EXECUTIVE SUMMARY:
Microsoft, the Health Information Sharing and Analysis Center (Health-ISAC) and other partners have announced a widespread technical and legal crackdown against servers hosting “cracked” copies of Cobalt Strike; a tool commonly deployed by cyber criminals to distribute malware, including ransomware.
The primary goal is to prevent hackers from continuing to use Cobalt Strike in ransomware attacks that target hospitals and healthcare groups. Ransomware attackers using cracked copies of Cobalt Strike have been linked to 68 hits on healthcare organizations in at least 19 countries. Attacks have disrupted critical patient care services, and exacted unnecessary financial tolls on organizations.
Cobalt Strike crackdown explained
The attacks have affected turn-around times for diagnostic, imaging and laboratory results. Attacks have also led to canceled medical procedures and delays in the delivery of chemotherapy treatments. In the long-run, these types of cyber attacks have negative impacts on hospitals and patients alike, and can increase mortality rates.
More critical information
On Friday March 31st, the U.S. District Court for the Eastern District of New York issued a court order permitting Microsoft and a partner organization to seize the domain names and to remove the IP addresses of servers hosting cracked versions of Cobalt Strike.
The malicious infrastructure will be removed from the internet with the help of relevant computer emergency readiness teams (CERTs) and internet service providers. Takedowns have already begun.
“Disrupting cracked legal copies of Cobalt Strike will significantly hinder the monetization of these illegal copies and slow their use in cyber attacks, forcing criminals to re-evaluate and change their tactics,” Amy Hogan-Burney, stated head of Microsoft’s Digital Crimes Unit (DCU).
How it happened
Previously known as Help Systems, Fortra released Cobalt Strike in 2012. The product was designed as a legitimate commercial pen testing tool for red teams, who would use it to scan infrastructure for vulnerabilities.
While the developer carefully screens customers and only provides licenses for lawful use, over time, malicious persons have obtained and distributed cracked versions of the software. In turn, Cobalt Strike has become a frequently used tool in ransomware and data theft-related cyber attacks.
Specifically, hackers use the tool for post-exploitation tasks after developing beacons designed to provide them with persistent remote access to compromised devices. This allows hackers to harvest sensitive data or proceed with further malicious payloads.
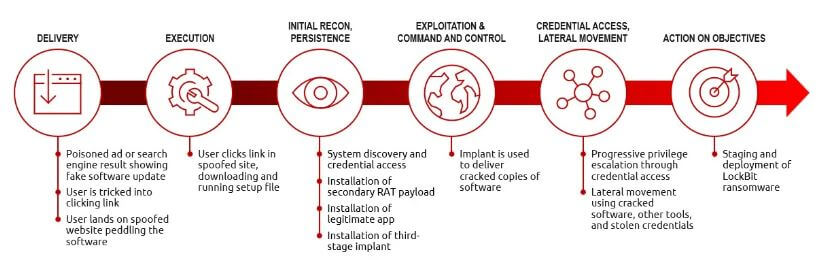
Malicious infrastructure
Microsoft has found malicious infrastructure hosting Cobalt Strike in every region of the globe, from China, to the United States, to Russia. While the exact identities of the criminals behind the operations remain unknown, two infamous Russian-speaking ransomware gangs, Conti and LockBit, are believed to be involved.
Microsoft has also observed several state-backed cyber attack groups using Cobalt Strike versions while serving the interests of foreign governments. The legal crackdown follows Google Cloud’s identification of 34 different hacked versions of the Cobalt Strike tool in the wild.
Microsoft takes on ‘sinkholing’ and more
In order to help prevent future related cyber attacks, Microsoft says that it’s going to pursue ‘sinkholing,’ meaning that it will redirect certain malicious domains to Microsoft so that the company can identify victims.
Microsoft has previously tapped civil orders to seize domains and IP addresses associated with specific malware, but the recent court order represents the first time where Redmond has attempted to take down a malicious hacking tool on such a massive scale.
In planning for tomorrow, Microsoft has already begun digging into the hacking tools that cyber criminals may turn to once Cobalt Strike becomes a non-option.
“…We are going to seek a permanent injunction because we believe this activity will continue…They [cyber criminals] will look to move hosting [sites] for the cracked versions of Cobalt Strike because it is an effective tool for them. And we will continue to chase them,” stated Hogan-Burney.
For more ransomware insights, please see CyberTalk.org’s past coverage. Lastly, to receive more cutting-edge cyber security news, best practices and analyses, please sign up for the CyberTalk.org newsletter.
Views: 4




















































