the cloud can afford organizations...
As a technology leader, Celebrate National Computer Security Day! EXECUTIVE SUMMARY: As a technology leader, you...
How to reduce industrial cyber attacks during cloud transformation Contributed by April Miller, Senior Writer for...