Guidance for securing networks continues to evolve as adversaries exploit new vulnerabilities, new security features are implemented, and new methods of securing devices are identified. Improper configurations, incorrect handling of configurations, and weak encryption keys can expose vulnerabilities in the entire network. All networks are at risk of compromise, especially if devices are not properly configured and maintained. An administrator’s role is critical to securing the network against adversarial techniques and requires dedicated people to secure the devices, applications, and information on the network.
This report presents best practices for overall network security and protection of individual network devices. It will assist administrators in preventing an adversary from exploiting their network. While the guidance presented here can be applied to many types of network devices, the National Security Agency (NSA) has provided sample commands for Cisco Internetwork Operating System (IOS) devices. These commands can be executed to implement recommended mitigations.
1.1 Regarding Zero Trust
Zero Trust is a security model, a set of system design principles, and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries. NSA fully supports the Zero Trust security model, and much of the guidance in this report can be applied at different boundaries as recommended in Zero Trust guidance. However, this report provides guidance to mitigate common vulnerabilities and weaknesses on existing networks. As system owners introduce new network designs intended to achieve more mature Zero Trust principles, this guide may need to be modified.
Network architecture and design
A secure network design that implements multiple defensive layers is critical to defend against threats and protect resources within the network. The design should follow security best practices and model Zero Trust principles, both for network perimeter and internal devices.
2.1 Install perimeter and internal defense devices
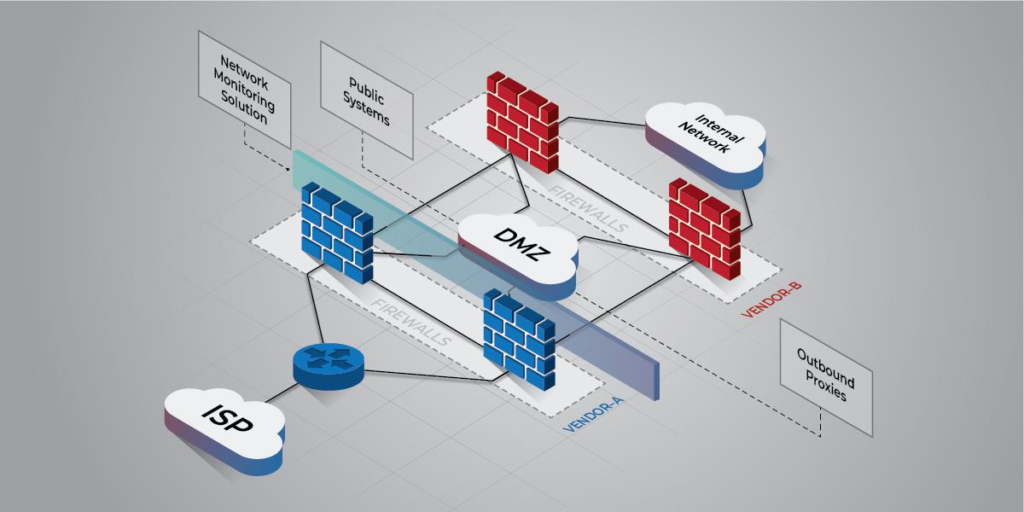
A network requires a substantial defensive strategy to protect individual components and the information they contain. Multiple layers of defense should be implemented at the network’s perimeter to protect against external threats, and to monitor and restrict inbound and outbound traffic.
NSA recommends configuring and installing security devices at the perimeter of the network according to security best practices:
- Install a border router to facilitate a connection to the external network, such as an Internet service provider (ISP).
- Implement multiple layers of next-generation firewalls throughout the network to restrict inbound traffic, restrict outbound traffic, and examine all internal activity between disparate network regions. Each layer should utilize different vendors to protect against an adversary exploiting the same unpatched vulnerability in an attempt to access the internal network.
- Place publicly accessible systems and outbound proxies in between the firewall layers in one or more demilitarized zone (DMZ) subnets, where access can be appropriately controlled between external devices, DMZ devices, and internal systems.
- Implement a network monitoring solution to log and track inbound and outbound traffic, such as a network intrusion detection system (NIDS), a traffic inspector, or a full-packet capture device.
- Deploy multiple dedicated remote log servers to enable activity correlation among devices and detection of lateral movement.
- Implement redundant devices in core areas to ensure availability, which can be load-balanced to increase network throughput and decrease latency.
Views: 19




















































