Source: heimdalsecurity.com – Author: Mihaela Marian
The hacking group known as APT37, also referred to as StarCruft, Reaper, or RedEyes, has employed a new malware called FadeStealer to steal information. This sophisticated malware incorporates a ‘wiretapping’ feature that enables the threat actors to eavesdrop on and record conversations through victims’ microphones.
About the Threat Group
APT37 is widely believed to be a state-sponsored hacking group operating in alignment with North Korean interests. With a lengthy history of conducting cyber espionage attacks, their targets primarily include North Korean defectors, educational institutions, and organizations based in the European Union.
Previously, APT37 utilized custom-made malware named Dolphin and M2RAT to carry out commands and steal data, credentials, and screenshots from Windows devices, including connected mobile phones.
A recent report from the AhnLab Security Emergency Response Center (ASEC) sheds light on the group’s latest tactics. Researchers have identified new custom malware called the ‘AblyGo backdoor’ and ‘FadeStealer,’ which APT37 employs in their espionage operations.
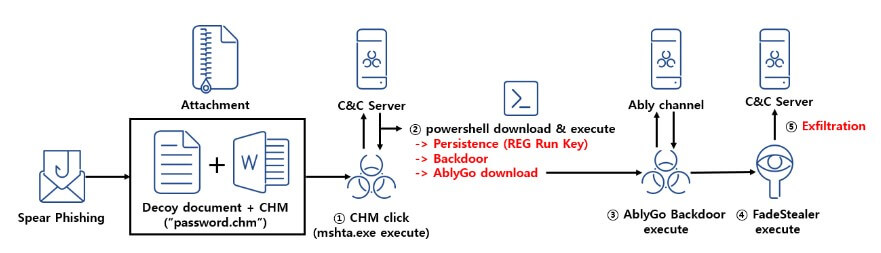
The Process
To deliver the malware, APT37 employs phishing emails that contain password-protected Word and Hangul Word Processor documents (.docx and .hwp files) as well as a Windows CHM file named ‘password.chm’ that is used as an archive. The recipient of the phishing email is instructed to open the CHM file to access the password for the documents, initiating the infection process.
Upon opening the CHM file, the user is presented with the purported password to unlock the document. Simultaneously, a remote PowerShell script is clandestinely downloaded and executed, acting as a backdoor with autostart registration on the Windows system.
Next, the PowerShell backdoor establishes communication with the attackers’ command and control servers and executes commands sent by them. Furthermore, it serves as a means to deploy an additional GoLang backdoor in the later stages of the attack. This secondary backdoor is referred to as the ‘AblyGo backdoor’ due to its utilization of the Ably Platform, an API service enabling developers to integrate real-time features and information delivery into their applications.
Ultimately, the deployed backdoors serve as a delivery mechanism for the ‘FadeStealer’ malware, the final payload. Once installed, FadeStealer injects itself into the legitimate ‘ieinstall.exe’ process of Internet Explorer using DLL sideloading. It proceeds to gather data, such as screenshots, logged keystrokes, files gathered from connected smartphones and removable devices, and even audio recordings from the connected microphone, storing it in RAR archives every 30 minutes. This allows the threat actors to eavesdrop on conversations. The collected data can then be analyzed in order to extract sensitive information for the North Korean government’s use.
It is worth noting that APT37 is not the sole North Korean threat actor exploiting CHM files to distribute malware. ASEC has also reported that the state-sponsored hacking group called Kimsuky utilizes CHM files in phishing attacks to deploy malicious scripts that steal user information and install additional malware.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/north-korean-apt37-exploits-new-fadestealer-malware/
Category & Tags: Cybersecurity News – Cybersecurity News
Views: 0




















































