In the United States, there is no national, statutory, cross-sector minimum standard for information security. No...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Center for Internet Security
Enterprises looking to implement cyber defenses wish to know three things: Which protections will we start...
Enterprises looking to implement cyber defenses wish to know three things: Which protections will we start...
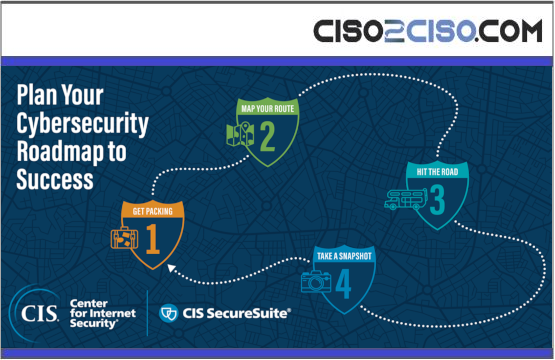
Data breaches happen when we treat cybersecurity as a destination. If we believe security is complete,...
Argon (now part of Aqua Security) approached the Center for Internet Security (CIS) with theidea of...