Source: www.bleepingcomputer.com – Author: Bill Toulas

A new campaign distributing the RomCom backdoor malware is impersonating the websites of well-known or fictional software, tricking users into downloading and launching malicious installers.
The latest campaign was uncovered by Trend Micro, who have followed RomCom since the summer of 2022. The researchers report that the threat actors behind the malware have escalated its evasion by using payload encryption and obfuscation and expanded the tool’s capabilities by introducing new and powerful commands.
Most websites used for distributing RomCom to victims concern remote desktop management applications, which increases the likelihood of attackers employing phishing or social engineering to approach their targets.
RomCom linked to Cuba ransomware
The first documented use of RomCom was reported in August 2022 by Palo Alto Networks, attributing the attacks to a Cuba ransomware affiliate they named ‘Tropical Scorpius.’ Trend Micro uses ‘Void Rabisu’ to track the same actor.
In October 2022, Ukraine’s CERT-UA reported that the RomCom malware was being used in attacks against critical networks in the country.
Another report published almost simultaneously by BlackBerry claimed the association with Cuba ransomware but confirmed the attacks in Ukraine while also indicating there were malware victims in the United States, Brazil, and the Philippines.
A subsequent BlackBerry report in November 2022 illustrated how RomCom impersonated legitimate software, including SolarWinds Network Performance Monitor (NPM), the KeePass password manager, and PDF Reader Pro.
The current campaign
Trend Micro’s report on the latest RomCom activity lists several examples of websites used by the malware operators between December 2022 and April 2023 that impersonate legitimate software, like Gimp, Go To Meeting, ChatGPT, WinDirStat, AstraChat, System Ninja, Devolutions’ Remote Desktop Manager, and more.
Some of the malicious sites used in the said time period are:
- gllmp.com (offline) – Impersonates the free and open-source image editor
- gotomeet.us (offline) – Impersonates the cloud video meeting and conferencing app
- singularlabs.org (offline) – Impersonates a PC-cleaning tool
- chatgpt4beta.com (online) – Impersonates the AI-powered chatbot platform
- astrachats.com (offline) – Impersonates the secure chat software
- devolutionrdp.com (online) – Impersonates a remote desktop management tool
- cozy-sofware.com (offline) – Impersonates a remote desktop management tool
- vectordmanagesoft.com (offline) – Impersonates a remote desktop management tool
- devolrdm.com (online) – Impersonates a remote desktop management tool
- dirwinstat.com (online) – Impersonates a disk usage viewer and cleanup tool
These fake sites are promoted through Google advertisements and highly targeted phishing emails, with most of the victims based in Eastern Europe.
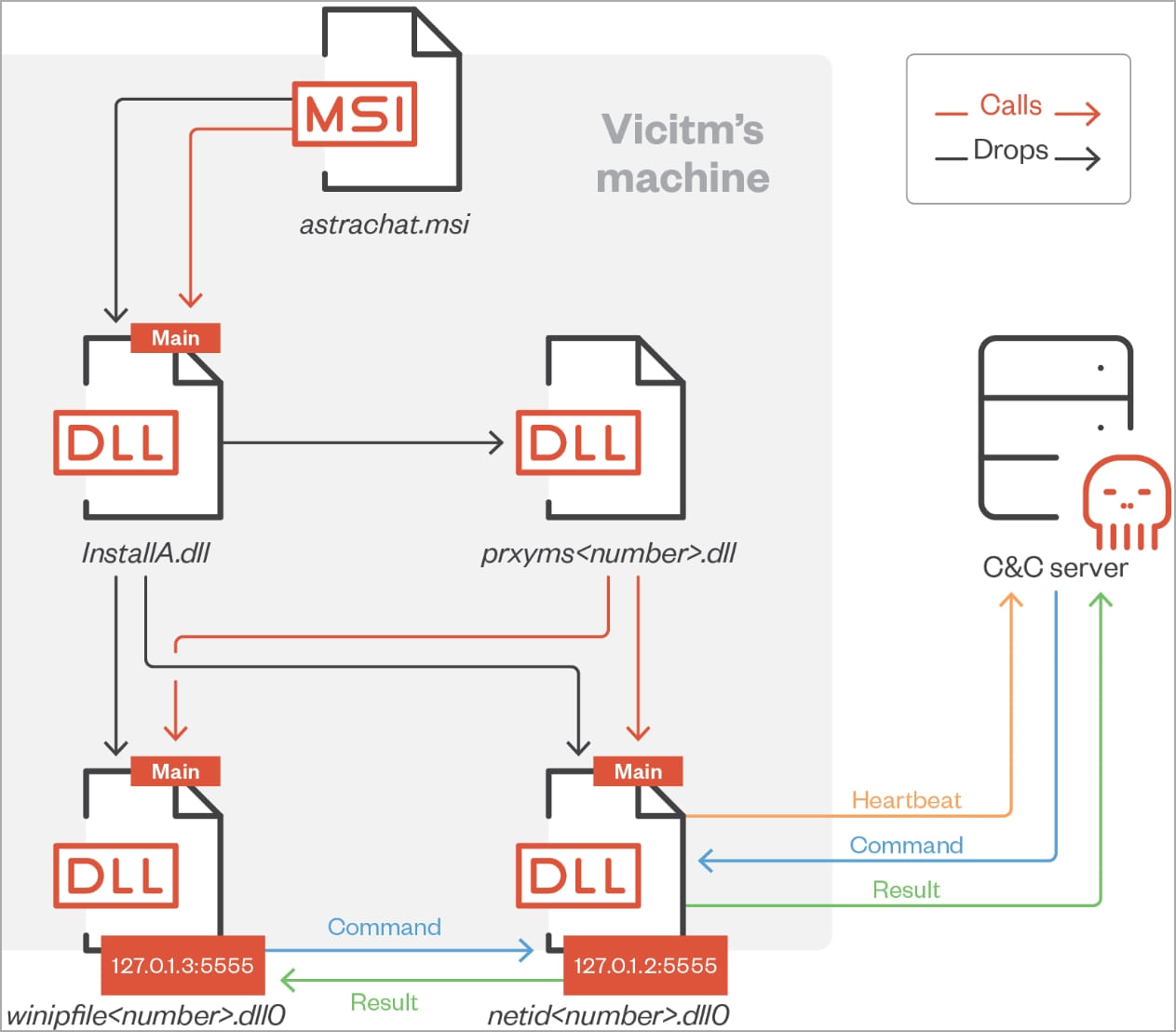
The websites distribute MSI installers that impersonate the promised app but are trojanized with a malicious DLL file (“InstallA.dll”).
This file extracts another three DLLs onto the victim’s %PUBLIC%Libraries folder, which handles command and controll server communications and command execution.
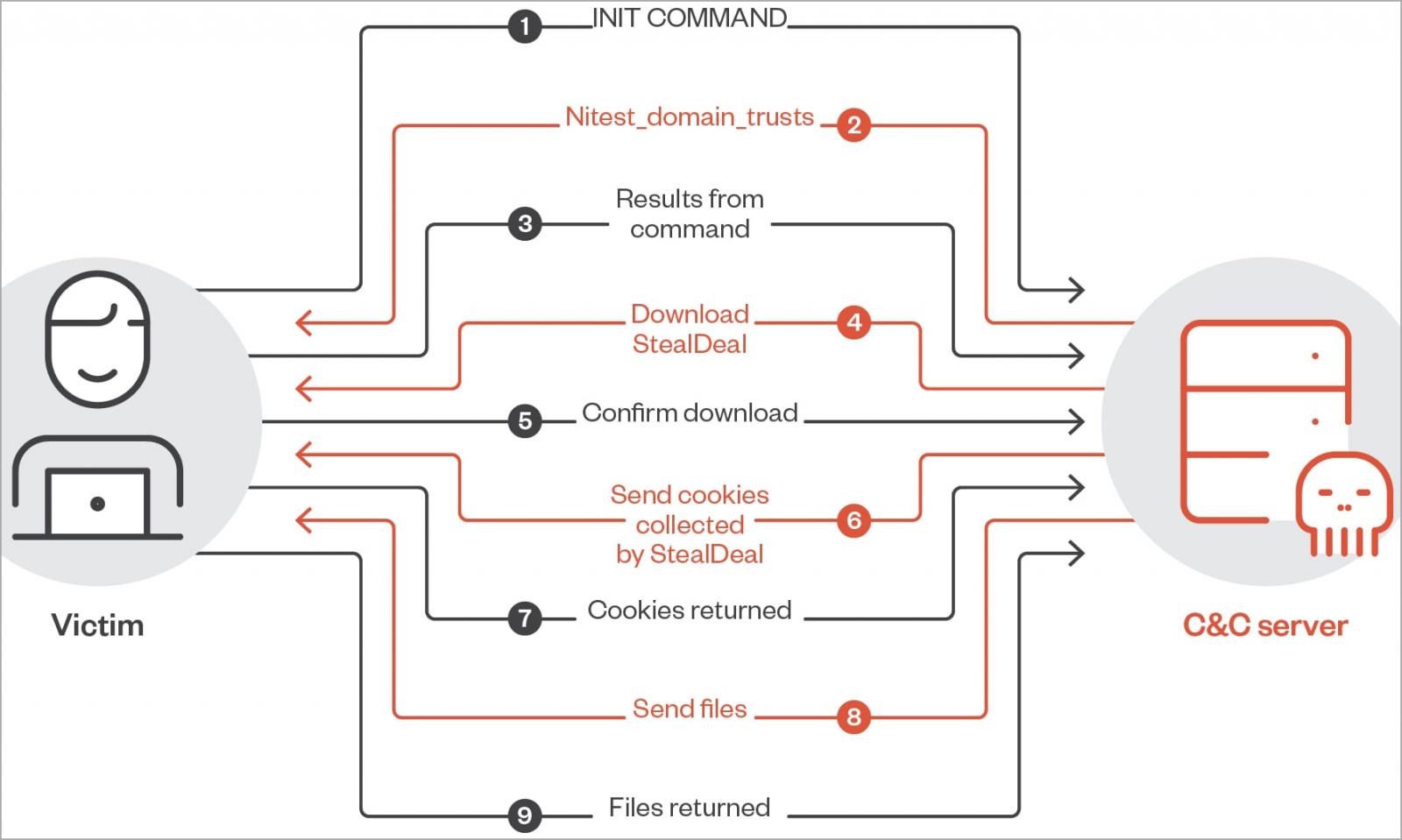
The latest version of the RomCom payload analyzed by Trend Micro shows that its authors have worked towards implementing additional malicious commands, with their number of commands growing from 20 to 42.
Some of the highlighted commands that can be pushed to a device infected with RomCom are:
- Start cmd.exe
- Drop a file onto the victim’s computer to introduce more payloads.
- Spawn a process with PID spoofing to make it appear legitimate.
- Exfiltrate data from the compromised system.
- Set up a proxy via SSH.
- Update the malware on the device.
- Run AnyDesk on a hidden window.
- Compress a given folder and send it to the attackers’ server.
These commands already give the attackers extensive capabilities, but the cybersecurity company reports having seen several cases of additional malware payloads being installed through RomCom.
Stealer components downloaded by RomCom on compromised devices include:
- PhotoDirector.dll – A screenshot-snapping tool that compresses images in ZIP archives for exfiltration.
- procsys.dll – A web browser (Chrome, Firefox, Edge) cookies stealer.
- wallet.exe – A cryptocurrency wallet stealer.
- msg.dll – An instant messenger chat stealer.
- FileInfo.dll – An FTP credentials stealer that uploads data to an FTP server.
Enhanced evasion
RomCom’s authors now use the VMProtect software for code protection and anti-VM capabilities. Also, it uses encryption for the payload, the key for which is not hard coded but fetched by an external address.
The malware uses null bytes in its C2 communication to evade detection from network monitoring tools.
Finally, the software downloaded from the malicious websites is signed by seemingly legitimate companies supposedly based in the U.S. and Canada, the websites of which are filled with fake or plagiarized content.
RomCom has been associated with ransomware, espionage, and warfare, and the exact goals of its operators remain murky. Whatever the case, it is a versatile threat that can cause significant damage.
Trend Micro has provided a comprehensive list of indicators of compromise (IoCs) for the latest RomCom campaign and Yara rules to help defenders detect and stop the attacks.
Original Post URL: https://www.bleepingcomputer.com/news/security/romcom-malware-spread-via-google-ads-for-chatgpt-gimp-more/
Category & Tags: Security – Security
Views: 0




















































